Quick filters:
Cyber crime control Stock Photos and Images
 Security concept with person increasing the protection level by turning a knob. Selecting highest defence against cyber attack. Digital crime and data Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/security-concept-with-person-increasing-the-protection-level-by-turning-a-knob-selecting-highest-defence-against-cyber-attack-digital-crime-and-data-image448002768.html
Security concept with person increasing the protection level by turning a knob. Selecting highest defence against cyber attack. Digital crime and data Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/security-concept-with-person-increasing-the-protection-level-by-turning-a-knob-selecting-highest-defence-against-cyber-attack-digital-crime-and-data-image448002768.htmlRF2H0T82T–Security concept with person increasing the protection level by turning a knob. Selecting highest defence against cyber attack. Digital crime and data
 Handcuffs on a laptop. Cyber crime or hacking. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/handcuffs-on-a-laptop-cyber-crime-or-hacking-image216622186.html
Handcuffs on a laptop. Cyber crime or hacking. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/handcuffs-on-a-laptop-cyber-crime-or-hacking-image216622186.htmlRFPGBYPJ–Handcuffs on a laptop. Cyber crime or hacking.
 Previously unreleased photo dated 08/09/11 of a view of the Global Operations Security Control Centre, which is responsible for protecting the military's networks worldwide from cyber attacks. PRESS ASSSOCIATION Photo. Issue date: Friday November 25, 2011. A new police Cyber Crime Unit is to be set up to protect Britain against the growing threat of attacks on the internet and in electronic communications. See PA story POLITICS Cyber. Photo credit should read: Tim Ireland/PA Wire Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-previously-unreleased-photo-dated-080911-of-a-view-of-the-global-operations-106216001.html
Previously unreleased photo dated 08/09/11 of a view of the Global Operations Security Control Centre, which is responsible for protecting the military's networks worldwide from cyber attacks. PRESS ASSSOCIATION Photo. Issue date: Friday November 25, 2011. A new police Cyber Crime Unit is to be set up to protect Britain against the growing threat of attacks on the internet and in electronic communications. See PA story POLITICS Cyber. Photo credit should read: Tim Ireland/PA Wire Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-previously-unreleased-photo-dated-080911-of-a-view-of-the-global-operations-106216001.htmlRMG4PFGH–Previously unreleased photo dated 08/09/11 of a view of the Global Operations Security Control Centre, which is responsible for protecting the military's networks worldwide from cyber attacks. PRESS ASSSOCIATION Photo. Issue date: Friday November 25, 2011. A new police Cyber Crime Unit is to be set up to protect Britain against the growing threat of attacks on the internet and in electronic communications. See PA story POLITICS Cyber. Photo credit should read: Tim Ireland/PA Wire
 Internet crime concept. Handcuffs on the laptop keyboard, cyber crime concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/internet-crime-concept-handcuffs-on-the-laptop-keyboard-cyber-crime-concept-image396139794.html
Internet crime concept. Handcuffs on the laptop keyboard, cyber crime concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/internet-crime-concept-handcuffs-on-the-laptop-keyboard-cyber-crime-concept-image396139794.htmlRF2E0DM9P–Internet crime concept. Handcuffs on the laptop keyboard, cyber crime concept
RFF0JN03–Blue sports car with a smart phone. There is hacker icon showing in the phone. Concept for cyber crime.
