Quick filters:
Data privacy awareness Stock Photos and Images
 Executive Director Pushing DATA PRIVACY AWARENESS Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-image-executive-director-pushing-data-privacy-awareness-168907688.html
Executive Director Pushing DATA PRIVACY AWARENESS Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-image-executive-director-pushing-data-privacy-awareness-168907688.htmlRFKPPBDC–Executive Director Pushing DATA PRIVACY AWARENESS
 A blue padlock rests on a laptop keyboard, with a red light shining from the background. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/a-blue-padlock-rests-on-a-laptop-keyboard-with-a-red-light-shining-from-the-background-image612884697.html
A blue padlock rests on a laptop keyboard, with a red light shining from the background. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/a-blue-padlock-rests-on-a-laptop-keyboard-with-a-red-light-shining-from-the-background-image612884697.htmlRF2XH38K5–A blue padlock rests on a laptop keyboard, with a red light shining from the background.
RFKDTHNJ–Cyber Awareness Icon with Red Border
 Safety on the Computer - Computer Safety Concepts Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-safety-on-the-computer-computer-safety-concepts-173193988.html
Safety on the Computer - Computer Safety Concepts Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-safety-on-the-computer-computer-safety-concepts-173193988.htmlRFM1NJKG–Safety on the Computer - Computer Safety Concepts
 The image can be used in various contexts, such as educational materials, websites, or presentations related to digital safety, password protection, a Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/the-image-can-be-used-in-various-contexts-such-as-educational-materials-websites-or-presentations-related-to-digital-safety-password-protection-a-image573652341.html
The image can be used in various contexts, such as educational materials, websites, or presentations related to digital safety, password protection, a Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/the-image-can-be-used-in-various-contexts-such-as-educational-materials-websites-or-presentations-related-to-digital-safety-password-protection-a-image573652341.htmlRF2T983BH–The image can be used in various contexts, such as educational materials, websites, or presentations related to digital safety, password protection, a
 Face recognition signs and tags on people faces. Privacy and personal data protection. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/face-recognition-signs-and-tags-on-people-faces-privacy-and-personal-data-protection-image452241834.html
Face recognition signs and tags on people faces. Privacy and personal data protection. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/face-recognition-signs-and-tags-on-people-faces-privacy-and-personal-data-protection-image452241834.htmlRF2H7NB22–Face recognition signs and tags on people faces. Privacy and personal data protection.
 Business, Technology, Internet and network concept. Young woman holding a sign with an inscription Security Awareness Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/business-technology-internet-and-network-concept-young-woman-holding-image157533556.html
Business, Technology, Internet and network concept. Young woman holding a sign with an inscription Security Awareness Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/business-technology-internet-and-network-concept-young-woman-holding-image157533556.htmlRFK487JC–Business, Technology, Internet and network concept. Young woman holding a sign with an inscription Security Awareness
 Jason Nurse , Assistant professor at the University of Kent, presenting a talk entitled 'Online data and the pursuit of privacy', on the Technology Stage, at New Scientist Live 2019 Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/jason-nurse-assistant-professor-at-the-university-of-kent-presenting-a-talk-entitled-online-data-and-the-pursuit-of-privacy-on-the-technology-stage-at-new-scientist-live-2019-image331572882.html
Jason Nurse , Assistant professor at the University of Kent, presenting a talk entitled 'Online data and the pursuit of privacy', on the Technology Stage, at New Scientist Live 2019 Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/jason-nurse-assistant-professor-at-the-university-of-kent-presenting-a-talk-entitled-online-data-and-the-pursuit-of-privacy-on-the-technology-stage-at-new-scientist-live-2019-image331572882.htmlRM2A7CCGJ–Jason Nurse , Assistant professor at the University of Kent, presenting a talk entitled 'Online data and the pursuit of privacy', on the Technology Stage, at New Scientist Live 2019
 Smartphone protection with two factor authentication. Cybersecurity and data privacy in digital realm Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/smartphone-protection-with-two-factor-authentication-cybersecurity-and-data-privacy-in-digital-realm-image439546290.html
Smartphone protection with two factor authentication. Cybersecurity and data privacy in digital realm Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/smartphone-protection-with-two-factor-authentication-cybersecurity-and-data-privacy-in-digital-realm-image439546290.htmlRF2GF31NP–Smartphone protection with two factor authentication. Cybersecurity and data privacy in digital realm
 Writing note showing Data Privacy Awareness. Business photo showcasing Respecting privacy and protect what we share online Digital Combination of Colu Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/writing-note-showing-data-privacy-awareness-business-photo-showcasing-respecting-privacy-and-protect-what-we-share-online-digital-combination-of-colu-image232742183.html
Writing note showing Data Privacy Awareness. Business photo showcasing Respecting privacy and protect what we share online Digital Combination of Colu Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/writing-note-showing-data-privacy-awareness-business-photo-showcasing-respecting-privacy-and-protect-what-we-share-online-digital-combination-of-colu-image232742183.htmlRFREJ90R–Writing note showing Data Privacy Awareness. Business photo showcasing Respecting privacy and protect what we share online Digital Combination of Colu
 Download privacy Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/download-privacy-image343625258.html
Download privacy Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/download-privacy-image343625258.htmlRM2AY1DEJ–Download privacy
RF2XP0NC7–Image of data processing and padlock icon over dark background
 Flower with human eye Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-flower-with-human-eye-57972852.html
Flower with human eye Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-flower-with-human-eye-57972852.htmlRMDA8TY0–Flower with human eye
 Hand turns dice and changes the expression 'no privacy' to 'data privacy'. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/hand-turns-dice-and-changes-the-expression-no-privacy-to-data-privacy-image393921004.html
Hand turns dice and changes the expression 'no privacy' to 'data privacy'. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/hand-turns-dice-and-changes-the-expression-no-privacy-to-data-privacy-image393921004.htmlRF2DTTJ78–Hand turns dice and changes the expression 'no privacy' to 'data privacy'.
 Virtual display button: Security Awareness Business, Technology, Internet and network concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/virtual-display-button-security-awareness-business-technology-internet-and-network-concept-image526860773.html
Virtual display button: Security Awareness Business, Technology, Internet and network concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/virtual-display-button-security-awareness-business-technology-internet-and-network-concept-image526860773.htmlRF2NH4G85–Virtual display button: Security Awareness Business, Technology, Internet and network concept
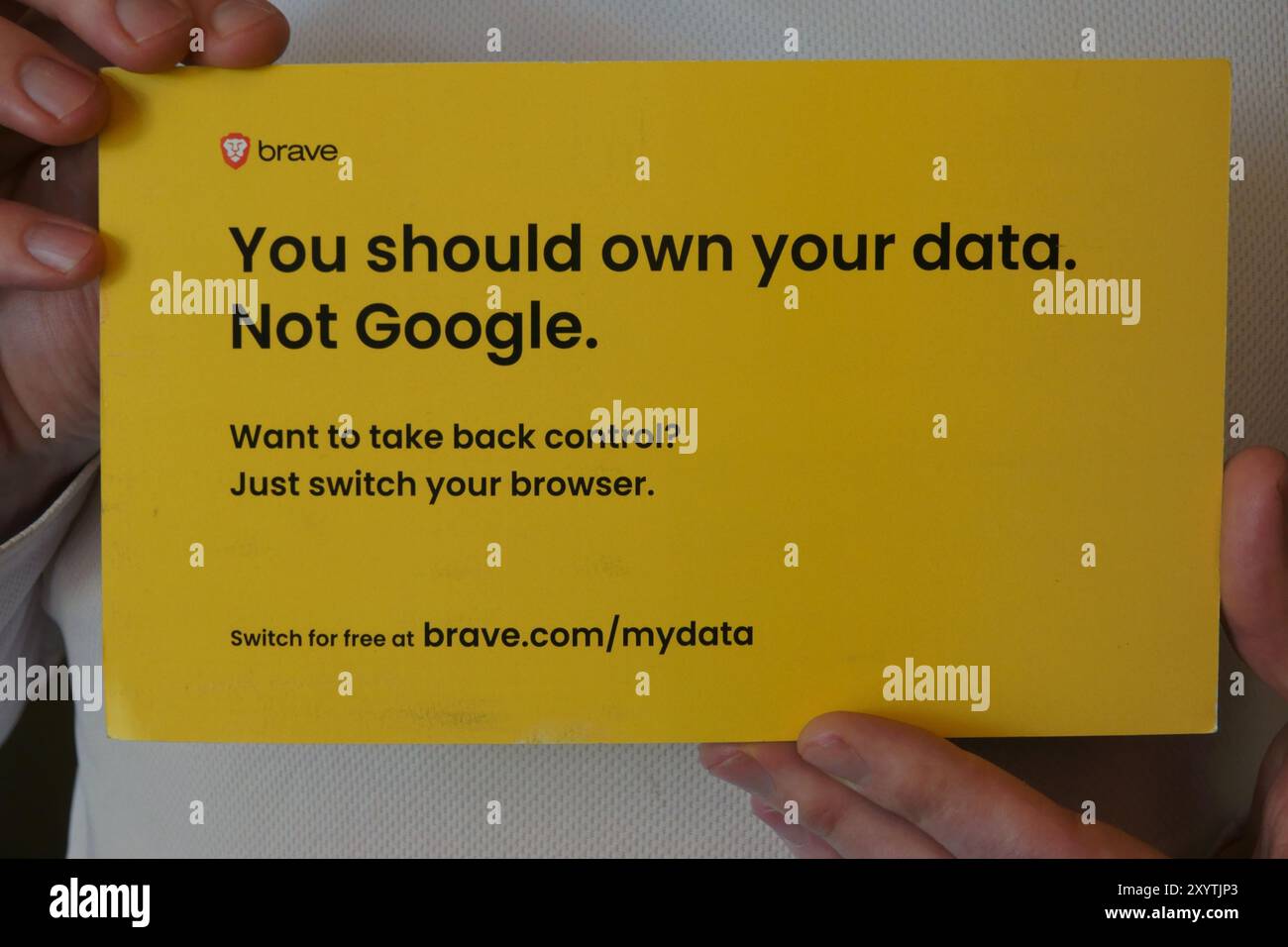 Los Angeles, California, USA - Jan. 15, 2024: A Brave internet browser advertising mailer is shown, reading “You should own your data. Not Google.' Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/los-angeles-california-usa-jan-15-2024-a-brave-internet-browser-advertising-mailer-is-shown-reading-you-should-own-your-data-not-google-image619500171.html
Los Angeles, California, USA - Jan. 15, 2024: A Brave internet browser advertising mailer is shown, reading “You should own your data. Not Google.' Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/los-angeles-california-usa-jan-15-2024-a-brave-internet-browser-advertising-mailer-is-shown-reading-you-should-own-your-data-not-google-image619500171.htmlRF2XYTJP3–Los Angeles, California, USA - Jan. 15, 2024: A Brave internet browser advertising mailer is shown, reading “You should own your data. Not Google.'
