Botnet detection Stock Vectors & Vector Art
RF2PP6PA3–Malware prevention linear icons set. Firewall, Antivirus, Encryption, Patching, Detection, Sandbox, Phishing line vector and concept signs. Ransomware
 AI Cybersecurity set. Digital defense mechanisms powered by artificial intelligence. User behavior analysis to fishing detection. Vector illustration. Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/ai-cybersecurity-set-digital-defense-mechanisms-powered-by-artificial-intelligence-user-behavior-analysis-to-fishing-detection-vector-illustration-image626341613.html
AI Cybersecurity set. Digital defense mechanisms powered by artificial intelligence. User behavior analysis to fishing detection. Vector illustration. Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/ai-cybersecurity-set-digital-defense-mechanisms-powered-by-artificial-intelligence-user-behavior-analysis-to-fishing-detection-vector-illustration-image626341613.htmlRF2YB0939–AI Cybersecurity set. Digital defense mechanisms powered by artificial intelligence. User behavior analysis to fishing detection. Vector illustration.
 Vulnerability, Spreading Malware or Ransomware Attack - Failing Vulnerable Network Threat Protection -IT Security, Corporate Networking Concept Vector Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-vulnerability-spreading-malware-or-ransomware-attack-failing-vulnerable-142975524.html
Vulnerability, Spreading Malware or Ransomware Attack - Failing Vulnerable Network Threat Protection -IT Security, Corporate Networking Concept Vector Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-vulnerability-spreading-malware-or-ransomware-attack-failing-vulnerable-142975524.htmlRFJ8H2MM–Vulnerability, Spreading Malware or Ransomware Attack - Failing Vulnerable Network Threat Protection -IT Security, Corporate Networking Concept Vector
RF2PNKCHM–Threat management line icons collection. Risk, Security, Vulnerability, Attack, Response, Assessment, Detection vector and linear illustration
RF2XH8TDX–Black and white icon of a bomb with binary code, representing a cyber attack
RF2DX2HNW–Secured control book icon. Outline secured control book vector icon for web design isolated on white background
RF2PP39KX–Malware prevention linear icons set. Firewall, Antivirus, Encryption, Patching, Detection, Sandbox, Phishing line vector and concept signs. Ransomware
 Botnet concept. An alert tech-savvy individual encounters a menacing skull on devices, symbolizing the lurking dangers of botnets. Unauthorized access. Network compromise. Flat vector illustration. Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/botnet-concept-an-alert-tech-savvy-individual-encounters-a-menacing-skull-on-devices-symbolizing-the-lurking-dangers-of-botnets-unauthorized-access-network-compromise-flat-vector-illustration-image597446798.html
Botnet concept. An alert tech-savvy individual encounters a menacing skull on devices, symbolizing the lurking dangers of botnets. Unauthorized access. Network compromise. Flat vector illustration. Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/botnet-concept-an-alert-tech-savvy-individual-encounters-a-menacing-skull-on-devices-symbolizing-the-lurking-dangers-of-botnets-unauthorized-access-network-compromise-flat-vector-illustration-image597446798.htmlRF2WM01DJ–Botnet concept. An alert tech-savvy individual encounters a menacing skull on devices, symbolizing the lurking dangers of botnets. Unauthorized access. Network compromise. Flat vector illustration.