 National Cyber Security Awareness Month October. Vector illustration. It is celebrated every year in October. Suitable for greeting card, poster Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/national-cyber-security-awareness-month-october-vector-illustration-it-is-celebrated-every-year-in-october-suitable-for-greeting-card-poster-image566746773.html
National Cyber Security Awareness Month October. Vector illustration. It is celebrated every year in October. Suitable for greeting card, poster Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/national-cyber-security-awareness-month-october-vector-illustration-it-is-celebrated-every-year-in-october-suitable-for-greeting-card-poster-image566746773.htmlRF2RX1F85–National Cyber Security Awareness Month October. Vector illustration. It is celebrated every year in October. Suitable for greeting card, poster
 handcuffs on laptop cyber crime concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/handcuffs-on-laptop-cyber-crime-concept-image369872827.html
handcuffs on laptop cyber crime concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/handcuffs-on-laptop-cyber-crime-concept-image369872827.htmlRM2CDN4FR–handcuffs on laptop cyber crime concept
 Indian Man Using Stop Gesture – Warning Against AI Threats and Cyber Crime. An Indian man is depicted with his palm wide open in a strong stop gesture Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/indian-man-using-stop-gesture-warning-against-ai-threats-and-cyber-crime-an-indian-man-is-depicted-with-his-palm-wide-open-in-a-strong-stop-gesture-image491432113.html
Indian Man Using Stop Gesture – Warning Against AI Threats and Cyber Crime. An Indian man is depicted with his palm wide open in a strong stop gesture Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/indian-man-using-stop-gesture-warning-against-ai-threats-and-cyber-crime-an-indian-man-is-depicted-with-his-palm-wide-open-in-a-strong-stop-gesture-image491432113.htmlRF2KFEJJW–Indian Man Using Stop Gesture – Warning Against AI Threats and Cyber Crime. An Indian man is depicted with his palm wide open in a strong stop gesture
 High tech IT cyber crime arrest concept, image of police handcuffs over computer keyboard, selective focus Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/high-tech-it-cyber-crime-arrest-concept-image-of-police-handcuffs-over-computer-keyboard-selective-focus-image594530676.html
High tech IT cyber crime arrest concept, image of police handcuffs over computer keyboard, selective focus Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/high-tech-it-cyber-crime-arrest-concept-image-of-police-handcuffs-over-computer-keyboard-selective-focus-image594530676.htmlRF2WF75XC–High tech IT cyber crime arrest concept, image of police handcuffs over computer keyboard, selective focus
 Anonymous Cyberbully Pressing CYBERBULLYING Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-image-anonymous-cyberbully-pressing-cyberbullying-168818839.html
Anonymous Cyberbully Pressing CYBERBULLYING Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-image-anonymous-cyberbully-pressing-cyberbullying-168818839.htmlRFKPJA47–Anonymous Cyberbully Pressing CYBERBULLYING
 Black Hat Hacker Pressing MALICIOUS SOFTWARE Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-image-black-hat-hacker-pressing-malicious-software-168769054.html
Black Hat Hacker Pressing MALICIOUS SOFTWARE Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-image-black-hat-hacker-pressing-malicious-software-168769054.htmlRFKPG2J6–Black Hat Hacker Pressing MALICIOUS SOFTWARE
 A hacker behind binary code, stream of data, unlock cyber security, and control your personal identity Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/a-hacker-behind-binary-code-stream-of-data-unlock-cyber-security-and-control-your-personal-identity-image565818830.html
A hacker behind binary code, stream of data, unlock cyber security, and control your personal identity Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/a-hacker-behind-binary-code-stream-of-data-unlock-cyber-security-and-control-your-personal-identity-image565818830.htmlRF2RTF7KA–A hacker behind binary code, stream of data, unlock cyber security, and control your personal identity
 Cyber crime concept. Metal handcuffs on computer keyboard, 3d illustration Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-crime-concept-metal-handcuffs-on-computer-keyboard-3d-illustration-image209934346.html
Cyber crime concept. Metal handcuffs on computer keyboard, 3d illustration Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-crime-concept-metal-handcuffs-on-computer-keyboard-3d-illustration-image209934346.htmlRFP5F9B6–Cyber crime concept. Metal handcuffs on computer keyboard, 3d illustration
 Cyber security abstract technology banner background. Data protection, information privacy. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-security-abstract-technology-banner-background-data-protection-information-privacy-image246398493.html
Cyber security abstract technology banner background. Data protection, information privacy. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-security-abstract-technology-banner-background-data-protection-information-privacy-image246398493.htmlRFT8TBP5–Cyber security abstract technology banner background. Data protection, information privacy.