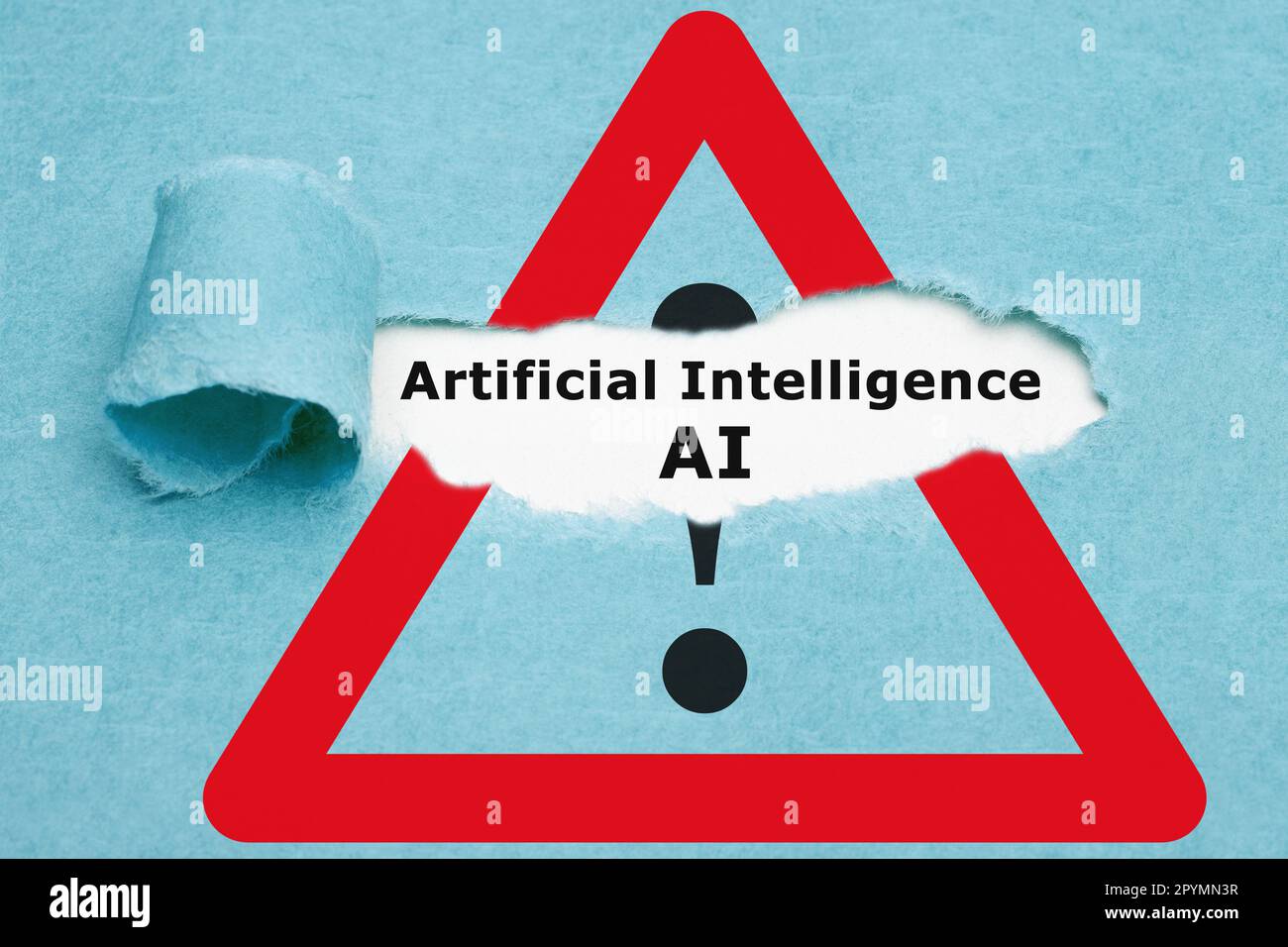 Text Artificial Intelligence AI appearing behind ripped blue paper on attention sign. Concept about safety, security, privacy, and the risks of using Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/text-artificial-intelligence-ai-appearing-behind-ripped-blue-paper-on-attention-sign-concept-about-safety-security-privacy-and-the-risks-of-using-image550572731.html
Text Artificial Intelligence AI appearing behind ripped blue paper on attention sign. Concept about safety, security, privacy, and the risks of using Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/text-artificial-intelligence-ai-appearing-behind-ripped-blue-paper-on-attention-sign-concept-about-safety-security-privacy-and-the-risks-of-using-image550572731.htmlRF2PYMN3R–Text Artificial Intelligence AI appearing behind ripped blue paper on attention sign. Concept about safety, security, privacy, and the risks of using
 One person is answering question about data privacy. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/one-person-is-answering-question-about-data-privacy-image398184529.html
One person is answering question about data privacy. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/one-person-is-answering-question-about-data-privacy-image398184529.htmlRF2E3PTC1–One person is answering question about data privacy.
 Data privacy day message written on asphalt road. Conceptual data privacy day symbol. Copy space. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/data-privacy-day-message-written-on-asphalt-road-conceptual-data-privacy-day-symbol-copy-space-image632724714.html
Data privacy day message written on asphalt road. Conceptual data privacy day symbol. Copy space. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/data-privacy-day-message-written-on-asphalt-road-conceptual-data-privacy-day-symbol-copy-space-image632724714.htmlRF2YNB2R6–Data privacy day message written on asphalt road. Conceptual data privacy day symbol. Copy space.
