Quick filters:
Cyber war Stock Photos and Images
 Cyber war or cyber warfare military defense technology concept as missiles attacking with binary code. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-cyber-war-or-cyber-warfare-military-defense-technology-concept-as-136780141.html
Cyber war or cyber warfare military defense technology concept as missiles attacking with binary code. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-cyber-war-or-cyber-warfare-military-defense-technology-concept-as-136780141.htmlRFHXETD1–Cyber war or cyber warfare military defense technology concept as missiles attacking with binary code.
 Steinenberg, Basel, Switzerland - February 19th, 2018. Front view of a carnival group with the topic of cyber warfare Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-steinenberg-basel-switzerland-february-19th-2018-front-view-of-a-carnival-177423538.html
Steinenberg, Basel, Switzerland - February 19th, 2018. Front view of a carnival group with the topic of cyber warfare Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-steinenberg-basel-switzerland-february-19th-2018-front-view-of-a-carnival-177423538.htmlRMM8J9EX–Steinenberg, Basel, Switzerland - February 19th, 2018. Front view of a carnival group with the topic of cyber warfare
 Cyber army soldier Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-cyber-army-soldier-96324780.html
Cyber army soldier Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-cyber-army-soldier-96324780.htmlRFFGKY6M–Cyber army soldier
 CYBER WAR red Rubber Stamp over a white background. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-cyber-war-red-rubber-stamp-over-a-white-background-78155109.html
CYBER WAR red Rubber Stamp over a white background. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-cyber-war-red-rubber-stamp-over-a-white-background-78155109.htmlRFEF47HW–CYBER WAR red Rubber Stamp over a white background.
 The keyboard of a military combat machine and headphones lie on a camouflage camouflage net, cyber police, online attack, technology Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/the-keyboard-of-a-military-combat-machine-and-headphones-lie-on-a-camouflage-camouflage-net-cyber-police-online-attack-technology-image469852083.html
The keyboard of a military combat machine and headphones lie on a camouflage camouflage net, cyber police, online attack, technology Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/the-keyboard-of-a-military-combat-machine-and-headphones-lie-on-a-camouflage-camouflage-net-cyber-police-online-attack-technology-image469852083.htmlRF2J8BH3F–The keyboard of a military combat machine and headphones lie on a camouflage camouflage net, cyber police, online attack, technology
 Cyberwar Virtual Warfare Hacking Invasion 3d Illustration Shows Government Cyber War Or Army Cyberterrorism Combat Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyberwar-virtual-warfare-hacking-invasion-3d-illustration-shows-government-cyber-war-or-army-cyberterrorism-combat-image212232627.html
Cyberwar Virtual Warfare Hacking Invasion 3d Illustration Shows Government Cyber War Or Army Cyberterrorism Combat Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyberwar-virtual-warfare-hacking-invasion-3d-illustration-shows-government-cyber-war-or-army-cyberterrorism-combat-image212232627.htmlRFP980TK–Cyberwar Virtual Warfare Hacking Invasion 3d Illustration Shows Government Cyber War Or Army Cyberterrorism Combat
 Military Operation in Action, Soldiers Using Military Grade Laptop Use Military Industrial Complex Hardware for Accomplishing International Mission. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-military-operation-in-action-soldiers-using-military-grade-laptop-176615700.html
Military Operation in Action, Soldiers Using Military Grade Laptop Use Military Industrial Complex Hardware for Accomplishing International Mission. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-military-operation-in-action-soldiers-using-military-grade-laptop-176615700.htmlRFM79F3G–Military Operation in Action, Soldiers Using Military Grade Laptop Use Military Industrial Complex Hardware for Accomplishing International Mission.
 PC keyboard with the message of war Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-pc-keyboard-with-the-message-of-war-33578039.html
PC keyboard with the message of war Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-pc-keyboard-with-the-message-of-war-33578039.htmlRFBXHH3K–PC keyboard with the message of war
 Cyber war and hybrid conflict symbol technology concept. Abstract sign on glitch screens 3d illustration. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-war-and-hybrid-conflict-symbol-technology-concept-abstract-sign-on-glitch-screens-3d-illustration-image637708364.html
Cyber war and hybrid conflict symbol technology concept. Abstract sign on glitch screens 3d illustration. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-war-and-hybrid-conflict-symbol-technology-concept-abstract-sign-on-glitch-screens-3d-illustration-image637708364.htmlRF2S1E3EM–Cyber war and hybrid conflict symbol technology concept. Abstract sign on glitch screens 3d illustration.
 Dark web cyber war concept. Hooded hacker using a laptop for organizing massive data breach attack on government servers Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/dark-web-cyber-war-concept-hooded-hacker-using-a-laptop-for-organizing-massive-data-breach-attack-on-government-servers-image463275823.html
Dark web cyber war concept. Hooded hacker using a laptop for organizing massive data breach attack on government servers Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/dark-web-cyber-war-concept-hooded-hacker-using-a-laptop-for-organizing-massive-data-breach-attack-on-government-servers-image463275823.htmlRF2HWM113–Dark web cyber war concept. Hooded hacker using a laptop for organizing massive data breach attack on government servers
 cyber war - word in vintage letterpress wood type Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-war-word-in-vintage-letterpress-wood-type-image483657681.html
cyber war - word in vintage letterpress wood type Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-war-word-in-vintage-letterpress-wood-type-image483657681.htmlRF2K2TE8H–cyber war - word in vintage letterpress wood type
 CYBER WAR. Concept illustration. Graphic tag collection. Wordcloud collage. Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-cyber-war-concept-illustration-graphic-tag-collection-wordcloud-collage-84278655.html
CYBER WAR. Concept illustration. Graphic tag collection. Wordcloud collage. Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-cyber-war-concept-illustration-graphic-tag-collection-wordcloud-collage-84278655.htmlRFEW367Y–CYBER WAR. Concept illustration. Graphic tag collection. Wordcloud collage.
 Symbolic image, cyber war Russia China, cyber security, cyber attacks worldwide, computer crime, digital IT attacks, economy, energy economy, nuclear Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/symbolic-image-cyber-war-russia-china-cyber-security-cyber-attacks-worldwide-computer-crime-digital-it-attacks-economy-energy-economy-nuclear-image605609195.html
Symbolic image, cyber war Russia China, cyber security, cyber attacks worldwide, computer crime, digital IT attacks, economy, energy economy, nuclear Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/symbolic-image-cyber-war-russia-china-cyber-security-cyber-attacks-worldwide-computer-crime-digital-it-attacks-economy-energy-economy-nuclear-image605609195.htmlRM2X57TKR–Symbolic image, cyber war Russia China, cyber security, cyber attacks worldwide, computer crime, digital IT attacks, economy, energy economy, nuclear
 Cyber war: Bank of America has stopped handling WikiLeaks transactions Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-cyber-war-bank-of-america-has-stopped-handling-wikileaks-transactions-33521045.html
Cyber war: Bank of America has stopped handling WikiLeaks transactions Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-cyber-war-bank-of-america-has-stopped-handling-wikileaks-transactions-33521045.htmlRMBXF0C5–Cyber war: Bank of America has stopped handling WikiLeaks transactions
 Terrorist working on his computer. Concept about international crisis, war, terrorism ,terrorist and bandit Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/terrorist-working-on-his-computer-concept-about-international-crisis-image156839658.html
Terrorist working on his computer. Concept about international crisis, war, terrorism ,terrorist and bandit Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/terrorist-working-on-his-computer-concept-about-international-crisis-image156839658.htmlRFK34JGA–Terrorist working on his computer. Concept about international crisis, war, terrorism ,terrorist and bandit
 soldiers silhouettes in front of world map, cyber war concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-image-soldiers-silhouettes-in-front-of-world-map-cyber-war-concept-163090496.html
soldiers silhouettes in front of world map, cyber war concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-image-soldiers-silhouettes-in-front-of-world-map-cyber-war-concept-163090496.htmlRMKD9BGG–soldiers silhouettes in front of world map, cyber war concept
 digital safety concept computer virus in electronic environment, 3D illustration Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-digital-safety-concept-computer-virus-in-electronic-environment-3d-105314896.html
digital safety concept computer virus in electronic environment, 3D illustration Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-digital-safety-concept-computer-virus-in-electronic-environment-3d-105314896.htmlRFG39E68–digital safety concept computer virus in electronic environment, 3D illustration
 Acts of electronic warfare are real threat in modern Cyber War disruptive to business, military, education, health, and government. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/acts-of-electronic-warfare-are-real-threat-in-modern-cyber-war-disruptive-to-business-military-education-health-and-government-image462334889.html
Acts of electronic warfare are real threat in modern Cyber War disruptive to business, military, education, health, and government. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/acts-of-electronic-warfare-are-real-threat-in-modern-cyber-war-disruptive-to-business-military-education-health-and-government-image462334889.htmlRF2HT54T9–Acts of electronic warfare are real threat in modern Cyber War disruptive to business, military, education, health, and government.
 bus stop cyber war Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-bus-stop-cyber-war-79611017.html
bus stop cyber war Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-bus-stop-cyber-war-79611017.htmlRFEHEGJH–bus stop cyber war
RF2J5F59T–Digital war and computer technology warfare as a hand grenade explosive device that is pixelated representing hacking cyber attack and internet.