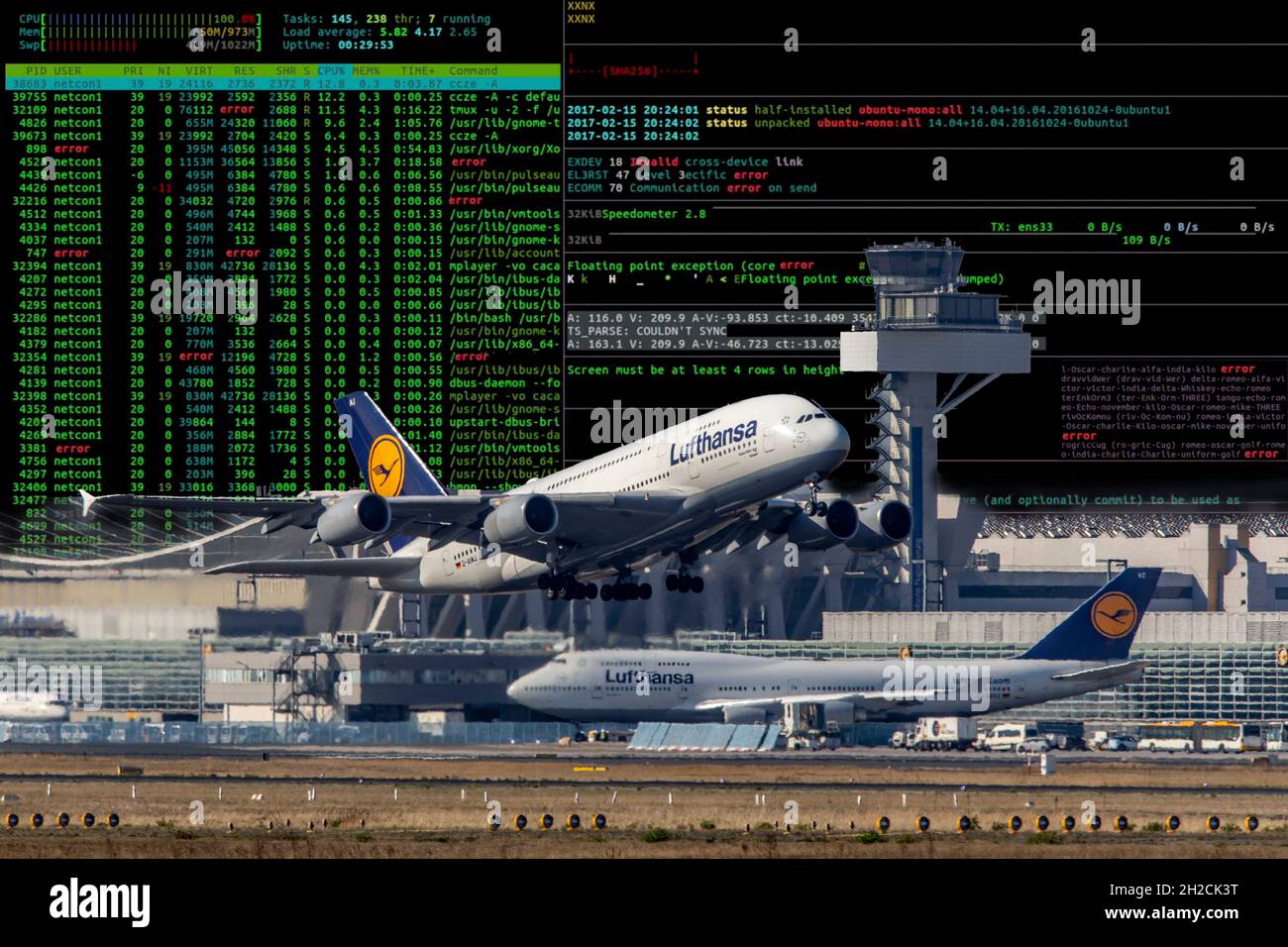 Symbolic image Cybe attack, computer crime, cybercrime, computer hackers attack a city's IT infrastructure, traffic, Frankfurt Airport, Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/symbolic-image-cybe-attack-computer-crime-cybercrime-computer-hackers-attack-a-citys-it-infrastructure-traffic-frankfurt-airport-image448977308.html
Symbolic image Cybe attack, computer crime, cybercrime, computer hackers attack a city's IT infrastructure, traffic, Frankfurt Airport, Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/symbolic-image-cybe-attack-computer-crime-cybercrime-computer-hackers-attack-a-citys-it-infrastructure-traffic-frankfurt-airport-image448977308.htmlRM2H2CK3T–Symbolic image Cybe attack, computer crime, cybercrime, computer hackers attack a city's IT infrastructure, traffic, Frankfurt Airport,
 Big Brother Is Watching. Concept Of Global human Surveillance, Security Systems And The freedom Of A New World With Text Please Smile Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/big-brother-is-watching-concept-of-global-human-surveillance-security-systems-and-the-freedom-of-a-new-world-with-text-please-smile-image356490850.html
Big Brother Is Watching. Concept Of Global human Surveillance, Security Systems And The freedom Of A New World With Text Please Smile Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/big-brother-is-watching-concept-of-global-human-surveillance-security-systems-and-the-freedom-of-a-new-world-with-text-please-smile-image356490850.htmlRF2BKYFM2–Big Brother Is Watching. Concept Of Global human Surveillance, Security Systems And The freedom Of A New World With Text Please Smile
 Business, Technology, Internet and network concept. Young business man, working on the tablet of the future, select on the virtual display: Cyber Secu Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-business-technology-internet-and-network-concept-young-business-man-138964587.html
Business, Technology, Internet and network concept. Young business man, working on the tablet of the future, select on the virtual display: Cyber Secu Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-business-technology-internet-and-network-concept-young-business-man-138964587.htmlRFJ22AMY–Business, Technology, Internet and network concept. Young business man, working on the tablet of the future, select on the virtual display: Cyber Secu