 Sign displaying Data Theft. Concept meaning illegal transfer of any information that is confidential Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/sign-displaying-data-theft-concept-meaning-illegal-transfer-of-any-information-that-is-confidential-image550248833.html
Sign displaying Data Theft. Concept meaning illegal transfer of any information that is confidential Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/sign-displaying-data-theft-concept-meaning-illegal-transfer-of-any-information-that-is-confidential-image550248833.htmlRF2PY6001–Sign displaying Data Theft. Concept meaning illegal transfer of any information that is confidential
 Conceptual display Privacy Policy, Business showcase Documentation regarding the management of the client s is data Prescribed Medicine Vitamines And Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/conceptual-display-privacy-policy-business-showcase-documentation-regarding-the-management-of-the-client-s-is-data-prescribed-medicine-vitamines-and-image447022715.html
Conceptual display Privacy Policy, Business showcase Documentation regarding the management of the client s is data Prescribed Medicine Vitamines And Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/conceptual-display-privacy-policy-business-showcase-documentation-regarding-the-management-of-the-client-s-is-data-prescribed-medicine-vitamines-and-image447022715.htmlRF2GY7J0Y–Conceptual display Privacy Policy, Business showcase Documentation regarding the management of the client s is data Prescribed Medicine Vitamines And
 Cyber Security Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-image-cyber-security-163424628.html
Cyber Security Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-image-cyber-security-163424628.htmlRFKDTHNT–Cyber Security
 January 28. Hand writing text Data Privacy Day on calendar date. Save the date. Holiday. Day of the year concept. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/january-28-hand-writing-text-data-privacy-day-on-calendar-date-save-the-date-holiday-day-of-the-year-concept-image575291032.html
January 28. Hand writing text Data Privacy Day on calendar date. Save the date. Holiday. Day of the year concept. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/january-28-hand-writing-text-data-privacy-day-on-calendar-date-save-the-date-holiday-day-of-the-year-concept-image575291032.htmlRF2TBXNG8–January 28. Hand writing text Data Privacy Day on calendar date. Save the date. Holiday. Day of the year concept.
 Cyber security and information or network protection. Cyber Technology Web Services for Business. Phishing, mobile phone hacker or cyber scam conc Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-security-and-information-or-network-protection-cyber-technology-web-services-for-business-phishing-mobile-phone-hacker-or-cyber-scam-conc-image573652336.html
Cyber security and information or network protection. Cyber Technology Web Services for Business. Phishing, mobile phone hacker or cyber scam conc Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-security-and-information-or-network-protection-cyber-technology-web-services-for-business-phishing-mobile-phone-hacker-or-cyber-scam-conc-image573652336.htmlRF2T983BC–Cyber security and information or network protection. Cyber Technology Web Services for Business. Phishing, mobile phone hacker or cyber scam conc
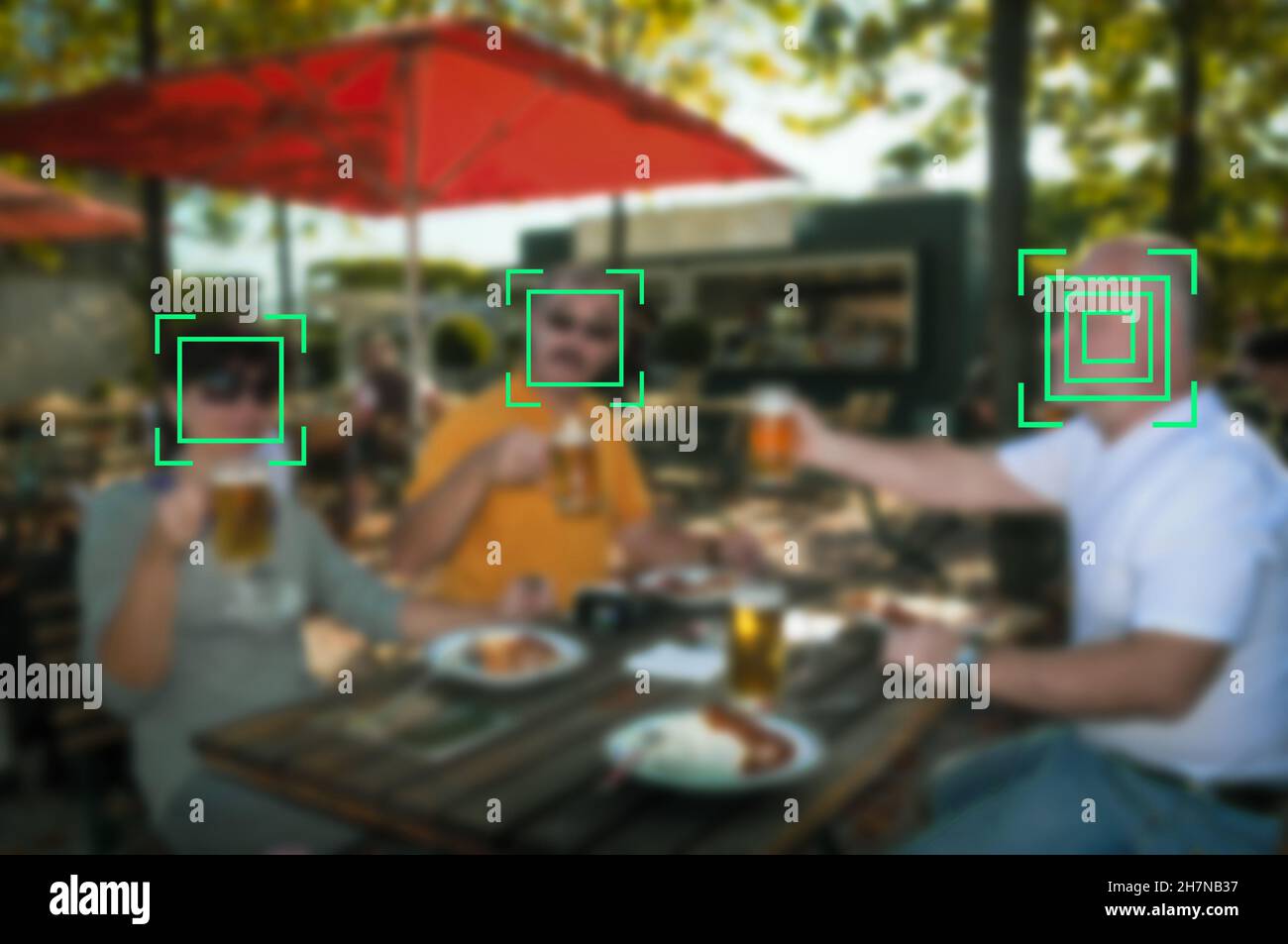 Face recognition signs and tags on people faces. Privacy and personal data protection. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/face-recognition-signs-and-tags-on-people-faces-privacy-and-personal-data-protection-image452241867.html
Face recognition signs and tags on people faces. Privacy and personal data protection. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/face-recognition-signs-and-tags-on-people-faces-privacy-and-personal-data-protection-image452241867.htmlRF2H7NB37–Face recognition signs and tags on people faces. Privacy and personal data protection.
 A metal padlock sits on a laptop keyboard, illuminated by blue and yellow light. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/a-metal-padlock-sits-on-a-laptop-keyboard-illuminated-by-blue-and-yellow-light-image612884695.html
A metal padlock sits on a laptop keyboard, illuminated by blue and yellow light. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/a-metal-padlock-sits-on-a-laptop-keyboard-illuminated-by-blue-and-yellow-light-image612884695.htmlRF2XH38K3–A metal padlock sits on a laptop keyboard, illuminated by blue and yellow light.
 Jason Nurse , Assistant professor at the University of Kent, presenting a talk entitled 'Online data and the pursuit of privacy', on the Technology Stage, at New Scientist Live 2019 Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/jason-nurse-assistant-professor-at-the-university-of-kent-presenting-a-talk-entitled-online-data-and-the-pursuit-of-privacy-on-the-technology-stage-at-new-scientist-live-2019-image331572776.html
Jason Nurse , Assistant professor at the University of Kent, presenting a talk entitled 'Online data and the pursuit of privacy', on the Technology Stage, at New Scientist Live 2019 Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/jason-nurse-assistant-professor-at-the-university-of-kent-presenting-a-talk-entitled-online-data-and-the-pursuit-of-privacy-on-the-technology-stage-at-new-scientist-live-2019-image331572776.htmlRM2A7CCCT–Jason Nurse , Assistant professor at the University of Kent, presenting a talk entitled 'Online data and the pursuit of privacy', on the Technology Stage, at New Scientist Live 2019
 Faceless young female browsing smartphone while typing on laptop. Millennial data privacy concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/faceless-young-female-browsing-smartphone-while-typing-on-laptop-millennial-data-privacy-concept-image439546567.html
Faceless young female browsing smartphone while typing on laptop. Millennial data privacy concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/faceless-young-female-browsing-smartphone-while-typing-on-laptop-millennial-data-privacy-concept-image439546567.htmlRF2GF323K–Faceless young female browsing smartphone while typing on laptop. Millennial data privacy concept
 Handwriting text Data Privacy Awareness. Concept meaning Respecting privacy and protect what we share online Drawn Hu analysis Hand Holding Presenting Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/handwriting-text-data-privacy-awareness-concept-meaning-respecting-privacy-and-protect-what-we-share-online-drawn-hu-analysis-hand-holding-presenting-image232771559.html
Handwriting text Data Privacy Awareness. Concept meaning Respecting privacy and protect what we share online Drawn Hu analysis Hand Holding Presenting Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/handwriting-text-data-privacy-awareness-concept-meaning-respecting-privacy-and-protect-what-we-share-online-drawn-hu-analysis-hand-holding-presenting-image232771559.htmlRFREKJDY–Handwriting text Data Privacy Awareness. Concept meaning Respecting privacy and protect what we share online Drawn Hu analysis Hand Holding Presenting
 Data privacy, data wellbeing, management, personal information, digital identity, digital behavior, security issue, data hygiene, cybersecurity Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/data-privacy-data-wellbeing-management-personal-information-digital-identity-digital-behavior-security-issue-data-hygiene-cybersecurity-image437455997.html
Data privacy, data wellbeing, management, personal information, digital identity, digital behavior, security issue, data hygiene, cybersecurity Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/data-privacy-data-wellbeing-management-personal-information-digital-identity-digital-behavior-security-issue-data-hygiene-cybersecurity-image437455997.htmlRF2GBKRGD–Data privacy, data wellbeing, management, personal information, digital identity, digital behavior, security issue, data hygiene, cybersecurity
RF2Y8089H–Image of padlock icons and digital data processing over computer servers
RFKCC9PY–Young businesswoman working in virtual glasses, select the icon Security Awareness on the virtual display
 Hand turns dice and changes the German expression 'kein Schutz' (no protection) to 'Datenschutz' (data privacy). Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/hand-turns-dice-and-changes-the-german-expression-kein-schutz-no-protection-to-datenschutz-data-privacy-image393920907.html
Hand turns dice and changes the German expression 'kein Schutz' (no protection) to 'Datenschutz' (data privacy). Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/hand-turns-dice-and-changes-the-german-expression-kein-schutz-no-protection-to-datenschutz-data-privacy-image393920907.htmlRF2DTTJ3R–Hand turns dice and changes the German expression 'kein Schutz' (no protection) to 'Datenschutz' (data privacy).