 Social Media Peace or War. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-social-media-peace-or-war-122693768.html
Social Media Peace or War. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-social-media-peace-or-war-122693768.htmlRFH3H548–Social Media Peace or War.
 Woman hacker data breach China vs Russia cyber war Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/woman-hacker-data-breach-china-vs-russia-cyber-war-image345103056.html
Woman hacker data breach China vs Russia cyber war Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/woman-hacker-data-breach-china-vs-russia-cyber-war-image345103056.htmlRF2B1CPD4–Woman hacker data breach China vs Russia cyber war
 smartphone security access protection concept. phone hacking from internet intruder digital cyber attack anti virus system. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/smartphone-security-access-protection-concept-phone-hacking-from-internet-intruder-digital-cyber-attack-anti-virus-system-image478263067.html
smartphone security access protection concept. phone hacking from internet intruder digital cyber attack anti virus system. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/smartphone-security-access-protection-concept-phone-hacking-from-internet-intruder-digital-cyber-attack-anti-virus-system-image478263067.htmlRF2JP2NBR–smartphone security access protection concept. phone hacking from internet intruder digital cyber attack anti virus system.
 The keyboard of a military combat machine and headphones lie on a camouflage camouflage net, cyber police, online attack, technology Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/the-keyboard-of-a-military-combat-machine-and-headphones-lie-on-a-camouflage-camouflage-net-cyber-police-online-attack-technology-image469852051.html
The keyboard of a military combat machine and headphones lie on a camouflage camouflage net, cyber police, online attack, technology Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/the-keyboard-of-a-military-combat-machine-and-headphones-lie-on-a-camouflage-camouflage-net-cyber-police-online-attack-technology-image469852051.htmlRF2J8BH2B–The keyboard of a military combat machine and headphones lie on a camouflage camouflage net, cyber police, online attack, technology
 cyber war on database with pistol in front of white Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-cyber-war-on-database-with-pistol-in-front-of-white-54234774.html
cyber war on database with pistol in front of white Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-cyber-war-on-database-with-pistol-in-front-of-white-54234774.htmlRMD46H06–cyber war on database with pistol in front of white
 x05 4 1 1 Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-x05-4-1-1-21796638.html
x05 4 1 1 Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-x05-4-1-1-21796638.htmlRFB7CWRA–x05 4 1 1
 Keyboard with red attack button concept for information security Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-keyboard-with-red-attack-button-concept-for-information-security-91559197.html
Keyboard with red attack button concept for information security Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-keyboard-with-red-attack-button-concept-for-information-security-91559197.htmlRFF8XTK9–Keyboard with red attack button concept for information security
 Cyber war and hybrid conflict symbol technology concept. Abstract sign on glitch screens 3d illustration. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-war-and-hybrid-conflict-symbol-technology-concept-abstract-sign-on-glitch-screens-3d-illustration-image637708341.html
Cyber war and hybrid conflict symbol technology concept. Abstract sign on glitch screens 3d illustration. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-war-and-hybrid-conflict-symbol-technology-concept-abstract-sign-on-glitch-screens-3d-illustration-image637708341.htmlRF2S1E3DW–Cyber war and hybrid conflict symbol technology concept. Abstract sign on glitch screens 3d illustration.
 Tech. Sgt. Wyatt Bloom uses a spectrum analyzer to check television broadcast network routers at the Defense Media Activity’s Headquarters at Fort Meade, Md., July 18, 2012. Bloom is a cyber-transport technician assigned to DMA. Val Gempis Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-tech-sgt-wyatt-bloom-uses-a-spectrum-analyzer-to-check-television-78729599.html
Tech. Sgt. Wyatt Bloom uses a spectrum analyzer to check television broadcast network routers at the Defense Media Activity’s Headquarters at Fort Meade, Md., July 18, 2012. Bloom is a cyber-transport technician assigned to DMA. Val Gempis Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-tech-sgt-wyatt-bloom-uses-a-spectrum-analyzer-to-check-television-78729599.htmlRMEG2CBB–Tech. Sgt. Wyatt Bloom uses a spectrum analyzer to check television broadcast network routers at the Defense Media Activity’s Headquarters at Fort Meade, Md., July 18, 2012. Bloom is a cyber-transport technician assigned to DMA. Val Gempis
 Cyber War Special Forces Fully Armed Soldier Uncovers Internationally Wanted Hacker's Hideout Place. Lair is Full of Monitors, Cables and Has Neon. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-war-special-forces-fully-armed-soldier-uncovers-internationally-wanted-hackers-hideout-place-lair-is-full-of-monitors-cables-and-has-neon-image177830426.html
Cyber War Special Forces Fully Armed Soldier Uncovers Internationally Wanted Hacker's Hideout Place. Lair is Full of Monitors, Cables and Has Neon. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-war-special-forces-fully-armed-soldier-uncovers-internationally-wanted-hackers-hideout-place-lair-is-full-of-monitors-cables-and-has-neon-image177830426.htmlRFM98TEJ–Cyber War Special Forces Fully Armed Soldier Uncovers Internationally Wanted Hacker's Hideout Place. Lair is Full of Monitors, Cables and Has Neon.
 3D rendering of a futuristic robot cop holding gun with a dog beside him, fighting a war in a ruined city. Smoke and fire all around them. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/3d-rendering-of-a-futuristic-robot-cop-holding-gun-with-a-dog-beside-him-fighting-a-war-in-a-ruined-city-smoke-and-fire-all-around-them-image211633917.html
3D rendering of a futuristic robot cop holding gun with a dog beside him, fighting a war in a ruined city. Smoke and fire all around them. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/3d-rendering-of-a-futuristic-robot-cop-holding-gun-with-a-dog-beside-him-fighting-a-war-in-a-ruined-city-smoke-and-fire-all-around-them-image211633917.htmlRFP88N65–3D rendering of a futuristic robot cop holding gun with a dog beside him, fighting a war in a ruined city. Smoke and fire all around them.
 Symbolic image, cyber war Russia China, cyber security, cyber attacks worldwide, computer crime, digital IT attacks, economy, energy economy, nuclear Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/symbolic-image-cyber-war-russia-china-cyber-security-cyber-attacks-worldwide-computer-crime-digital-it-attacks-economy-energy-economy-nuclear-image605609191.html
Symbolic image, cyber war Russia China, cyber security, cyber attacks worldwide, computer crime, digital IT attacks, economy, energy economy, nuclear Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/symbolic-image-cyber-war-russia-china-cyber-security-cyber-attacks-worldwide-computer-crime-digital-it-attacks-economy-energy-economy-nuclear-image605609191.htmlRM2X57TKK–Symbolic image, cyber war Russia China, cyber security, cyber attacks worldwide, computer crime, digital IT attacks, economy, energy economy, nuclear
 Cyber war: original WiikiLeaks website has become unavailable Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-cyber-war-original-wiikileaks-website-has-become-unavailable-33521160.html
Cyber war: original WiikiLeaks website has become unavailable Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-cyber-war-original-wiikileaks-website-has-become-unavailable-33521160.htmlRMBXF0G8–Cyber war: original WiikiLeaks website has become unavailable
 cyber war - isolated words in vintage letterpress wood type, cyberwarfare and digital attacks concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-war-isolated-words-in-vintage-letterpress-wood-type-cyberwarfare-and-digital-attacks-concept-image468606945.html
cyber war - isolated words in vintage letterpress wood type, cyberwarfare and digital attacks concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-war-isolated-words-in-vintage-letterpress-wood-type-cyberwarfare-and-digital-attacks-concept-image468606945.htmlRF2J6ATX9–cyber war - isolated words in vintage letterpress wood type, cyberwarfare and digital attacks concept
 soldiers silhouettes in front of world map, cyber war concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-image-soldiers-silhouettes-in-front-of-world-map-cyber-war-concept-163090493.html
soldiers silhouettes in front of world map, cyber war concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-image-soldiers-silhouettes-in-front-of-world-map-cyber-war-concept-163090493.htmlRMKD9BGD–soldiers silhouettes in front of world map, cyber war concept
 Anonymous Hacker commits cyber crime with laptop held in hand Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/anonymous-hacker-commits-cyber-crime-with-laptop-held-in-hand-image465940648.html
Anonymous Hacker commits cyber crime with laptop held in hand Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/anonymous-hacker-commits-cyber-crime-with-laptop-held-in-hand-image465940648.htmlRF2J21C1C–Anonymous Hacker commits cyber crime with laptop held in hand
 A masked protester wearing Guy Fawkes mask, camped at St Pauls Occupy London site on an old telephone, tent in background. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-a-masked-protester-wearing-guy-fawkes-mask-camped-at-st-pauls-occupy-43157093.html
A masked protester wearing Guy Fawkes mask, camped at St Pauls Occupy London site on an old telephone, tent in background. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-a-masked-protester-wearing-guy-fawkes-mask-camped-at-st-pauls-occupy-43157093.htmlRMCE5Y8N–A masked protester wearing Guy Fawkes mask, camped at St Pauls Occupy London site on an old telephone, tent in background.