 Successfully Detected and Stopped Malware or Ransomware Attack - Network Threat Protection, IT Security Concept Design, Vector illustration Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-successfully-detected-and-stopped-malware-or-ransomware-attack-network-142975430.html
Successfully Detected and Stopped Malware or Ransomware Attack - Network Threat Protection, IT Security Concept Design, Vector illustration Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-successfully-detected-and-stopped-malware-or-ransomware-attack-network-142975430.htmlRFJ8H2HA–Successfully Detected and Stopped Malware or Ransomware Attack - Network Threat Protection, IT Security Concept Design, Vector illustration
RF2PNE67E–Internet security line icons collection. Firewall, Encryption, Malware, Phishing, SSL, Authentication, Antivirus vector and linear illustration
RF2XH8W3T–Black silhouette icon representing a computer virus entering an operating system through an internet cable
RF2DMTNBD–Secured control book icon. Outline secured control book vector icon for web design isolated on white background
RF2PP15GP–Malware prevention linear icons set. Firewall, Antivirus, Encryption, Patching, Detection, Sandbox, Phishing line vector and concept signs. Ransomware
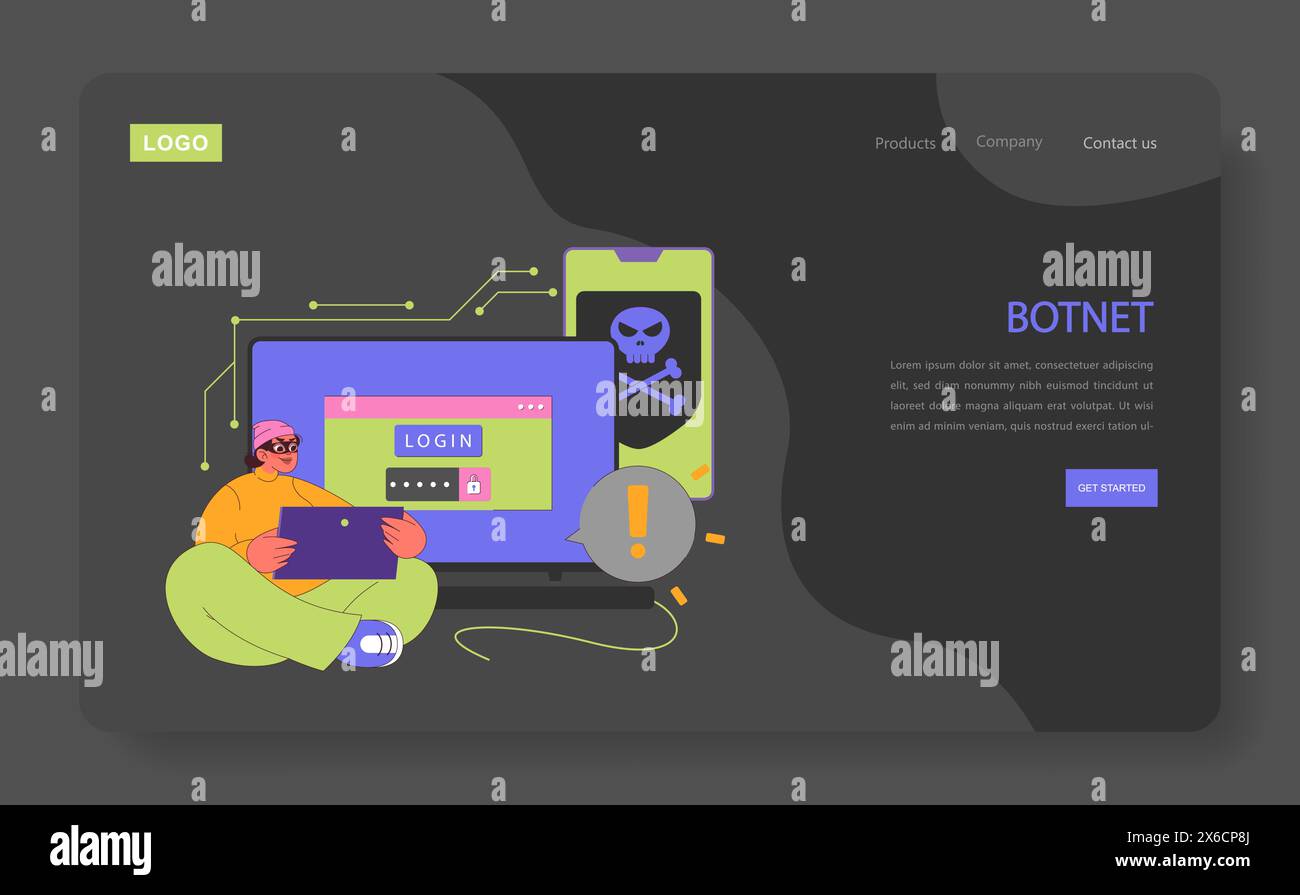 Botnet concept. An alert tech-savvy individual encounters a menacing skull on devices, symbolizing the lurking dangers of botnets. Unauthorized access. Network compromise. Flat vector illustration. Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/botnet-concept-an-alert-tech-savvy-individual-encounters-a-menacing-skull-on-devices-symbolizing-the-lurking-dangers-of-botnets-unauthorized-access-network-compromise-flat-vector-illustration-image606331730.html
Botnet concept. An alert tech-savvy individual encounters a menacing skull on devices, symbolizing the lurking dangers of botnets. Unauthorized access. Network compromise. Flat vector illustration. Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/botnet-concept-an-alert-tech-savvy-individual-encounters-a-menacing-skull-on-devices-symbolizing-the-lurking-dangers-of-botnets-unauthorized-access-network-compromise-flat-vector-illustration-image606331730.htmlRF2X6CP8J–Botnet concept. An alert tech-savvy individual encounters a menacing skull on devices, symbolizing the lurking dangers of botnets. Unauthorized access. Network compromise. Flat vector illustration.