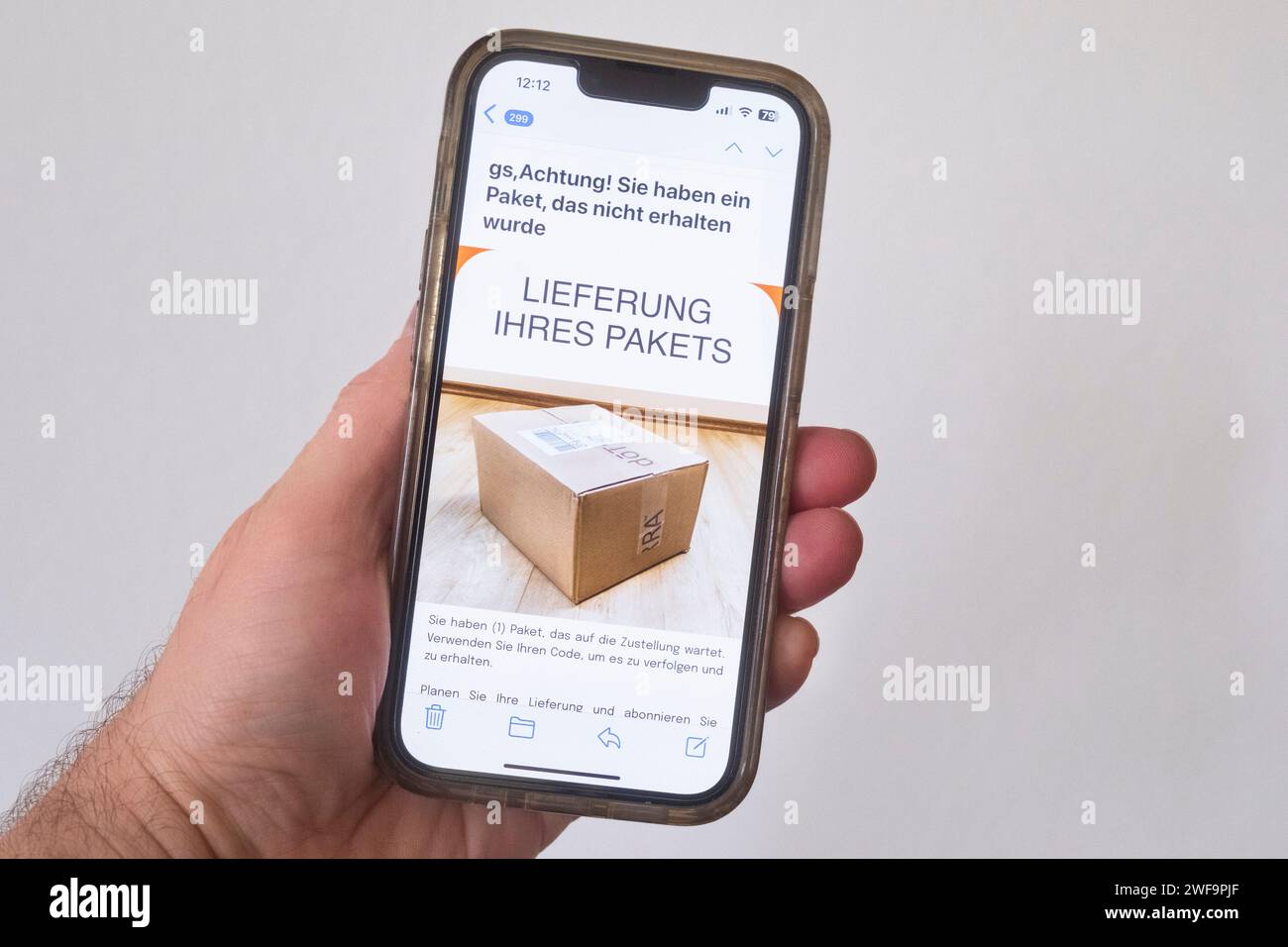 Phishing e-mail: Fraudsters want to steal sensitive data and small amounts. Hand holding a mobile phone on which a fraudulent phishing mail can be see Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/phishing-e-mail-fraudsters-want-to-steal-sensitive-data-and-small-amounts-hand-holding-a-mobile-phone-on-which-a-fraudulent-phishing-mail-can-be-see-image594587687.html
Phishing e-mail: Fraudsters want to steal sensitive data and small amounts. Hand holding a mobile phone on which a fraudulent phishing mail can be see Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/phishing-e-mail-fraudsters-want-to-steal-sensitive-data-and-small-amounts-hand-holding-a-mobile-phone-on-which-a-fraudulent-phishing-mail-can-be-see-image594587687.htmlRM2WF9PJF–Phishing e-mail: Fraudsters want to steal sensitive data and small amounts. Hand holding a mobile phone on which a fraudulent phishing mail can be see
 Young African Businessman with a laptop outdoors talks to clients remotely, educates customers on cyber security. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/young-african-businessman-with-a-laptop-outdoors-talks-to-clients-remotely-educates-customers-on-cyber-security-image538423753.html
Young African Businessman with a laptop outdoors talks to clients remotely, educates customers on cyber security. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/young-african-businessman-with-a-laptop-outdoors-talks-to-clients-remotely-educates-customers-on-cyber-security-image538423753.htmlRF2P7Y8YN–Young African Businessman with a laptop outdoors talks to clients remotely, educates customers on cyber security.
 Hand drawing AI Artificial Intelligence prohibition sign concept with marker isolated on white background. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/hand-drawing-ai-artificial-intelligence-prohibition-sign-concept-with-marker-isolated-on-white-background-image558708657.html
Hand drawing AI Artificial Intelligence prohibition sign concept with marker isolated on white background. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/hand-drawing-ai-artificial-intelligence-prohibition-sign-concept-with-marker-isolated-on-white-background-image558708657.htmlRF2RCYAGH–Hand drawing AI Artificial Intelligence prohibition sign concept with marker isolated on white background.
 One person is answering question about data privacy. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/one-person-is-answering-question-about-data-privacy-image398184530.html
One person is answering question about data privacy. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/one-person-is-answering-question-about-data-privacy-image398184530.htmlRF2E3PTC2–One person is answering question about data privacy.
 Data privacy day message written on wooden blocks with blue background. Conceptual data privacy day symbol. Copy space. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/data-privacy-day-message-written-on-wooden-blocks-with-blue-background-conceptual-data-privacy-day-symbol-copy-space-image635017382.html
Data privacy day message written on wooden blocks with blue background. Conceptual data privacy day symbol. Copy space. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/data-privacy-day-message-written-on-wooden-blocks-with-blue-background-conceptual-data-privacy-day-symbol-copy-space-image635017382.htmlRF2YW3F46–Data privacy day message written on wooden blocks with blue background. Conceptual data privacy day symbol. Copy space.