 Cyber Security Isometric Concept. Vector Illustration. Gateway Preventing Cyber Attacks. Protecting Data and Confidentiality. Security Services. Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-security-isometric-concept-vector-illustration-gateway-preventing-cyber-attacks-protecting-data-and-confidentiality-security-services-image406682058.html
Cyber Security Isometric Concept. Vector Illustration. Gateway Preventing Cyber Attacks. Protecting Data and Confidentiality. Security Services. Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-security-isometric-concept-vector-illustration-gateway-preventing-cyber-attacks-protecting-data-and-confidentiality-security-services-image406682058.htmlRF2EHHY36–Cyber Security Isometric Concept. Vector Illustration. Gateway Preventing Cyber Attacks. Protecting Data and Confidentiality. Security Services.
 Computer Security concept. Chain and padlock on keyboard. Cyber security concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/computer-security-concept-chain-and-padlock-on-keyboard-cyber-security-concept-image612418767.html
Computer Security concept. Chain and padlock on keyboard. Cyber security concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/computer-security-concept-chain-and-padlock-on-keyboard-cyber-security-concept-image612418767.htmlRF2XGA2AR–Computer Security concept. Chain and padlock on keyboard. Cyber security concept
 Cyber security expert working on network and data protection on laptop computer against digital crime. Privacy technology on internet. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-security-expert-working-on-network-and-data-protection-on-laptop-computer-against-digital-crime-privacy-technology-on-internet-image447818488.html
Cyber security expert working on network and data protection on laptop computer against digital crime. Privacy technology on internet. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-security-expert-working-on-network-and-data-protection-on-laptop-computer-against-digital-crime-privacy-technology-on-internet-image447818488.htmlRF2H0FW1C–Cyber security expert working on network and data protection on laptop computer against digital crime. Privacy technology on internet.
RF2T3MYCP–Cyber security banner web icon vector illustration concept with icon of application, information, network, operational, encryption, access control.