 Hacker man looks at the screen. There are green texts on the black screen. Hacker writes code. People silhouette is looking at the screen. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/hacker-man-looks-at-the-screen-there-are-green-texts-on-the-black-screen-hacker-writes-code-people-silhouette-is-looking-at-the-screen-image395346876.html
Hacker man looks at the screen. There are green texts on the black screen. Hacker writes code. People silhouette is looking at the screen. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/hacker-man-looks-at-the-screen-there-are-green-texts-on-the-black-screen-hacker-writes-code-people-silhouette-is-looking-at-the-screen-image395346876.htmlRF2DY5GY8–Hacker man looks at the screen. There are green texts on the black screen. Hacker writes code. People silhouette is looking at the screen.
 Hands holding election signs protesting a computer cyber attack outside the Houses of Parliament at Westminster Palace in London, UK Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-hands-holding-election-signs-protesting-a-computer-cyber-attack-outside-140662809.html
Hands holding election signs protesting a computer cyber attack outside the Houses of Parliament at Westminster Palace in London, UK Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-hands-holding-election-signs-protesting-a-computer-cyber-attack-outside-140662809.htmlRFJ4RMRN–Hands holding election signs protesting a computer cyber attack outside the Houses of Parliament at Westminster Palace in London, UK
 Cyber war, Hacker with laptop initiating hacker attack. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-image-cyber-war-hacker-with-laptop-initiating-hacker-attack-160477705.html
Cyber war, Hacker with laptop initiating hacker attack. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-image-cyber-war-hacker-with-laptop-initiating-hacker-attack-160477705.htmlRFK92AXH–Cyber war, Hacker with laptop initiating hacker attack.
 Woman hacker data breach China vs Russia cyber war Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/woman-hacker-data-breach-china-vs-russia-cyber-war-image345103140.html
Woman hacker data breach China vs Russia cyber war Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/woman-hacker-data-breach-china-vs-russia-cyber-war-image345103140.htmlRF2B1CPG4–Woman hacker data breach China vs Russia cyber war
 Cyber war with nuclear symbol hologram on a processor technology concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-war-with-nuclear-symbol-hologram-on-a-processor-technology-concept-image458221935.html
Cyber war with nuclear symbol hologram on a processor technology concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-war-with-nuclear-symbol-hologram-on-a-processor-technology-concept-image458221935.htmlRF2HHDPN3–Cyber war with nuclear symbol hologram on a processor technology concept
 War Sound ridden by Richard Johnson in the Spectra Cyber Security Solutions Trophy Handicap Chase during Festival Trials Day at Cheltenham Racecourse. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/war-sound-ridden-by-richard-johnson-in-the-spectra-cyber-security-solutions-trophy-handicap-chase-during-festival-trials-day-at-cheltenham-racecourse-image234367902.html
War Sound ridden by Richard Johnson in the Spectra Cyber Security Solutions Trophy Handicap Chase during Festival Trials Day at Cheltenham Racecourse. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/war-sound-ridden-by-richard-johnson-in-the-spectra-cyber-security-solutions-trophy-handicap-chase-during-festival-trials-day-at-cheltenham-racecourse-image234367902.htmlRMRH8AJ6–War Sound ridden by Richard Johnson in the Spectra Cyber Security Solutions Trophy Handicap Chase during Festival Trials Day at Cheltenham Racecourse.
 cyber war on database with pistol in front of white Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-cyber-war-on-database-with-pistol-in-front-of-white-54619874.html
cyber war on database with pistol in front of white Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-cyber-war-on-database-with-pistol-in-front-of-white-54619874.htmlRFD4T45P–cyber war on database with pistol in front of white
 Still life depicting international computer crime Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-still-life-depicting-international-computer-crime-21796898.html
Still life depicting international computer crime Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-still-life-depicting-international-computer-crime-21796898.htmlRFB7CX4J–Still life depicting international computer crime
 Keyboard with green shield key concept for information security Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-keyboard-with-green-shield-key-concept-for-information-security-91559204.html
Keyboard with green shield key concept for information security Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-keyboard-with-green-shield-key-concept-for-information-security-91559204.htmlRFF8XTKG–Keyboard with green shield key concept for information security
 Cyber war and hybrid conflict symbol technology concept. Abstract sign on glitch screens 3d illustration. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-war-and-hybrid-conflict-symbol-technology-concept-abstract-sign-on-glitch-screens-3d-illustration-image637708348.html
Cyber war and hybrid conflict symbol technology concept. Abstract sign on glitch screens 3d illustration. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-war-and-hybrid-conflict-symbol-technology-concept-abstract-sign-on-glitch-screens-3d-illustration-image637708348.htmlRF2S1E3E4–Cyber war and hybrid conflict symbol technology concept. Abstract sign on glitch screens 3d illustration.
 US Military Soldier Smart Phone Espionage. Cyber War Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/us-military-soldier-smart-phone-espionage-cyber-war-image505908864.html
US Military Soldier Smart Phone Espionage. Cyber War Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/us-military-soldier-smart-phone-espionage-cyber-war-image505908864.htmlRF2MB23WM–US Military Soldier Smart Phone Espionage. Cyber War
 Cyber War Special Forces Fully Armed Soldier Uncovers Internationally Wanted Hacker's Hideout Place. Lair is Full of Monitors, Cables and Has Neon. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-war-special-forces-fully-armed-soldier-uncovers-internationally-wanted-hackers-hideout-place-lair-is-full-of-monitors-cables-and-has-neon-image177830430.html
Cyber War Special Forces Fully Armed Soldier Uncovers Internationally Wanted Hacker's Hideout Place. Lair is Full of Monitors, Cables and Has Neon. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-war-special-forces-fully-armed-soldier-uncovers-internationally-wanted-hackers-hideout-place-lair-is-full-of-monitors-cables-and-has-neon-image177830430.htmlRFM98TEP–Cyber War Special Forces Fully Armed Soldier Uncovers Internationally Wanted Hacker's Hideout Place. Lair is Full of Monitors, Cables and Has Neon.
 Cyber Warfare. Machine gun on keyboard computer. Fake news. Hybrid war media influence public opinion. Data security cyber war terrorism threat Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-warfare-machine-gun-on-keyboard-computer-fake-news-hybrid-war-media-influence-public-opinion-data-security-cyber-war-terrorism-threat-image465745511.html
Cyber Warfare. Machine gun on keyboard computer. Fake news. Hybrid war media influence public opinion. Data security cyber war terrorism threat Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-warfare-machine-gun-on-keyboard-computer-fake-news-hybrid-war-media-influence-public-opinion-data-security-cyber-war-terrorism-threat-image465745511.htmlRF2J1MF47–Cyber Warfare. Machine gun on keyboard computer. Fake news. Hybrid war media influence public opinion. Data security cyber war terrorism threat
 Symbolic image, cyber war Russia China, cyber security, cyber attacks worldwide, computer crime, digital IT attacks, economy, energy economy, nuclear Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/symbolic-image-cyber-war-russia-china-cyber-security-cyber-attacks-worldwide-computer-crime-digital-it-attacks-economy-energy-economy-nuclear-image605609192.html
Symbolic image, cyber war Russia China, cyber security, cyber attacks worldwide, computer crime, digital IT attacks, economy, energy economy, nuclear Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/symbolic-image-cyber-war-russia-china-cyber-security-cyber-attacks-worldwide-computer-crime-digital-it-attacks-economy-energy-economy-nuclear-image605609192.htmlRM2X57TKM–Symbolic image, cyber war Russia China, cyber security, cyber attacks worldwide, computer crime, digital IT attacks, economy, energy economy, nuclear
 Cyber war: WikiLeaks website now has mirror sites throughout Europe Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-cyber-war-wikileaks-website-now-has-mirror-sites-throughout-europe-33521032.html
Cyber war: WikiLeaks website now has mirror sites throughout Europe Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-cyber-war-wikileaks-website-now-has-mirror-sites-throughout-europe-33521032.htmlRMBXF0BM–Cyber war: WikiLeaks website now has mirror sites throughout Europe
 cyber war - words in vintage letterpress wood type on laptop screen, cyberwarfare and digital attacks concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-war-words-in-vintage-letterpress-wood-type-on-laptop-screen-cyberwarfare-and-digital-attacks-concept-image470097774.html
cyber war - words in vintage letterpress wood type on laptop screen, cyberwarfare and digital attacks concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-war-words-in-vintage-letterpress-wood-type-on-laptop-screen-cyberwarfare-and-digital-attacks-concept-image470097774.htmlRF2J8PPE6–cyber war - words in vintage letterpress wood type on laptop screen, cyberwarfare and digital attacks concept
 Cyber war concept: black computer keyboard with text Cyber Attack Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-war-concept-black-computer-keyboard-with-text-cyber-attack-image464933160.html
Cyber war concept: black computer keyboard with text Cyber Attack Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-war-concept-black-computer-keyboard-with-text-cyber-attack-image464933160.htmlRF2J0BEYM–Cyber war concept: black computer keyboard with text Cyber Attack
 Anonymous Hacker commits cyber crime with laptop held in hand Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/anonymous-hacker-commits-cyber-crime-with-laptop-held-in-hand-image465940651.html
Anonymous Hacker commits cyber crime with laptop held in hand Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/anonymous-hacker-commits-cyber-crime-with-laptop-held-in-hand-image465940651.htmlRF2J21C1F–Anonymous Hacker commits cyber crime with laptop held in hand
 The word cyber war written on a sticky note paper on computer keyboard. Business concept for virtual war, hacker system attacks or digital theft. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/the-word-cyber-war-written-on-a-sticky-note-paper-on-computer-keyboard-business-concept-for-virtual-war-hacker-system-attacks-or-digital-theft-image643782604.html
The word cyber war written on a sticky note paper on computer keyboard. Business concept for virtual war, hacker system attacks or digital theft. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/the-word-cyber-war-written-on-a-sticky-note-paper-on-computer-keyboard-business-concept-for-virtual-war-hacker-system-attacks-or-digital-theft-image643782604.htmlRF2SBAR7T–The word cyber war written on a sticky note paper on computer keyboard. Business concept for virtual war, hacker system attacks or digital theft.