 Conceptual display Data Theft. Business approach illegal transfer of any information that is confidential Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/conceptual-display-data-theft-business-approach-illegal-transfer-of-any-information-that-is-confidential-image550248288.html
Conceptual display Data Theft. Business approach illegal transfer of any information that is confidential Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/conceptual-display-data-theft-business-approach-illegal-transfer-of-any-information-that-is-confidential-image550248288.htmlRF2PY5Y8G–Conceptual display Data Theft. Business approach illegal transfer of any information that is confidential
 Conceptual caption Privacy Policy, Word for Documentation regarding the management of the client s is data Typing Cooking Instructions And Ingredient Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/conceptual-caption-privacy-policy-word-for-documentation-regarding-the-management-of-the-client-s-is-data-typing-cooking-instructions-and-ingredient-image447084012.html
Conceptual caption Privacy Policy, Word for Documentation regarding the management of the client s is data Typing Cooking Instructions And Ingredient Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/conceptual-caption-privacy-policy-word-for-documentation-regarding-the-management-of-the-client-s-is-data-typing-cooking-instructions-and-ingredient-image447084012.htmlRF2GYAC64–Conceptual caption Privacy Policy, Word for Documentation regarding the management of the client s is data Typing Cooking Instructions And Ingredient
 Locked Keyboard Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-image-locked-keyboard-163424633.html
Locked Keyboard Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-image-locked-keyboard-163424633.htmlRFKDTHP1–Locked Keyboard
 February 1. Hand writing text Change Your Password Day on calendar date. Save the date. Holiday. Day of the year concept. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/february-1-hand-writing-text-change-your-password-day-on-calendar-date-save-the-date-holiday-day-of-the-year-concept-image592656115.html
February 1. Hand writing text Change Your Password Day on calendar date. Save the date. Holiday. Day of the year concept. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/february-1-hand-writing-text-change-your-password-day-on-calendar-date-save-the-date-holiday-day-of-the-year-concept-image592656115.htmlRF2WC5PWR–February 1. Hand writing text Change Your Password Day on calendar date. Save the date. Holiday. Day of the year concept.
 This image is ideal for conveying the importance of online security, safeguarding personal and confidential information, and promoting awareness about Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/this-image-is-ideal-for-conveying-the-importance-of-online-security-safeguarding-personal-and-confidential-information-and-promoting-awareness-about-image573652330.html
This image is ideal for conveying the importance of online security, safeguarding personal and confidential information, and promoting awareness about Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/this-image-is-ideal-for-conveying-the-importance-of-online-security-safeguarding-personal-and-confidential-information-and-promoting-awareness-about-image573652330.htmlRF2T983B6–This image is ideal for conveying the importance of online security, safeguarding personal and confidential information, and promoting awareness about
 Face recognition signs and tags on people faces. Privacy and personal data protection. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/face-recognition-signs-and-tags-on-people-faces-privacy-and-personal-data-protection-image452241789.html
Face recognition signs and tags on people faces. Privacy and personal data protection. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/face-recognition-signs-and-tags-on-people-faces-privacy-and-personal-data-protection-image452241789.htmlRF2H7NB0D–Face recognition signs and tags on people faces. Privacy and personal data protection.
 A red padlock sits on a laptop keyboard, illuminated by blue and red light. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/a-red-padlock-sits-on-a-laptop-keyboard-illuminated-by-blue-and-red-light-image612884840.html
A red padlock sits on a laptop keyboard, illuminated by blue and red light. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/a-red-padlock-sits-on-a-laptop-keyboard-illuminated-by-blue-and-red-light-image612884840.htmlRF2XH38T8–A red padlock sits on a laptop keyboard, illuminated by blue and red light.
 Shredded paper from a waste paper bin Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-shredded-paper-from-a-waste-paper-bin-28007665.html
Shredded paper from a waste paper bin Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-shredded-paper-from-a-waste-paper-bin-28007665.htmlRMBHFT1N–Shredded paper from a waste paper bin
 Employee data privacy at work. Booking and purchasing with credit card online at workspace Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/employee-data-privacy-at-work-booking-and-purchasing-with-credit-card-online-at-workspace-image447950380.html
Employee data privacy at work. Booking and purchasing with credit card online at workspace Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/employee-data-privacy-at-work-booking-and-purchasing-with-credit-card-online-at-workspace-image447950380.htmlRF2H0NW7T–Employee data privacy at work. Booking and purchasing with credit card online at workspace
 Word writing text Data Privacy Awareness. Business concept for Respecting privacy and protect what we share online Blank Oval Outlined Speech Bubble T Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/word-writing-text-data-privacy-awareness-business-concept-for-respecting-privacy-and-protect-what-we-share-online-blank-oval-outlined-speech-bubble-t-image232746117.html
Word writing text Data Privacy Awareness. Business concept for Respecting privacy and protect what we share online Blank Oval Outlined Speech Bubble T Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/word-writing-text-data-privacy-awareness-business-concept-for-respecting-privacy-and-protect-what-we-share-online-blank-oval-outlined-speech-bubble-t-image232746117.htmlRFREJE19–Word writing text Data Privacy Awareness. Business concept for Respecting privacy and protect what we share online Blank Oval Outlined Speech Bubble T
 Data privacy, data wellbeing, management, personal information, digital identity, digital behavior, security issue, data hygiene, cybersecurity Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/data-privacy-data-wellbeing-management-personal-information-digital-identity-digital-behavior-security-issue-data-hygiene-cybersecurity-image437404915.html
Data privacy, data wellbeing, management, personal information, digital identity, digital behavior, security issue, data hygiene, cybersecurity Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/data-privacy-data-wellbeing-management-personal-information-digital-identity-digital-behavior-security-issue-data-hygiene-cybersecurity-image437404915.htmlRF2GBHEC3–Data privacy, data wellbeing, management, personal information, digital identity, digital behavior, security issue, data hygiene, cybersecurity
 Image of hacked text and binary coding data processing over circuit board Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/image-of-hacked-text-and-binary-coding-data-processing-over-circuit-board-image603025115.html
Image of hacked text and binary coding data processing over circuit board Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/image-of-hacked-text-and-binary-coding-data-processing-over-circuit-board-image603025115.htmlRF2X124K7–Image of hacked text and binary coding data processing over circuit board
RFKCC9TF–Young businesswoman working in virtual glasses, select the icon Security Awareness on the virtual display
 Spying on users. Blurred boundaries between personal privacy and data collection. Transparent data usage policies. Cautious about sharing personal inf Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/spying-on-users-blurred-boundaries-between-personal-privacy-and-data-collection-transparent-data-usage-policies-cautious-about-sharing-personal-inf-image563687493.html
Spying on users. Blurred boundaries between personal privacy and data collection. Transparent data usage policies. Cautious about sharing personal inf Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/spying-on-users-blurred-boundaries-between-personal-privacy-and-data-collection-transparent-data-usage-policies-cautious-about-sharing-personal-inf-image563687493.htmlRF2RN2545–Spying on users. Blurred boundaries between personal privacy and data collection. Transparent data usage policies. Cautious about sharing personal inf
 Phishing e-mail: Fraudsters want to steal sensitive data and small amounts. Hand holding a mobile phone on which a fraudulent phishing mail can be see Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/phishing-e-mail-fraudsters-want-to-steal-sensitive-data-and-small-amounts-hand-holding-a-mobile-phone-on-which-a-fraudulent-phishing-mail-can-be-see-image594587689.html
Phishing e-mail: Fraudsters want to steal sensitive data and small amounts. Hand holding a mobile phone on which a fraudulent phishing mail can be see Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/phishing-e-mail-fraudsters-want-to-steal-sensitive-data-and-small-amounts-hand-holding-a-mobile-phone-on-which-a-fraudulent-phishing-mail-can-be-see-image594587689.htmlRM2WF9PJH–Phishing e-mail: Fraudsters want to steal sensitive data and small amounts. Hand holding a mobile phone on which a fraudulent phishing mail can be see
 Security Awareness. Business, Technology, Internet and network concept. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/security-awareness-business-technology-internet-and-network-concept-image566324464.html
Security Awareness. Business, Technology, Internet and network concept. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/security-awareness-business-technology-internet-and-network-concept-image566324464.htmlRF2RWA8HM–Security Awareness. Business, Technology, Internet and network concept.