 Successfully Detected and Stopped Malware or Ransomware Attack - Network Threat Protection, IT Security Concept Design, Vector illustration Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-successfully-detected-and-stopped-malware-or-ransomware-attack-network-142975523.html
Successfully Detected and Stopped Malware or Ransomware Attack - Network Threat Protection, IT Security Concept Design, Vector illustration Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-successfully-detected-and-stopped-malware-or-ransomware-attack-network-142975523.htmlRFJ8H2MK–Successfully Detected and Stopped Malware or Ransomware Attack - Network Threat Protection, IT Security Concept Design, Vector illustration
RF2PNX6FM–Virtual security line icons collection. Encryption, Firewall, Passwords, Cyberattack, Malware, Authentication, Cybercrime vector and linear
RF2HCMT93–Secured control book icon. Outline secured control book vector icon color flat isolated
RF2PP6ENX–Cybersecurity linear icons set. Malware, Encryption, Firewall, Phishing, Cybercrime, Botnet, Hacking line vector and concept signs. Vulnerability
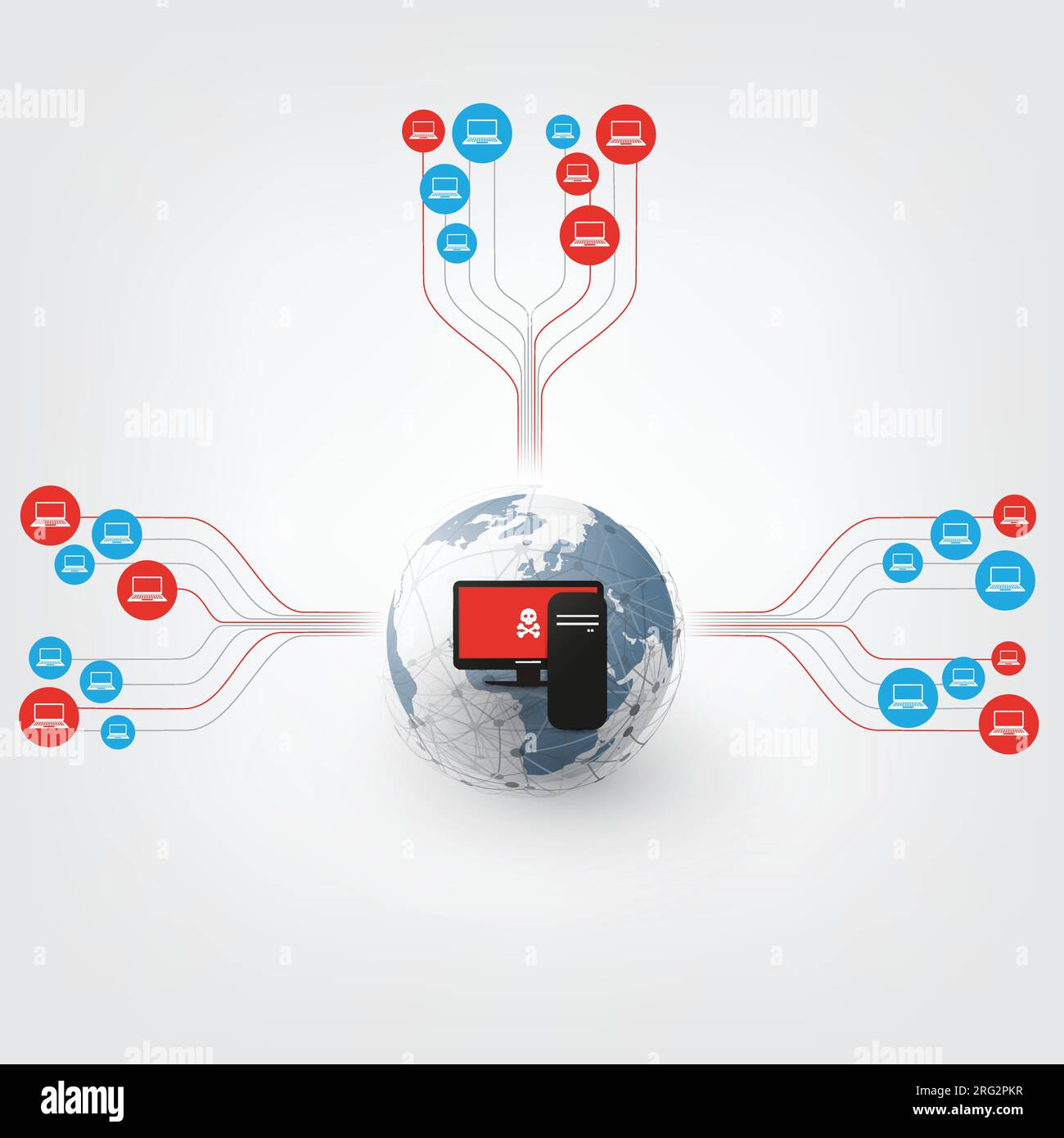 Computer Vulnerability, Spreading Malware or Ransomware Attack - Failing Vulnerable Network without Threat Protection - IT Security, Corporate Network Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/computer-vulnerability-spreading-malware-or-ransomware-attack-failing-vulnerable-network-without-threat-protection-it-security-corporate-network-image560627979.html
Computer Vulnerability, Spreading Malware or Ransomware Attack - Failing Vulnerable Network without Threat Protection - IT Security, Corporate Network Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/computer-vulnerability-spreading-malware-or-ransomware-attack-failing-vulnerable-network-without-threat-protection-it-security-corporate-network-image560627979.htmlRF2RG2PKR–Computer Vulnerability, Spreading Malware or Ransomware Attack - Failing Vulnerable Network without Threat Protection - IT Security, Corporate Network
RF2PNH1J8–Cyber security line icons collection. Malware, Firewall, Encryption, Vulnerability, Phishing, Passwords, Privacy vector and linear illustration
RF2PP6326–Cybersecurity linear icons set. Malware, Encryption, Firewall, Phishing, Cybercrime, Botnet, Hacking line vector and concept signs. Vulnerability
RF2PNE2T2–Digital protection line icons collection. Encryption, Passwords, Firewall, VPN, Antivirus, Malware, Cybersecurity vector and linear illustration