 bearded man with a hoodie, hacking on a black screen computer Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/bearded-man-with-a-hoodie-hacking-on-a-black-screen-computer-image468650545.html
bearded man with a hoodie, hacking on a black screen computer Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/bearded-man-with-a-hoodie-hacking-on-a-black-screen-computer-image468650545.htmlRF2J6CTFD–bearded man with a hoodie, hacking on a black screen computer
 Hands holding signs protesting a computer cyber attack outside the Houses of Parliament at Westminster Palace in London, UK Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-hands-holding-signs-protesting-a-computer-cyber-attack-outside-the-140529930.html
Hands holding signs protesting a computer cyber attack outside the Houses of Parliament at Westminster Palace in London, UK Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-hands-holding-signs-protesting-a-computer-cyber-attack-outside-the-140529930.htmlRFJ4HKA2–Hands holding signs protesting a computer cyber attack outside the Houses of Parliament at Westminster Palace in London, UK
 Drone attacking a women. Drone targeting a human. Autonomous drone seeking out human target. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-drone-attacking-a-women-drone-targeting-a-human-autonomous-drone-seeking-175440160.html
Drone attacking a women. Drone targeting a human. Autonomous drone seeking out human target. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-drone-attacking-a-women-drone-targeting-a-human-autonomous-drone-seeking-175440160.htmlRFM5BYM0–Drone attacking a women. Drone targeting a human. Autonomous drone seeking out human target.
 Woman hacker data breach China vs Russia cyber war Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/woman-hacker-data-breach-china-vs-russia-cyber-war-image345103147.html
Woman hacker data breach China vs Russia cyber war Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/woman-hacker-data-breach-china-vs-russia-cyber-war-image345103147.htmlRF2B1CPGB–Woman hacker data breach China vs Russia cyber war
 Hand holding a digital weapon Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-hand-holding-a-digital-weapon-57972845.html
Hand holding a digital weapon Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-hand-holding-a-digital-weapon-57972845.htmlRMDA8TXN–Hand holding a digital weapon
 Cyber war in cyberspace, vector digital art Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-war-in-cyberspace-vector-digital-art-image236606105.html
Cyber war in cyberspace, vector digital art Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-war-in-cyberspace-vector-digital-art-image236606105.htmlRFRMX9E1–Cyber war in cyberspace, vector digital art
 cyber war on database with pistol in front of white Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-cyber-war-on-database-with-pistol-in-front-of-white-54619862.html
cyber war on database with pistol in front of white Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-cyber-war-on-database-with-pistol-in-front-of-white-54619862.htmlRFD4T45A–cyber war on database with pistol in front of white
 Cyber war, Hacker with laptop initiating hacker attack. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-image-cyber-war-hacker-with-laptop-initiating-hacker-attack-160477694.html
Cyber war, Hacker with laptop initiating hacker attack. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-image-cyber-war-hacker-with-laptop-initiating-hacker-attack-160477694.htmlRFK92AX6–Cyber war, Hacker with laptop initiating hacker attack.
 Conceptual display Cyber Warfare. Business overview Virtual War Hackers System Attacks Digital Thief Stalker Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/conceptual-display-cyber-warfare-business-overview-virtual-war-hackers-system-attacks-digital-thief-stalker-image548182466.html
Conceptual display Cyber Warfare. Business overview Virtual War Hackers System Attacks Digital Thief Stalker Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/conceptual-display-cyber-warfare-business-overview-virtual-war-hackers-system-attacks-digital-thief-stalker-image548182466.htmlRF2PRRT96–Conceptual display Cyber Warfare. Business overview Virtual War Hackers System Attacks Digital Thief Stalker
 Cyber war and hybrid conflict symbol technology concept. Abstract sign on glitch screens 3d illustration. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-war-and-hybrid-conflict-symbol-technology-concept-abstract-sign-on-glitch-screens-3d-illustration-image637712627.html
Cyber war and hybrid conflict symbol technology concept. Abstract sign on glitch screens 3d illustration. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-war-and-hybrid-conflict-symbol-technology-concept-abstract-sign-on-glitch-screens-3d-illustration-image637712627.htmlRF2S1E8XY–Cyber war and hybrid conflict symbol technology concept. Abstract sign on glitch screens 3d illustration.
 US Military Soldier Smart Phone Espionage. Cyber War Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/us-military-soldier-smart-phone-espionage-cyber-war-image435042971.html
US Military Soldier Smart Phone Espionage. Cyber War Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/us-military-soldier-smart-phone-espionage-cyber-war-image435042971.htmlRF2G7NWMY–US Military Soldier Smart Phone Espionage. Cyber War
 Cyber War Special Forces Fully Armed Soldier Uncovers Internationally Wanted Hacker's Hideout Place. Lair is Full of Monitors, Cables and Has Neon. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-war-special-forces-fully-armed-soldier-uncovers-internationally-wanted-hackers-hideout-place-lair-is-full-of-monitors-cables-and-has-neon-image177830435.html
Cyber War Special Forces Fully Armed Soldier Uncovers Internationally Wanted Hacker's Hideout Place. Lair is Full of Monitors, Cables and Has Neon. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-war-special-forces-fully-armed-soldier-uncovers-internationally-wanted-hackers-hideout-place-lair-is-full-of-monitors-cables-and-has-neon-image177830435.htmlRFM98TEY–Cyber War Special Forces Fully Armed Soldier Uncovers Internationally Wanted Hacker's Hideout Place. Lair is Full of Monitors, Cables and Has Neon.