 Brand awareness written on paper clipboard isolated on white background Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/brand-awareness-written-on-paper-clipboard-isolated-on-white-background-image560336404.html
Brand awareness written on paper clipboard isolated on white background Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/brand-awareness-written-on-paper-clipboard-isolated-on-white-background-image560336404.htmlRF2RFHEPC–Brand awareness written on paper clipboard isolated on white background
 Computer and security concept. On the laptop keyboard is a flash drive with the inscription - COMMUNICATE DATA POLICIES Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/computer-and-security-concept-on-the-laptop-keyboard-is-a-flash-drive-with-the-inscription-communicate-data-policies-image478895050.html
Computer and security concept. On the laptop keyboard is a flash drive with the inscription - COMMUNICATE DATA POLICIES Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/computer-and-security-concept-on-the-laptop-keyboard-is-a-flash-drive-with-the-inscription-communicate-data-policies-image478895050.htmlRF2JR3FEJ–Computer and security concept. On the laptop keyboard is a flash drive with the inscription - COMMUNICATE DATA POLICIES
 Data privacy day message written on wooden blocks with red background. Conceptual data privacy day symbol. Copy space. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/data-privacy-day-message-written-on-wooden-blocks-with-red-background-conceptual-data-privacy-day-symbol-copy-space-image632719511.html
Data privacy day message written on wooden blocks with red background. Conceptual data privacy day symbol. Copy space. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/data-privacy-day-message-written-on-wooden-blocks-with-red-background-conceptual-data-privacy-day-symbol-copy-space-image632719511.htmlRF2YNAT5B–Data privacy day message written on wooden blocks with red background. Conceptual data privacy day symbol. Copy space.
 Conceptual caption Data Theft. Business overview illegal transfer of any information that is confidential Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/conceptual-caption-data-theft-business-overview-illegal-transfer-of-any-information-that-is-confidential-image550256074.html
Conceptual caption Data Theft. Business overview illegal transfer of any information that is confidential Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/conceptual-caption-data-theft-business-overview-illegal-transfer-of-any-information-that-is-confidential-image550256074.htmlRF2PY696J–Conceptual caption Data Theft. Business overview illegal transfer of any information that is confidential
 Handwriting text Privacy Policy, Business approach Documentation regarding the management of the client s is data Inspirational business technology co Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/handwriting-text-privacy-policy-business-approach-documentation-regarding-the-management-of-the-client-s-is-data-inspirational-business-technology-co-image447028847.html
Handwriting text Privacy Policy, Business approach Documentation regarding the management of the client s is data Inspirational business technology co Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/handwriting-text-privacy-policy-business-approach-documentation-regarding-the-management-of-the-client-s-is-data-inspirational-business-technology-co-image447028847.htmlRF2GY7WRY–Handwriting text Privacy Policy, Business approach Documentation regarding the management of the client s is data Inspirational business technology co
 Keyboard Locked Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-image-keyboard-locked-163424629.html
Keyboard Locked Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-image-keyboard-locked-163424629.htmlRFKDTHNW–Keyboard Locked
 Online Privacy Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/online-privacy-image343699066.html
Online Privacy Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/online-privacy-image343699066.htmlRM2AY4RJJ–Online Privacy
 Banner for Data Privacy Day with male hacker Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/banner-for-data-privacy-day-with-male-hacker-image593909530.html
Banner for Data Privacy Day with male hacker Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/banner-for-data-privacy-day-with-male-hacker-image593909530.htmlRF2WE6WJJ–Banner for Data Privacy Day with male hacker
 Face recognition signs on people faces. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/face-recognition-signs-on-people-faces-image438453159.html
Face recognition signs on people faces. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/face-recognition-signs-on-people-faces-image438453159.htmlRF2GD97DB–Face recognition signs on people faces.
 A silver padlock rests on a laptop keyboard, illuminated by blue light. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/a-silver-padlock-rests-on-a-laptop-keyboard-illuminated-by-blue-light-image612884506.html
A silver padlock rests on a laptop keyboard, illuminated by blue light. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/a-silver-padlock-rests-on-a-laptop-keyboard-illuminated-by-blue-light-image612884506.htmlRF2XH38CA–A silver padlock rests on a laptop keyboard, illuminated by blue light.
 Shredded paper from a waste paper bin Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-shredded-paper-from-a-waste-paper-bin-28006173.html
Shredded paper from a waste paper bin Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-shredded-paper-from-a-waste-paper-bin-28006173.htmlRMBHFP4D–Shredded paper from a waste paper bin
 Faceless female paying with debit card while doing shopping on Internet on laptop Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/faceless-female-paying-with-debit-card-while-doing-shopping-on-internet-on-laptop-image439546747.html
Faceless female paying with debit card while doing shopping on Internet on laptop Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/faceless-female-paying-with-debit-card-while-doing-shopping-on-internet-on-laptop-image439546747.htmlRF2GF32A3–Faceless female paying with debit card while doing shopping on Internet on laptop
 January 28. Hand writing text European Privacy Day on calendar date. Save the date. Holiday. Day of the year concept. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/january-28-hand-writing-text-european-privacy-day-on-calendar-date-save-the-date-holiday-day-of-the-year-concept-image575957823.html
January 28. Hand writing text European Privacy Day on calendar date. Save the date. Holiday. Day of the year concept. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/january-28-hand-writing-text-european-privacy-day-on-calendar-date-save-the-date-holiday-day-of-the-year-concept-image575957823.htmlRF2TD1427–January 28. Hand writing text European Privacy Day on calendar date. Save the date. Holiday. Day of the year concept.
 Data privacy, data wellbeing, management, personal information, digital identity, digital behavior, security issue, data hygiene, cybersecurity Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/data-privacy-data-wellbeing-management-personal-information-digital-identity-digital-behavior-security-issue-data-hygiene-cybersecurity-image437439930.html
Data privacy, data wellbeing, management, personal information, digital identity, digital behavior, security issue, data hygiene, cybersecurity Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/data-privacy-data-wellbeing-management-personal-information-digital-identity-digital-behavior-security-issue-data-hygiene-cybersecurity-image437439930.htmlRF2GBK32J–Data privacy, data wellbeing, management, personal information, digital identity, digital behavior, security issue, data hygiene, cybersecurity
 Image of data processing and security padlock over woman using laptop Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/image-of-data-processing-and-security-padlock-over-woman-using-laptop-image608895515.html
Image of data processing and security padlock over woman using laptop Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/image-of-data-processing-and-security-padlock-over-woman-using-laptop-image608895515.htmlRF2XAHGCB–Image of data processing and security padlock over woman using laptop
RFKCC9RM–Young businesswoman working in virtual glasses, select the icon Security Awareness on the virtual display
 Data safety and handcuffs usb data stick Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/data-safety-and-handcuffs-usb-data-stick-image357172133.html
Data safety and handcuffs usb data stick Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/data-safety-and-handcuffs-usb-data-stick-image357172133.htmlRF2BN2GKH–Data safety and handcuffs usb data stick
 Digital Surveillance and Ethics of Online Privacy Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/digital-surveillance-and-ethics-of-online-privacy-image331621768.html
Digital Surveillance and Ethics of Online Privacy Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/digital-surveillance-and-ethics-of-online-privacy-image331621768.htmlRF2A7EJXG–Digital Surveillance and Ethics of Online Privacy
 Security Awareness. Business, Technology, Internet and network concept. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/security-awareness-business-technology-internet-and-network-concept-image557273843.html
Security Awareness. Business, Technology, Internet and network concept. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/security-awareness-business-technology-internet-and-network-concept-image557273843.htmlRF2RAJ0D7–Security Awareness. Business, Technology, Internet and network concept.
 Technology concept.Top view black bubble speech written BRAND AWARENESS with magnifying glass isolated on yellow background. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/technology-concepttop-view-black-bubble-speech-written-brand-awareness-with-magnifying-glass-isolated-on-yellow-background-image542252688.html
Technology concept.Top view black bubble speech written BRAND AWARENESS with magnifying glass isolated on yellow background. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/technology-concepttop-view-black-bubble-speech-written-brand-awareness-with-magnifying-glass-isolated-on-yellow-background-image542252688.htmlRF2PE5MRC–Technology concept.Top view black bubble speech written BRAND AWARENESS with magnifying glass isolated on yellow background.