RF2PP2AF1–Malware detection linear icons set. Virus, Trojan, Spyware, Malware, Ransomware, Adware, Botnet line vector and concept signs. Worm,Rootkit,Keylogger
RF2PNGB14–Web security line icons collection. Encryption, Firewall, Malware, Phishing, Passwords, Authentication, SSL vector and linear illustration
RF2PP1KWP–Malware detection linear icons set. Virus, Trojan, Spyware, Malware, Ransomware, Adware, Botnet line vector and concept signs. Worm,Rootkit,Keylogger
RF2PNTG5A–Internet security line icons collection. Firewall, Malware, Encryption, Phishing, Spam, Antivirus, Cybercrime vector and linear illustration
RF2PP8EEX–Network protection linear icons set. Firewall, Encryption, Antivirus, Malware, Cybersecurity, Spam, Intrusion line vector and concept signs. Phishing
RF2PNHWTP–Cyber security line icons collection. Firewall, Malware, Encryption, Phishing, Virus, Hacking, Cybercrime vector and linear illustration. Passwords
RF2PP7MMR–Network protection linear icons set. Firewall, Encryption, Antivirus, Malware, Cybersecurity, Spam, Intrusion line vector and concept signs. Phishing
RF2PNKW3A–Enterprise architecture line icons collection. Firewall, Encryption, Malware, Antivirus, Authentication, Patching, Intrusion vector and linear
RF2PNW0HW–Network protection linear icons set. Firewall, Encryption, Antivirus, Malware, Cybersecurity, Spam, Intrusion vector symbols and line concept signs
RF2PNG1CK–Computer security line icons collection. Firewall, Malware, Encryption, Hacking, Passwords, Cybercrime, Antivirus vector and linear illustration
RF2PP2X9R–Cyber connections linear icons set. Cybersecurity, Nerking, Firewall, Router, Encryption, Phishing, Hacking line vector and concept signs. Malware
RF2PNJMJD–Cyber defense line icons collection. Firewall, Encryption, Malware, Antivirus, Authentication, Patching, Intrusion vector and linear illustration
RF2PP4XAK–Cyber connections linear icons set. Cybersecurity, Nerking, Firewall, Router, Encryption, Phishing, Hacking line vector and concept signs. Malware
RF2PNNCY8–Cyber resources line icons collection. Encryption, Firewall, Malware, Vulnerability, Breach, Hack, Phishing vector and linear illustration. Ransomware
RF2PNXJG6–Cybersecurity measures linear icons set. Encryption, Firewall, Antivirus, Authentication, Authorization, Biometrics, Malware line vector and concept
RF2PNWEYF–Web security line icons collection. Firewall, Encryption, Malware, Phishing, Hacking, SSL, Vulnerability vector and linear illustration