 Hacker in front of his laptop. Hooded hacker cyber war concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/hacker-in-front-of-his-laptop-hooded-hacker-cyber-war-concept-image396924985.html
Hacker in front of his laptop. Hooded hacker cyber war concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/hacker-in-front-of-his-laptop-hooded-hacker-cyber-war-concept-image396924985.htmlRF2E1NDT9–Hacker in front of his laptop. Hooded hacker cyber war concept
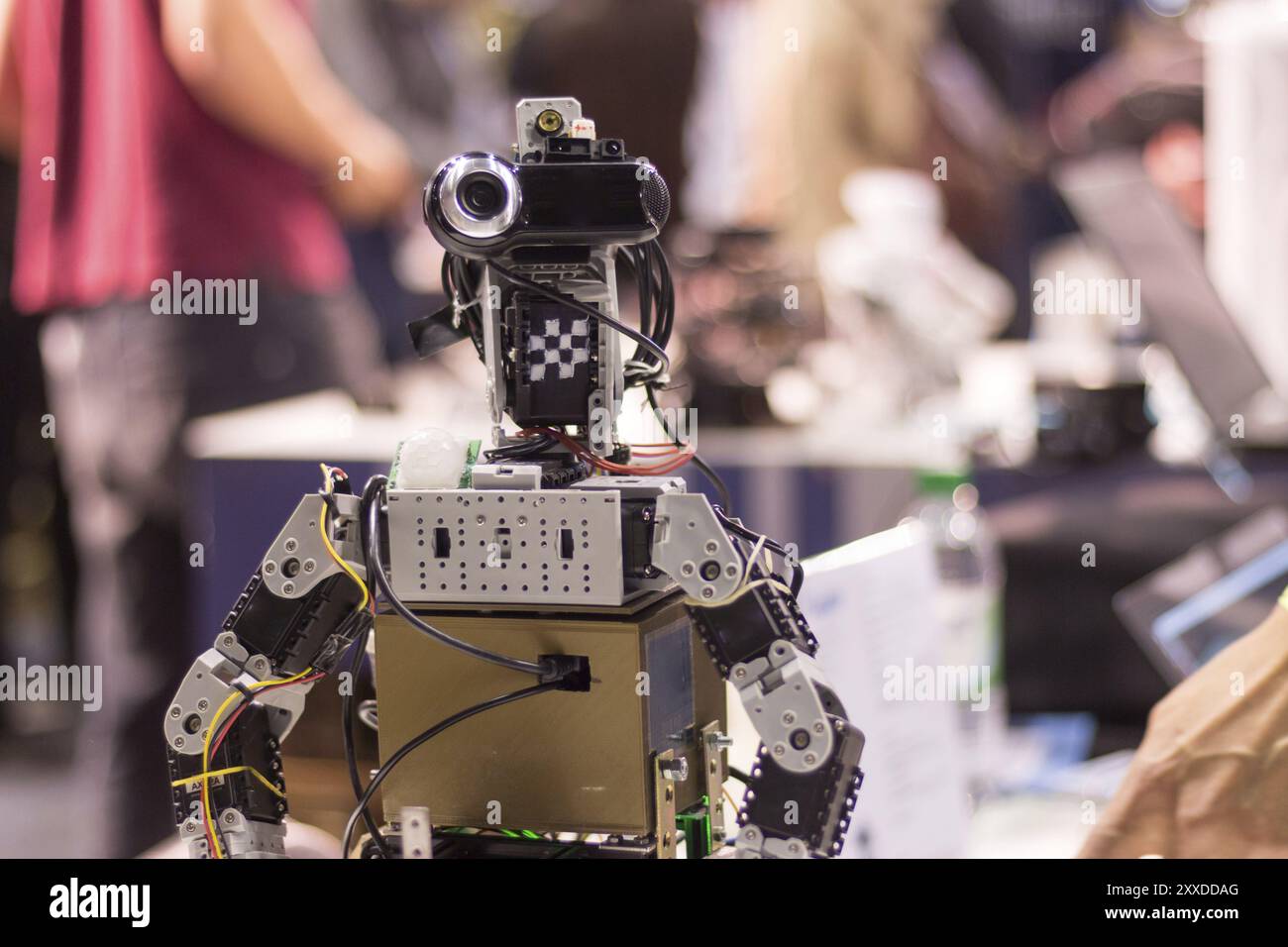 Android with build in webcam, self build autonomous robot Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/android-with-build-in-webcam-self-build-autonomous-robot-image618639800.html
Android with build in webcam, self build autonomous robot Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/android-with-build-in-webcam-self-build-autonomous-robot-image618639800.htmlRF2XXDDAG–Android with build in webcam, self build autonomous robot
 Word writing text Cyber Warfare. Business concept for Virtual War Hackers System Attacks Digital Thief Stalker White pc keyboard Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/word-writing-text-cyber-warfare-business-concept-for-virtual-war-hackers-system-attacks-digital-thief-stalker-white-pc-keyboard-image343860354.html
Word writing text Cyber Warfare. Business concept for Virtual War Hackers System Attacks Digital Thief Stalker White pc keyboard Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/word-writing-text-cyber-warfare-business-concept-for-virtual-war-hackers-system-attacks-digital-thief-stalker-white-pc-keyboard-image343860354.htmlRM2AYC5AX–Word writing text Cyber Warfare. Business concept for Virtual War Hackers System Attacks Digital Thief Stalker White pc keyboard
 cyber war - words in vintage letterpress wood type on a digital tablet, cyberwarfare and digital attacks concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-war-words-in-vintage-letterpress-wood-type-on-a-digital-tablet-cyberwarfare-and-digital-attacks-concept-image468606664.html
cyber war - words in vintage letterpress wood type on a digital tablet, cyberwarfare and digital attacks concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-war-words-in-vintage-letterpress-wood-type-on-a-digital-tablet-cyberwarfare-and-digital-attacks-concept-image468606664.htmlRF2J6ATG8–cyber war - words in vintage letterpress wood type on a digital tablet, cyberwarfare and digital attacks concept
 Russian flag displayed on a laptop screen and Guy Fawkes mask are seen in this illustration photo taken in Krakow, Poland on March 1, 2022. Global hacker group Anonymous declared 'cyber war' against Russia. (Photo by Jakub Porzycki/NurPhoto) Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/russian-flag-displayed-on-a-laptop-screen-and-guy-fawkes-mask-are-seen-in-this-illustration-photo-taken-in-krakow-poland-on-march-1-2022-global-hacker-group-anonymous-declared-cyber-war-against-russia-photo-by-jakub-porzyckinurphoto-image489969325.html
Russian flag displayed on a laptop screen and Guy Fawkes mask are seen in this illustration photo taken in Krakow, Poland on March 1, 2022. Global hacker group Anonymous declared 'cyber war' against Russia. (Photo by Jakub Porzycki/NurPhoto) Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/russian-flag-displayed-on-a-laptop-screen-and-guy-fawkes-mask-are-seen-in-this-illustration-photo-taken-in-krakow-poland-on-march-1-2022-global-hacker-group-anonymous-declared-cyber-war-against-russia-photo-by-jakub-porzyckinurphoto-image489969325.htmlRM2KD40TD–Russian flag displayed on a laptop screen and Guy Fawkes mask are seen in this illustration photo taken in Krakow, Poland on March 1, 2022. Global hacker group Anonymous declared 'cyber war' against Russia. (Photo by Jakub Porzycki/NurPhoto)
 Anonymous Hacker commits cyber crime with laptop held in hand Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/anonymous-hacker-commits-cyber-crime-with-laptop-held-in-hand-image465940644.html
Anonymous Hacker commits cyber crime with laptop held in hand Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/anonymous-hacker-commits-cyber-crime-with-laptop-held-in-hand-image465940644.htmlRF2J21C18–Anonymous Hacker commits cyber crime with laptop held in hand
 dark web hooded hacker cyber war concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/dark-web-hooded-hacker-cyber-war-concept-image371548351.html
dark web hooded hacker cyber war concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/dark-web-hooded-hacker-cyber-war-concept-image371548351.htmlRF2CGDDKY–dark web hooded hacker cyber war concept
 Marines and Civilians of Marine Corps Forces Cyberspace Command and Marine Corps Cyberspace Warfare Group participated in Joint Integrated Cyber Training 2021 (JICT) hosted by the USINDOPACOM Cyber War Innovation Center. The two-week full-spectrum exercise took place in Hawaii and consisted of teams from multiple services. The event served as an excellent tactical and analytic exchange for the teams and helped to inform operational and strategic planners through a realistic scenario within cyberspace. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/marines-and-civilians-of-marine-corps-forces-cyberspace-command-and-marine-corps-cyberspace-warfare-group-participated-in-joint-integrated-cyber-training-2021-jict-hosted-by-the-usindopacom-cyber-war-innovation-center-the-two-week-full-spectrum-exercise-took-place-in-hawaii-and-consisted-of-teams-from-multiple-services-the-event-served-as-an-excellent-tactical-and-analytic-exchange-for-the-teams-and-helped-to-inform-operational-and-strategic-planners-through-a-realistic-scenario-within-cyberspace-image442376817.html
Marines and Civilians of Marine Corps Forces Cyberspace Command and Marine Corps Cyberspace Warfare Group participated in Joint Integrated Cyber Training 2021 (JICT) hosted by the USINDOPACOM Cyber War Innovation Center. The two-week full-spectrum exercise took place in Hawaii and consisted of teams from multiple services. The event served as an excellent tactical and analytic exchange for the teams and helped to inform operational and strategic planners through a realistic scenario within cyberspace. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/marines-and-civilians-of-marine-corps-forces-cyberspace-command-and-marine-corps-cyberspace-warfare-group-participated-in-joint-integrated-cyber-training-2021-jict-hosted-by-the-usindopacom-cyber-war-innovation-center-the-two-week-full-spectrum-exercise-took-place-in-hawaii-and-consisted-of-teams-from-multiple-services-the-event-served-as-an-excellent-tactical-and-analytic-exchange-for-the-teams-and-helped-to-inform-operational-and-strategic-planners-through-a-realistic-scenario-within-cyberspace-image442376817.htmlRM2GKM041–Marines and Civilians of Marine Corps Forces Cyberspace Command and Marine Corps Cyberspace Warfare Group participated in Joint Integrated Cyber Training 2021 (JICT) hosted by the USINDOPACOM Cyber War Innovation Center. The two-week full-spectrum exercise took place in Hawaii and consisted of teams from multiple services. The event served as an excellent tactical and analytic exchange for the teams and helped to inform operational and strategic planners through a realistic scenario within cyberspace.