 Phishing-Mail: Betrüger wollen sensible Daten und Kleinbeträge ergaunern. Hand hält ein Mobiltelefon auf dem eine betrügerische Phishing Paketmitteilung zu sehen ist. *** Phishing e-mail: Fraudsters want to steal sensitive data and small amounts. Hand holding a mobile phone on which a fraudulent phishing mail can be seen. 20240609- DSF0309 Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/phishing-mail-betrger-wollen-sensible-daten-und-kleinbetrge-ergaunern-hand-hlt-ein-mobiltelefon-auf-dem-eine-betrgerische-phishing-paketmitteilung-zu-sehen-ist-phishing-e-mail-fraudsters-want-to-steal-sensitive-data-and-small-amounts-hand-holding-a-mobile-phone-on-which-a-fraudulent-phishing-mail-can-be-seen-20240609-dsf0309-image609120245.html
Phishing-Mail: Betrüger wollen sensible Daten und Kleinbeträge ergaunern. Hand hält ein Mobiltelefon auf dem eine betrügerische Phishing Paketmitteilung zu sehen ist. *** Phishing e-mail: Fraudsters want to steal sensitive data and small amounts. Hand holding a mobile phone on which a fraudulent phishing mail can be seen. 20240609- DSF0309 Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/phishing-mail-betrger-wollen-sensible-daten-und-kleinbetrge-ergaunern-hand-hlt-ein-mobiltelefon-auf-dem-eine-betrgerische-phishing-paketmitteilung-zu-sehen-ist-phishing-e-mail-fraudsters-want-to-steal-sensitive-data-and-small-amounts-hand-holding-a-mobile-phone-on-which-a-fraudulent-phishing-mail-can-be-seen-20240609-dsf0309-image609120245.htmlRM2XAYR2D–Phishing-Mail: Betrüger wollen sensible Daten und Kleinbeträge ergaunern. Hand hält ein Mobiltelefon auf dem eine betrügerische Phishing Paketmitteilung zu sehen ist. *** Phishing e-mail: Fraudsters want to steal sensitive data and small amounts. Hand holding a mobile phone on which a fraudulent phishing mail can be seen. 20240609- DSF0309
 Data privacy day message written on wooden blocks with blue background. Conceptual data privacy day symbol. Copy space. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/data-privacy-day-message-written-on-wooden-blocks-with-blue-background-conceptual-data-privacy-day-symbol-copy-space-image635018893.html
Data privacy day message written on wooden blocks with blue background. Conceptual data privacy day symbol. Copy space. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/data-privacy-day-message-written-on-wooden-blocks-with-blue-background-conceptual-data-privacy-day-symbol-copy-space-image635018893.htmlRF2YW3H25–Data privacy day message written on wooden blocks with blue background. Conceptual data privacy day symbol. Copy space.
 Inspiration showing sign Data Theft. Business showcase illegal transfer of any information that is confidential Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/inspiration-showing-sign-data-theft-business-showcase-illegal-transfer-of-any-information-that-is-confidential-image550248240.html
Inspiration showing sign Data Theft. Business showcase illegal transfer of any information that is confidential Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/inspiration-showing-sign-data-theft-business-showcase-illegal-transfer-of-any-information-that-is-confidential-image550248240.htmlRF2PY5Y6T–Inspiration showing sign Data Theft. Business showcase illegal transfer of any information that is confidential
 Conceptual display Privacy Policy, Conceptual photo Documentation regarding the management of the client s is data Inspirational business technology c Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/conceptual-display-privacy-policy-conceptual-photo-documentation-regarding-the-management-of-the-client-s-is-data-inspirational-business-technology-c-image447028049.html
Conceptual display Privacy Policy, Conceptual photo Documentation regarding the management of the client s is data Inspirational business technology c Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/conceptual-display-privacy-policy-conceptual-photo-documentation-regarding-the-management-of-the-client-s-is-data-inspirational-business-technology-c-image447028049.htmlRF2GY7TRD–Conceptual display Privacy Policy, Conceptual photo Documentation regarding the management of the client s is data Inspirational business technology c
 Cyber Lock Graphic Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-image-cyber-lock-graphic-163424640.html
Cyber Lock Graphic Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-image-cyber-lock-graphic-163424640.htmlRFKDTHP8–Cyber Lock Graphic
 Online Privacy Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/online-privacy-image343688903.html
Online Privacy Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/online-privacy-image343688903.htmlRM2AY4AKK–Online Privacy
 Banner for Data Privacy Day with male hacker Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/banner-for-data-privacy-day-with-male-hacker-image593909547.html
Banner for Data Privacy Day with male hacker Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/banner-for-data-privacy-day-with-male-hacker-image593909547.htmlRF2WE6WK7–Banner for Data Privacy Day with male hacker
 Face recognition signs on people faces. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/face-recognition-signs-on-people-faces-image438453070.html
Face recognition signs on people faces. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/face-recognition-signs-on-people-faces-image438453070.htmlRF2GD97A6–Face recognition signs on people faces.
 A gold padlock lies on a black laptop keyboard, with the padlock's hasp resting on the enter key. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/a-gold-padlock-lies-on-a-black-laptop-keyboard-with-the-padlocks-hasp-resting-on-the-enter-key-image613076635.html
A gold padlock lies on a black laptop keyboard, with the padlock's hasp resting on the enter key. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/a-gold-padlock-lies-on-a-black-laptop-keyboard-with-the-padlocks-hasp-resting-on-the-enter-key-image613076635.htmlRF2XHC1E3–A gold padlock lies on a black laptop keyboard, with the padlock's hasp resting on the enter key.
 Data Privacy Week Vector illustration. Suitable for greeting card, poster and banner. Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/data-privacy-week-vector-illustration-suitable-for-greeting-card-poster-and-banner-image633927159.html
Data Privacy Week Vector illustration. Suitable for greeting card, poster and banner. Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/data-privacy-week-vector-illustration-suitable-for-greeting-card-poster-and-banner-image633927159.htmlRF2YR9TFK–Data Privacy Week Vector illustration. Suitable for greeting card, poster and banner.
 Save the idea from the encroachments of industrial spies. Violation of privacy. Personal and sensitive information. Use of encryption, biometric authe Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/save-the-idea-from-the-encroachments-of-industrial-spies-violation-of-privacy-personal-and-sensitive-information-use-of-encryption-biometric-authe-image559859705.html
Save the idea from the encroachments of industrial spies. Violation of privacy. Personal and sensitive information. Use of encryption, biometric authe Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/save-the-idea-from-the-encroachments-of-industrial-spies-violation-of-privacy-personal-and-sensitive-information-use-of-encryption-biometric-authe-image559859705.htmlRF2RERPND–Save the idea from the encroachments of industrial spies. Violation of privacy. Personal and sensitive information. Use of encryption, biometric authe
 Businessman uses laptop with cybersecurity technology to protect personal data. Cybersecurity and privacy concepts Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/businessman-uses-laptop-with-cybersecurity-technology-to-protect-personal-data-cybersecurity-and-privacy-concepts-image615013043.html
Businessman uses laptop with cybersecurity technology to protect personal data. Cybersecurity and privacy concepts Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/businessman-uses-laptop-with-cybersecurity-technology-to-protect-personal-data-cybersecurity-and-privacy-concepts-image615013043.htmlRF2XMG7BF–Businessman uses laptop with cybersecurity technology to protect personal data. Cybersecurity and privacy concepts