RF2PP62FW–Cybersecurity measures linear icons set. Encryption, Firewall, Antivirus, Authentication, Authorization, Biometrics, Malware line vector and concept
RF2PP3XC0–Study abroad and exchange programs line icons collection. Encryption, Firewall, Antivirus, Phishing, Malware, Hacking, Cybercrime vector and linear
RF2PWF624–Cyber defense linear icons set. Encryption, Firewall, Malware, Hacking, Antivirus, Intrusion, Cybercrime line vector and concept signs. Vulnerability
RF2PP8P87–Cybersecurity protection line icons collection. Encryption, Firewall, Antivirus, Phishing, Malware, Hacking, Cybercrime vector and linear illustration
RF2PNXB5H–Cyber defense linear icons set. Encryption, Firewall, Malware, Hacking, Antivirus, Intrusion, Cybercrime line vector and concept signs. Vulnerability
RF2PP49TT–Cyber defense linear icons set. Encryption, Firewall, Malware, Hacking, Antivirus, Intrusion, Cybercrime line vector and concept signs. Vulnerability
RF2PNX62Y–Artificial security linear icons set. Cybersecurity, Encryption, Authentication, Malware, Passwords, Nerk, Hackers line vector and concept signs
RF2PNXJKX–Artificial security linear icons set. Cybersecurity, Encryption, Authentication, Malware, Passwords, Nerk, Hackers line vector and concept signs
RF2PNTXWD–Cyber space linear icons set. Digital, Virtual, Online, Internet, Technology, Connectivity, Cybersecurity vector symbols and line concept signs
RF2PP71H8–Cyber space linear icons set. Digital, Virtual, Online, Internet, Technology, Connectivity, Cybersecurity line vector and concept signs. Surveillance
RF2PP704F–Cyber space linear icons set. Digital, Virtual, Online, Internet, Technology, Connectivity, Cybersecurity line vector and concept signs. Surveillance
RF2PP0PFR–Online security linear icons set. Encryption, Firewall, Passwords, Privacy, Malware, Cybersecurity, Antivirus line vector and concept signs
RF2PNYR7F–Online security linear icons set. Encryption, Firewall, Passwords, Privacy, Malware, Cybersecurity, Antivirus line vector and concept signs
RF2PNXNNG–Online security linear icons set. Encryption, Firewall, Passwords, Privacy, Malware, Cybersecurity, Antivirus line vector and concept signs
RF2PP3HN3–Digital defense linear icons set. Cybersecurity, Encryption, Firewall, Malware, Passwords, Phishing, Vulnerabilities line vector and concept signs
RF2PP5JDD–Digital defense linear icons set. Cybersecurity, Encryption, Firewall, Malware, Passwords, Phishing, Vulnerabilities line vector and concept signs