 Signs representing issues with modern elections, the hacking of accounts and leaking of information, at the Houses of Parliament at Westminster London Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-signs-representing-issues-with-modern-elections-the-hacking-of-accounts-140661100.html
Signs representing issues with modern elections, the hacking of accounts and leaking of information, at the Houses of Parliament at Westminster London Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-signs-representing-issues-with-modern-elections-the-hacking-of-accounts-140661100.htmlRFJ4RJJM–Signs representing issues with modern elections, the hacking of accounts and leaking of information, at the Houses of Parliament at Westminster London
 Conceptual image of national threats of cyberattacks against American infrastructure seen in flag, keyboard, and CYBERWAR card still life Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/conceptual-image-of-national-threats-of-cyberattacks-against-american-infrastructure-seen-in-flag-keyboard-and-cyberwar-card-still-life-image464994327.html
Conceptual image of national threats of cyberattacks against American infrastructure seen in flag, keyboard, and CYBERWAR card still life Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/conceptual-image-of-national-threats-of-cyberattacks-against-american-infrastructure-seen-in-flag-keyboard-and-cyberwar-card-still-life-image464994327.htmlRF2J0E907–Conceptual image of national threats of cyberattacks against American infrastructure seen in flag, keyboard, and CYBERWAR card still life
 Woman hacker data breach China vs Russia cyber war Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/woman-hacker-data-breach-china-vs-russia-cyber-war-image345103046.html
Woman hacker data breach China vs Russia cyber war Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/woman-hacker-data-breach-china-vs-russia-cyber-war-image345103046.htmlRF2B1CPCP–Woman hacker data breach China vs Russia cyber war
 Chinese students compete in a cyber war-game contest in downtown Beijing on August 26, 2012. Cyber crime in China poses a serious threat to the fast-growing economy and it is likely that such attacks, already costing in excess of US$850 billion a year, will only increase. UPI/Stephen Shaver Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/chinese-students-compete-in-a-cyber-war-game-contest-in-downtown-beijing-on-august-26-2012-cyber-crime-in-china-poses-a-serious-threat-to-the-fast-growing-economy-and-it-is-likely-that-such-attacks-already-costing-in-excess-of-us850-billion-a-year-will-only-increase-upistephen-shaver-image258178665.html
Chinese students compete in a cyber war-game contest in downtown Beijing on August 26, 2012. Cyber crime in China poses a serious threat to the fast-growing economy and it is likely that such attacks, already costing in excess of US$850 billion a year, will only increase. UPI/Stephen Shaver Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/chinese-students-compete-in-a-cyber-war-game-contest-in-downtown-beijing-on-august-26-2012-cyber-crime-in-china-poses-a-serious-threat-to-the-fast-growing-economy-and-it-is-likely-that-such-attacks-already-costing-in-excess-of-us850-billion-a-year-will-only-increase-upistephen-shaver-image258178665.htmlRMW011EH–Chinese students compete in a cyber war-game contest in downtown Beijing on August 26, 2012. Cyber crime in China poses a serious threat to the fast-growing economy and it is likely that such attacks, already costing in excess of US$850 billion a year, will only increase. UPI/Stephen Shaver
 Bildnummer: 54881674 Datum: 04.02.2011 Copyright: imago/Xinhua (110204) -- MUNICH, Feb. 4, 2011 (Xinhua) -- NATO Secretary-General Anders Fogh Rasmussen speaks to the press during the 47th Munich Security Conference (MSC) in Munich, Germany, Feb. 4, 2011. The MSC kicked off here on Friday, during which 350 world leaders and diplomats will discuss major global security issues, including financial crisis, cyber war, transatlantic security, NATO-Russia relationship, non-proliferation of mass destruction arms, Afghanistan and Middle East. (Xinhua/Luo Huanhuan) GERMANY-MUNICH-NATO-RASMUSSEN PUBLI Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/bildnummer-54881674-datum-04022011-copyright-imagoxinhua-110204-munich-feb-4-2011-xinhua-nato-secretary-general-anders-fogh-rasmussen-speaks-to-the-press-during-the-47th-munich-security-conference-msc-in-munich-germany-feb-4-2011-the-msc-kicked-off-here-on-friday-during-which-350-world-leaders-and-diplomats-will-discuss-major-global-security-issues-including-financial-crisis-cyber-war-transatlantic-security-nato-russia-relationship-non-proliferation-of-mass-destruction-arms-afghanistan-and-middle-east-xinhualuo-huanhuan-germany-munich-nato-rasmussen-publi-image562701489.html
Bildnummer: 54881674 Datum: 04.02.2011 Copyright: imago/Xinhua (110204) -- MUNICH, Feb. 4, 2011 (Xinhua) -- NATO Secretary-General Anders Fogh Rasmussen speaks to the press during the 47th Munich Security Conference (MSC) in Munich, Germany, Feb. 4, 2011. The MSC kicked off here on Friday, during which 350 world leaders and diplomats will discuss major global security issues, including financial crisis, cyber war, transatlantic security, NATO-Russia relationship, non-proliferation of mass destruction arms, Afghanistan and Middle East. (Xinhua/Luo Huanhuan) GERMANY-MUNICH-NATO-RASMUSSEN PUBLI Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/bildnummer-54881674-datum-04022011-copyright-imagoxinhua-110204-munich-feb-4-2011-xinhua-nato-secretary-general-anders-fogh-rasmussen-speaks-to-the-press-during-the-47th-munich-security-conference-msc-in-munich-germany-feb-4-2011-the-msc-kicked-off-here-on-friday-during-which-350-world-leaders-and-diplomats-will-discuss-major-global-security-issues-including-financial-crisis-cyber-war-transatlantic-security-nato-russia-relationship-non-proliferation-of-mass-destruction-arms-afghanistan-and-middle-east-xinhualuo-huanhuan-germany-munich-nato-rasmussen-publi-image562701489.htmlRM2RKD7DN–Bildnummer: 54881674 Datum: 04.02.2011 Copyright: imago/Xinhua (110204) -- MUNICH, Feb. 4, 2011 (Xinhua) -- NATO Secretary-General Anders Fogh Rasmussen speaks to the press during the 47th Munich Security Conference (MSC) in Munich, Germany, Feb. 4, 2011. The MSC kicked off here on Friday, during which 350 world leaders and diplomats will discuss major global security issues, including financial crisis, cyber war, transatlantic security, NATO-Russia relationship, non-proliferation of mass destruction arms, Afghanistan and Middle East. (Xinhua/Luo Huanhuan) GERMANY-MUNICH-NATO-RASMUSSEN PUBLI
 cyber war on database with bullets in front of white Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-cyber-war-on-database-with-bullets-in-front-of-white-54619842.html
cyber war on database with bullets in front of white Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-cyber-war-on-database-with-bullets-in-front-of-white-54619842.htmlRMD4T44J–cyber war on database with bullets in front of white
 Cyber Warfare, Cyberwarfare, Cyber Attack, Cyberattack, Cyberterrorism, Cyber war, Cyber propaganda, Cyber activities, Cyber counterintelligence Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-warfare-cyberwarfare-cyber-attack-cyberattack-cyberterrorism-cyber-war-cyber-propaganda-cyber-activities-cyber-counterintelligence-image405290201.html
Cyber Warfare, Cyberwarfare, Cyber Attack, Cyberattack, Cyberterrorism, Cyber war, Cyber propaganda, Cyber activities, Cyber counterintelligence Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-warfare-cyberwarfare-cyber-attack-cyberattack-cyberterrorism-cyber-war-cyber-propaganda-cyber-activities-cyber-counterintelligence-image405290201.htmlRM2EFAFP1–Cyber Warfare, Cyberwarfare, Cyber Attack, Cyberattack, Cyberterrorism, Cyber war, Cyber propaganda, Cyber activities, Cyber counterintelligence
 Conceptual caption Cyber Warfare. Concept meaning Virtual War Hackers System Attacks Digital Thief Stalker -48675 Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/conceptual-caption-cyber-warfare-concept-meaning-virtual-war-hackers-system-attacks-digital-thief-stalker-48675-image547874554.html
Conceptual caption Cyber Warfare. Concept meaning Virtual War Hackers System Attacks Digital Thief Stalker -48675 Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/conceptual-caption-cyber-warfare-concept-meaning-virtual-war-hackers-system-attacks-digital-thief-stalker-48675-image547874554.htmlRF2PR9RGA–Conceptual caption Cyber Warfare. Concept meaning Virtual War Hackers System Attacks Digital Thief Stalker -48675
 Cyber war and hybrid conflict symbol technology concept. Abstract sign on glitch screens 3d illustration. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-war-and-hybrid-conflict-symbol-technology-concept-abstract-sign-on-glitch-screens-3d-illustration-image637708368.html
Cyber war and hybrid conflict symbol technology concept. Abstract sign on glitch screens 3d illustration. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-war-and-hybrid-conflict-symbol-technology-concept-abstract-sign-on-glitch-screens-3d-illustration-image637708368.htmlRF2S1E3ET–Cyber war and hybrid conflict symbol technology concept. Abstract sign on glitch screens 3d illustration.