 Data privacy, data wellbeing, management, personal information, digital identity, digital behavior, security issue, data hygiene, cybersecurity Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/data-privacy-data-wellbeing-management-personal-information-digital-identity-digital-behavior-security-issue-data-hygiene-cybersecurity-image437429359.html
Data privacy, data wellbeing, management, personal information, digital identity, digital behavior, security issue, data hygiene, cybersecurity Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/data-privacy-data-wellbeing-management-personal-information-digital-identity-digital-behavior-security-issue-data-hygiene-cybersecurity-image437429359.htmlRF2GBJHH3–Data privacy, data wellbeing, management, personal information, digital identity, digital behavior, security issue, data hygiene, cybersecurity
 Image of data processing and security padlock over woman using laptop Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/image-of-data-processing-and-security-padlock-over-woman-using-laptop-image608895441.html
Image of data processing and security padlock over woman using laptop Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/image-of-data-processing-and-security-padlock-over-woman-using-laptop-image608895441.htmlRF2XAHG9N–Image of data processing and security padlock over woman using laptop
 Concept of business security, safety of information from virus, crime and attack. Internet secure system. Protection system. Security awareness Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-concept-of-business-security-safety-of-information-from-virus-crime-138960935.html
Concept of business security, safety of information from virus, crime and attack. Internet secure system. Protection system. Security awareness Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-concept-of-business-security-safety-of-information-from-virus-crime-138960935.htmlRMJ2262F–Concept of business security, safety of information from virus, crime and attack. Internet secure system. Protection system. Security awareness
 Internet crime data stick with handcuffs symbol picture Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/internet-crime-data-stick-with-handcuffs-symbol-picture-image357171642.html
Internet crime data stick with handcuffs symbol picture Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/internet-crime-data-stick-with-handcuffs-symbol-picture-image357171642.htmlRF2BN2G22–Internet crime data stick with handcuffs symbol picture
 Digital Surveillance and Ethics of Online Privacy Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-image-digital-surveillance-and-ethics-of-online-privacy-167097389.html
Digital Surveillance and Ethics of Online Privacy Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-image-digital-surveillance-and-ethics-of-online-privacy-167097389.htmlRFKKRXBW–Digital Surveillance and Ethics of Online Privacy
 Inscription Security Awareness. Website Header Banner Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/inscription-security-awareness-website-header-banner-image434276574.html
Inscription Security Awareness. Website Header Banner Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/inscription-security-awareness-website-header-banner-image434276574.htmlRF2G6F05J–Inscription Security Awareness. Website Header Banner
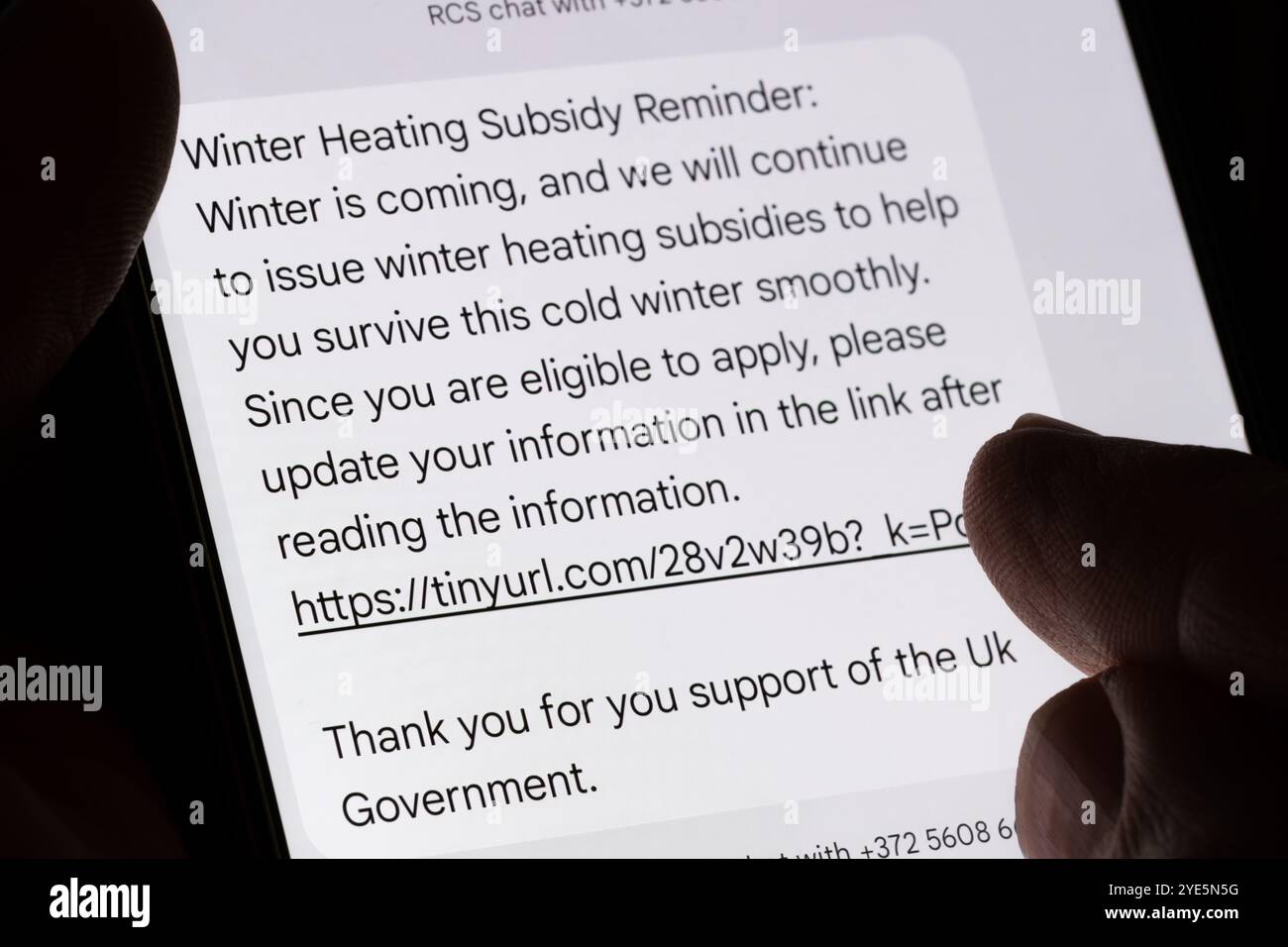 Close-up of genuine phishing text message falsely offering winter heating subsidy from UK government, highlighting fraud attempt through malicious lin Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/close-up-of-genuine-phishing-text-message-falsely-offering-winter-heating-subsidy-from-uk-government-highlighting-fraud-attempt-through-malicious-lin-image628304812.html
Close-up of genuine phishing text message falsely offering winter heating subsidy from UK government, highlighting fraud attempt through malicious lin Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/close-up-of-genuine-phishing-text-message-falsely-offering-winter-heating-subsidy-from-uk-government-highlighting-fraud-attempt-through-malicious-lin-image628304812.htmlRF2YE5N5G–Close-up of genuine phishing text message falsely offering winter heating subsidy from UK government, highlighting fraud attempt through malicious lin
 Phishing-Mail: Betrüger wollen sensible Daten und Kleinbeträge ergaunern. Hand hält ein Mobiltelefon auf dem eine betrügerische Phishing Paketmitteilung zu sehen ist. *** Phishing e-mail: Fraudsters want to steal sensitive data and small amounts. Hand holding a mobile phone on which a fraudulent phishing mail can be seen. 20240609- DSF0310 Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/phishing-mail-betrger-wollen-sensible-daten-und-kleinbetrge-ergaunern-hand-hlt-ein-mobiltelefon-auf-dem-eine-betrgerische-phishing-paketmitteilung-zu-sehen-ist-phishing-e-mail-fraudsters-want-to-steal-sensitive-data-and-small-amounts-hand-holding-a-mobile-phone-on-which-a-fraudulent-phishing-mail-can-be-seen-20240609-dsf0310-image609120277.html
Phishing-Mail: Betrüger wollen sensible Daten und Kleinbeträge ergaunern. Hand hält ein Mobiltelefon auf dem eine betrügerische Phishing Paketmitteilung zu sehen ist. *** Phishing e-mail: Fraudsters want to steal sensitive data and small amounts. Hand holding a mobile phone on which a fraudulent phishing mail can be seen. 20240609- DSF0310 Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/phishing-mail-betrger-wollen-sensible-daten-und-kleinbetrge-ergaunern-hand-hlt-ein-mobiltelefon-auf-dem-eine-betrgerische-phishing-paketmitteilung-zu-sehen-ist-phishing-e-mail-fraudsters-want-to-steal-sensitive-data-and-small-amounts-hand-holding-a-mobile-phone-on-which-a-fraudulent-phishing-mail-can-be-seen-20240609-dsf0310-image609120277.htmlRM2XAYR3H–Phishing-Mail: Betrüger wollen sensible Daten und Kleinbeträge ergaunern. Hand hält ein Mobiltelefon auf dem eine betrügerische Phishing Paketmitteilung zu sehen ist. *** Phishing e-mail: Fraudsters want to steal sensitive data and small amounts. Hand holding a mobile phone on which a fraudulent phishing mail can be seen. 20240609- DSF0310
 Data privacy day message written on wooden blocks with purple background. Conceptual data privacy day symbol. Copy space. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/data-privacy-day-message-written-on-wooden-blocks-with-purple-background-conceptual-data-privacy-day-symbol-copy-space-image632729773.html
Data privacy day message written on wooden blocks with purple background. Conceptual data privacy day symbol. Copy space. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/data-privacy-day-message-written-on-wooden-blocks-with-purple-background-conceptual-data-privacy-day-symbol-copy-space-image632729773.htmlRF2YNB97W–Data privacy day message written on wooden blocks with purple background. Conceptual data privacy day symbol. Copy space.
 Hand writing sign Data Theft. Business idea illegal transfer of any information that is confidential Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/hand-writing-sign-data-theft-business-idea-illegal-transfer-of-any-information-that-is-confidential-image550260495.html
Hand writing sign Data Theft. Business idea illegal transfer of any information that is confidential Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/hand-writing-sign-data-theft-business-idea-illegal-transfer-of-any-information-that-is-confidential-image550260495.htmlRF2PY6ETF–Hand writing sign Data Theft. Business idea illegal transfer of any information that is confidential
 Handwriting text Privacy Policy, Business concept Documentation regarding the management of the client s is data Computer Laptop For Communication Typ Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/handwriting-text-privacy-policy-business-concept-documentation-regarding-the-management-of-the-client-s-is-data-computer-laptop-for-communication-typ-image447021691.html
Handwriting text Privacy Policy, Business concept Documentation regarding the management of the client s is data Computer Laptop For Communication Typ Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/handwriting-text-privacy-policy-business-concept-documentation-regarding-the-management-of-the-client-s-is-data-computer-laptop-for-communication-typ-image447021691.htmlRF2GY7GMB–Handwriting text Privacy Policy, Business concept Documentation regarding the management of the client s is data Computer Laptop For Communication Typ
RFKDTHP7–Locked Computer Icon