 US Military Soldier Smart Phone Espionage. Cyber War Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/us-military-soldier-smart-phone-espionage-cyber-war-image434518811.html
US Military Soldier Smart Phone Espionage. Cyber War Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/us-military-soldier-smart-phone-espionage-cyber-war-image434518811.htmlRF2G6X14Y–US Military Soldier Smart Phone Espionage. Cyber War
 Cyber War Special Forces Fully Armed Soldier Uncovers Internationally Wanted Hacker's Hideout Place. Lair is Full of Monitors, Cables and Has Neon. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-war-special-forces-fully-armed-soldier-uncovers-internationally-wanted-hackers-hideout-place-lair-is-full-of-monitors-cables-and-has-neon-image177830422.html
Cyber War Special Forces Fully Armed Soldier Uncovers Internationally Wanted Hacker's Hideout Place. Lair is Full of Monitors, Cables and Has Neon. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-war-special-forces-fully-armed-soldier-uncovers-internationally-wanted-hackers-hideout-place-lair-is-full-of-monitors-cables-and-has-neon-image177830422.htmlRFM98TEE–Cyber War Special Forces Fully Armed Soldier Uncovers Internationally Wanted Hacker's Hideout Place. Lair is Full of Monitors, Cables and Has Neon.
 Computer data cybersecurity, cyber war future concept Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/computer-data-cybersecurity-cyber-war-future-concept-image261199677.html
Computer data cybersecurity, cyber war future concept Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/computer-data-cybersecurity-cyber-war-future-concept-image261199677.htmlRFW4XJRW–Computer data cybersecurity, cyber war future concept
 Spielzeugsoldaten auf einer Platine, Motherboard eines Computers, Symbolbild fuer Cyberkrieg und Cyberangriff, Studioaufnahme, Koeln Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/spielzeugsoldaten-auf-einer-platine-motherboard-eines-computers-symbolbild-fuer-cyberkrieg-und-cyberangriff-studioaufnahme-koeln-image469024212.html
Spielzeugsoldaten auf einer Platine, Motherboard eines Computers, Symbolbild fuer Cyberkrieg und Cyberangriff, Studioaufnahme, Koeln Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/spielzeugsoldaten-auf-einer-platine-motherboard-eines-computers-symbolbild-fuer-cyberkrieg-und-cyberangriff-studioaufnahme-koeln-image469024212.htmlRF2J71W4M–Spielzeugsoldaten auf einer Platine, Motherboard eines Computers, Symbolbild fuer Cyberkrieg und Cyberangriff, Studioaufnahme, Koeln
 Word writing text Cyber Warfare. Business concept for Virtual War Hackers System Attacks Digital Thief Stalker White pc keyboard Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/word-writing-text-cyber-warfare-business-concept-for-virtual-war-hackers-system-attacks-digital-thief-stalker-white-pc-keyboard-image343859659.html
Word writing text Cyber Warfare. Business concept for Virtual War Hackers System Attacks Digital Thief Stalker White pc keyboard Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/word-writing-text-cyber-warfare-business-concept-for-virtual-war-hackers-system-attacks-digital-thief-stalker-white-pc-keyboard-image343859659.htmlRM2AYC4E3–Word writing text Cyber Warfare. Business concept for Virtual War Hackers System Attacks Digital Thief Stalker White pc keyboard
 Cold War Espionage Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-cold-war-espionage-124787234.html
Cold War Espionage Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-cold-war-espionage-124787234.htmlRFH70FAX–Cold War Espionage
 Binary code displayed on a laptop screen and Guy Fawkes mask are seen in this illustration photo taken in Krakow, Poland on March 1, 2022. Global hacker group Anonymous declared 'cyber war' against Russia. (Photo by Jakub Porzycki/NurPhoto) Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/binary-code-displayed-on-a-laptop-screen-and-guy-fawkes-mask-are-seen-in-this-illustration-photo-taken-in-krakow-poland-on-march-1-2022-global-hacker-group-anonymous-declared-cyber-war-against-russia-photo-by-jakub-porzyckinurphoto-image489969323.html
Binary code displayed on a laptop screen and Guy Fawkes mask are seen in this illustration photo taken in Krakow, Poland on March 1, 2022. Global hacker group Anonymous declared 'cyber war' against Russia. (Photo by Jakub Porzycki/NurPhoto) Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/binary-code-displayed-on-a-laptop-screen-and-guy-fawkes-mask-are-seen-in-this-illustration-photo-taken-in-krakow-poland-on-march-1-2022-global-hacker-group-anonymous-declared-cyber-war-against-russia-photo-by-jakub-porzyckinurphoto-image489969323.htmlRM2KD40TB–Binary code displayed on a laptop screen and Guy Fawkes mask are seen in this illustration photo taken in Krakow, Poland on March 1, 2022. Global hacker group Anonymous declared 'cyber war' against Russia. (Photo by Jakub Porzycki/NurPhoto)
 Anonymous Hacker commits cyber crime with laptop held in hand Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/anonymous-hacker-commits-cyber-crime-with-laptop-held-in-hand-image465940545.html
Anonymous Hacker commits cyber crime with laptop held in hand Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/anonymous-hacker-commits-cyber-crime-with-laptop-held-in-hand-image465940545.htmlRF2J21BWN–Anonymous Hacker commits cyber crime with laptop held in hand
 War machine against white background closeup Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/war-machine-against-white-background-closeup-image682894915.html
War machine against white background closeup Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/war-machine-against-white-background-closeup-image682894915.htmlRF3BK0FC3–War machine against white background closeup
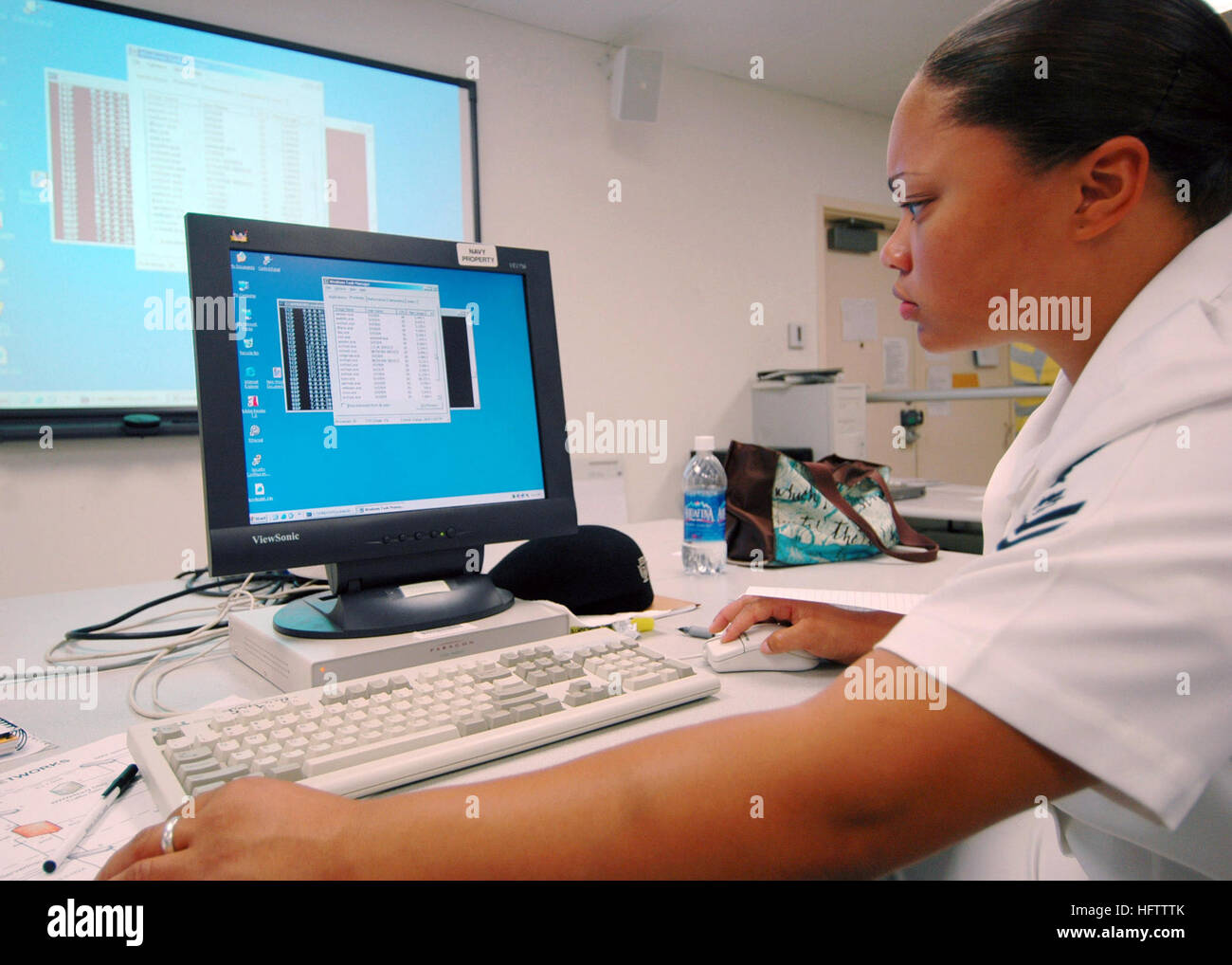 070712-N-9758L-048 PEARL CITY, Hawaii (July 12, 2007) Ð Information Systems Technician 2nd Class Athena Stovall, assigned to Commander U.S. 3rd Fleet in San Diego, scans the network on her computer for intrusions during a cyber war training course at the Space and Naval Warfare Systems Center. The course is designed to improve how military members would act in a real-life cyber war environment by defending the networks with sweeps and scans of the system as well as responding to intrusions, such as viruses and probes. U.S. Navy photo by Mass Communication Specialist 3rd Class Michael A. Lantro Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-070712-n-9758l-048-pearl-city-hawaii-july-12-2007-information-systems-130238771.html
070712-N-9758L-048 PEARL CITY, Hawaii (July 12, 2007) Ð Information Systems Technician 2nd Class Athena Stovall, assigned to Commander U.S. 3rd Fleet in San Diego, scans the network on her computer for intrusions during a cyber war training course at the Space and Naval Warfare Systems Center. The course is designed to improve how military members would act in a real-life cyber war environment by defending the networks with sweeps and scans of the system as well as responding to intrusions, such as viruses and probes. U.S. Navy photo by Mass Communication Specialist 3rd Class Michael A. Lantro Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-070712-n-9758l-048-pearl-city-hawaii-july-12-2007-information-systems-130238771.htmlRMHFTTTK–070712-N-9758L-048 PEARL CITY, Hawaii (July 12, 2007) Ð Information Systems Technician 2nd Class Athena Stovall, assigned to Commander U.S. 3rd Fleet in San Diego, scans the network on her computer for intrusions during a cyber war training course at the Space and Naval Warfare Systems Center. The course is designed to improve how military members would act in a real-life cyber war environment by defending the networks with sweeps and scans of the system as well as responding to intrusions, such as viruses and probes. U.S. Navy photo by Mass Communication Specialist 3rd Class Michael A. Lantro
 Signs representing issues with modern elections, the hacking of accounts and leaking of information, at the US Capitol Building, Washington DC, USA Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-signs-representing-issues-with-modern-elections-the-hacking-of-accounts-142493900.html
Signs representing issues with modern elections, the hacking of accounts and leaking of information, at the US Capitol Building, Washington DC, USA Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-signs-representing-issues-with-modern-elections-the-hacking-of-accounts-142493900.htmlRFJ7R4BT–Signs representing issues with modern elections, the hacking of accounts and leaking of information, at the US Capitol Building, Washington DC, USA
 Hybrid and Cyber War Concept. Microchip CPU Processors with Circuit and USA and Russia Flags on a white background. 3d Rendering Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/hybrid-and-cyber-war-concept-microchip-cpu-processors-with-circuit-and-usa-and-russia-flags-on-a-white-background-3d-rendering-image468486574.html
Hybrid and Cyber War Concept. Microchip CPU Processors with Circuit and USA and Russia Flags on a white background. 3d Rendering Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/hybrid-and-cyber-war-concept-microchip-cpu-processors-with-circuit-and-usa-and-russia-flags-on-a-white-background-3d-rendering-image468486574.htmlRF2J65BBA–Hybrid and Cyber War Concept. Microchip CPU Processors with Circuit and USA and Russia Flags on a white background. 3d Rendering
 Woman hacker data breach China vs Russia cyber war Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/woman-hacker-data-breach-china-vs-russia-cyber-war-image345103149.html
Woman hacker data breach China vs Russia cyber war Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/woman-hacker-data-breach-china-vs-russia-cyber-war-image345103149.htmlRF2B1CPGD–Woman hacker data breach China vs Russia cyber war
 Chinese students compete in a cyber war-game contest in downtown Beijing on August 26, 2012. Cyber crime in China poses a serious threat to the fast-growing economy and it is likely that such attacks, already costing in excess of US$850 billion a year, will only increase. UPI/Stephen Shaver Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/chinese-students-compete-in-a-cyber-war-game-contest-in-downtown-beijing-on-august-26-2012-cyber-crime-in-china-poses-a-serious-threat-to-the-fast-growing-economy-and-it-is-likely-that-such-attacks-already-costing-in-excess-of-us850-billion-a-year-will-only-increase-upistephen-shaver-image258178707.html
Chinese students compete in a cyber war-game contest in downtown Beijing on August 26, 2012. Cyber crime in China poses a serious threat to the fast-growing economy and it is likely that such attacks, already costing in excess of US$850 billion a year, will only increase. UPI/Stephen Shaver Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/chinese-students-compete-in-a-cyber-war-game-contest-in-downtown-beijing-on-august-26-2012-cyber-crime-in-china-poses-a-serious-threat-to-the-fast-growing-economy-and-it-is-likely-that-such-attacks-already-costing-in-excess-of-us850-billion-a-year-will-only-increase-upistephen-shaver-image258178707.htmlRMW011G3–Chinese students compete in a cyber war-game contest in downtown Beijing on August 26, 2012. Cyber crime in China poses a serious threat to the fast-growing economy and it is likely that such attacks, already costing in excess of US$850 billion a year, will only increase. UPI/Stephen Shaver
 Bildnummer: 54881673 Datum: 04.02.2011 Copyright: imago/Xinhua (110204) -- MUNICH, Feb. 4, 2011 (Xinhua) -- NATO Secretary-General Anders Fogh Rasmussen speaks to the press during the 47th Munich Security Conference (MSC) in Munich, Germany, Feb. 4, 2011. The MSC kicked off here on Friday, during which 350 world leaders and diplomats will discuss major global security issues, including financial crisis, cyber war, transatlantic security, NATO-Russia relationship, non-proliferation of mass destruction arms, Afghanistan and Middle East. (Xinhua/Luo Huanhuan) GERMANY-MUNICH-NATO-RASMUSSEN PUBLI Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/bildnummer-54881673-datum-04022011-copyright-imagoxinhua-110204-munich-feb-4-2011-xinhua-nato-secretary-general-anders-fogh-rasmussen-speaks-to-the-press-during-the-47th-munich-security-conference-msc-in-munich-germany-feb-4-2011-the-msc-kicked-off-here-on-friday-during-which-350-world-leaders-and-diplomats-will-discuss-major-global-security-issues-including-financial-crisis-cyber-war-transatlantic-security-nato-russia-relationship-non-proliferation-of-mass-destruction-arms-afghanistan-and-middle-east-xinhualuo-huanhuan-germany-munich-nato-rasmussen-publi-image562701539.html
Bildnummer: 54881673 Datum: 04.02.2011 Copyright: imago/Xinhua (110204) -- MUNICH, Feb. 4, 2011 (Xinhua) -- NATO Secretary-General Anders Fogh Rasmussen speaks to the press during the 47th Munich Security Conference (MSC) in Munich, Germany, Feb. 4, 2011. The MSC kicked off here on Friday, during which 350 world leaders and diplomats will discuss major global security issues, including financial crisis, cyber war, transatlantic security, NATO-Russia relationship, non-proliferation of mass destruction arms, Afghanistan and Middle East. (Xinhua/Luo Huanhuan) GERMANY-MUNICH-NATO-RASMUSSEN PUBLI Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/bildnummer-54881673-datum-04022011-copyright-imagoxinhua-110204-munich-feb-4-2011-xinhua-nato-secretary-general-anders-fogh-rasmussen-speaks-to-the-press-during-the-47th-munich-security-conference-msc-in-munich-germany-feb-4-2011-the-msc-kicked-off-here-on-friday-during-which-350-world-leaders-and-diplomats-will-discuss-major-global-security-issues-including-financial-crisis-cyber-war-transatlantic-security-nato-russia-relationship-non-proliferation-of-mass-destruction-arms-afghanistan-and-middle-east-xinhualuo-huanhuan-germany-munich-nato-rasmussen-publi-image562701539.htmlRM2RKD7FF–Bildnummer: 54881673 Datum: 04.02.2011 Copyright: imago/Xinhua (110204) -- MUNICH, Feb. 4, 2011 (Xinhua) -- NATO Secretary-General Anders Fogh Rasmussen speaks to the press during the 47th Munich Security Conference (MSC) in Munich, Germany, Feb. 4, 2011. The MSC kicked off here on Friday, during which 350 world leaders and diplomats will discuss major global security issues, including financial crisis, cyber war, transatlantic security, NATO-Russia relationship, non-proliferation of mass destruction arms, Afghanistan and Middle East. (Xinhua/Luo Huanhuan) GERMANY-MUNICH-NATO-RASMUSSEN PUBLI