 Security System and Access Control of Private Data Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/security-system-and-access-control-of-private-data-image412709301.html
Security System and Access Control of Private Data Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/security-system-and-access-control-of-private-data-image412709301.htmlRF2EYCEWW–Security System and Access Control of Private Data
 Hacker working on a code. Programming code on screen. Internet crime concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-image-hacker-working-on-a-code-programming-code-on-screen-internet-crime-161299451.html
Hacker working on a code. Programming code on screen. Internet crime concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-image-hacker-working-on-a-code-programming-code-on-screen-internet-crime-161299451.htmlRFKABR2K–Hacker working on a code. Programming code on screen. Internet crime concept
RFF0JN09–Car center console and smart phone display hacker icon. Concept for cyber crime in Today's car life.
 National Cyber Security Awareness Month. Vector stock illustration Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/national-cyber-security-awareness-month-vector-stock-illustration-image451892591.html
National Cyber Security Awareness Month. Vector stock illustration Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/national-cyber-security-awareness-month-vector-stock-illustration-image451892591.htmlRF2H75DH3–National Cyber Security Awareness Month. Vector stock illustration
RF2P0XKJH–Surveillance camera about to examine some people icons passing in front of it. Digital illustration.
 Red word 'Ransomware' hidden in the middle of a binary code sequence. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/red-word-ransomware-hidden-in-the-middle-of-a-binary-code-sequence-image463657291.html
Red word 'Ransomware' hidden in the middle of a binary code sequence. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/red-word-ransomware-hidden-in-the-middle-of-a-binary-code-sequence-image463657291.htmlRF2HX9BGY–Red word 'Ransomware' hidden in the middle of a binary code sequence.
 High tech IT cyber crime arrest concept, image of police handcuffs over computer keyboard, selective focus Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/high-tech-it-cyber-crime-arrest-concept-image-of-police-handcuffs-over-computer-keyboard-selective-focus-image576256746.html
High tech IT cyber crime arrest concept, image of police handcuffs over computer keyboard, selective focus Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/high-tech-it-cyber-crime-arrest-concept-image-of-police-handcuffs-over-computer-keyboard-selective-focus-image576256746.htmlRF2TDENA2–High tech IT cyber crime arrest concept, image of police handcuffs over computer keyboard, selective focus
 Driving through the access data tunnel Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/driving-through-the-access-data-tunnel-image483515623.html
Driving through the access data tunnel Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/driving-through-the-access-data-tunnel-image483515623.htmlRF2K2J133–Driving through the access data tunnel
RF2F4EMBM–Fingerprint under magnifying glass vector line icon, Crime investigation and digital access control symbol
 A hacker behind binary code, stream of data, able to break through cyber security and reaches his hand out to control your personal identity Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/a-hacker-behind-binary-code-stream-of-data-able-to-break-through-cyber-security-and-reaches-his-hand-out-to-control-your-personal-identity-image565818840.html
A hacker behind binary code, stream of data, able to break through cyber security and reaches his hand out to control your personal identity Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/a-hacker-behind-binary-code-stream-of-data-able-to-break-through-cyber-security-and-reaches-his-hand-out-to-control-your-personal-identity-image565818840.htmlRF2RTF7KM–A hacker behind binary code, stream of data, able to break through cyber security and reaches his hand out to control your personal identity
 Cyber crime concept. Metal handcuffs and electronic devices on wooden background, 3d illustration Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-crime-concept-metal-handcuffs-and-electronic-devices-on-wooden-background-3d-illustration-image209934358.html
Cyber crime concept. Metal handcuffs and electronic devices on wooden background, 3d illustration Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-crime-concept-metal-handcuffs-and-electronic-devices-on-wooden-background-3d-illustration-image209934358.htmlRFP5F9BJ–Cyber crime concept. Metal handcuffs and electronic devices on wooden background, 3d illustration
 Cyber security abstract technology banner background. Data protection, information privacy Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-security-abstract-technology-banner-background-data-protection-information-privacy-image248220719.html
Cyber security abstract technology banner background. Data protection, information privacy Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-security-abstract-technology-banner-background-data-protection-information-privacy-image248220719.htmlRFTBRC1K–Cyber security abstract technology banner background. Data protection, information privacy
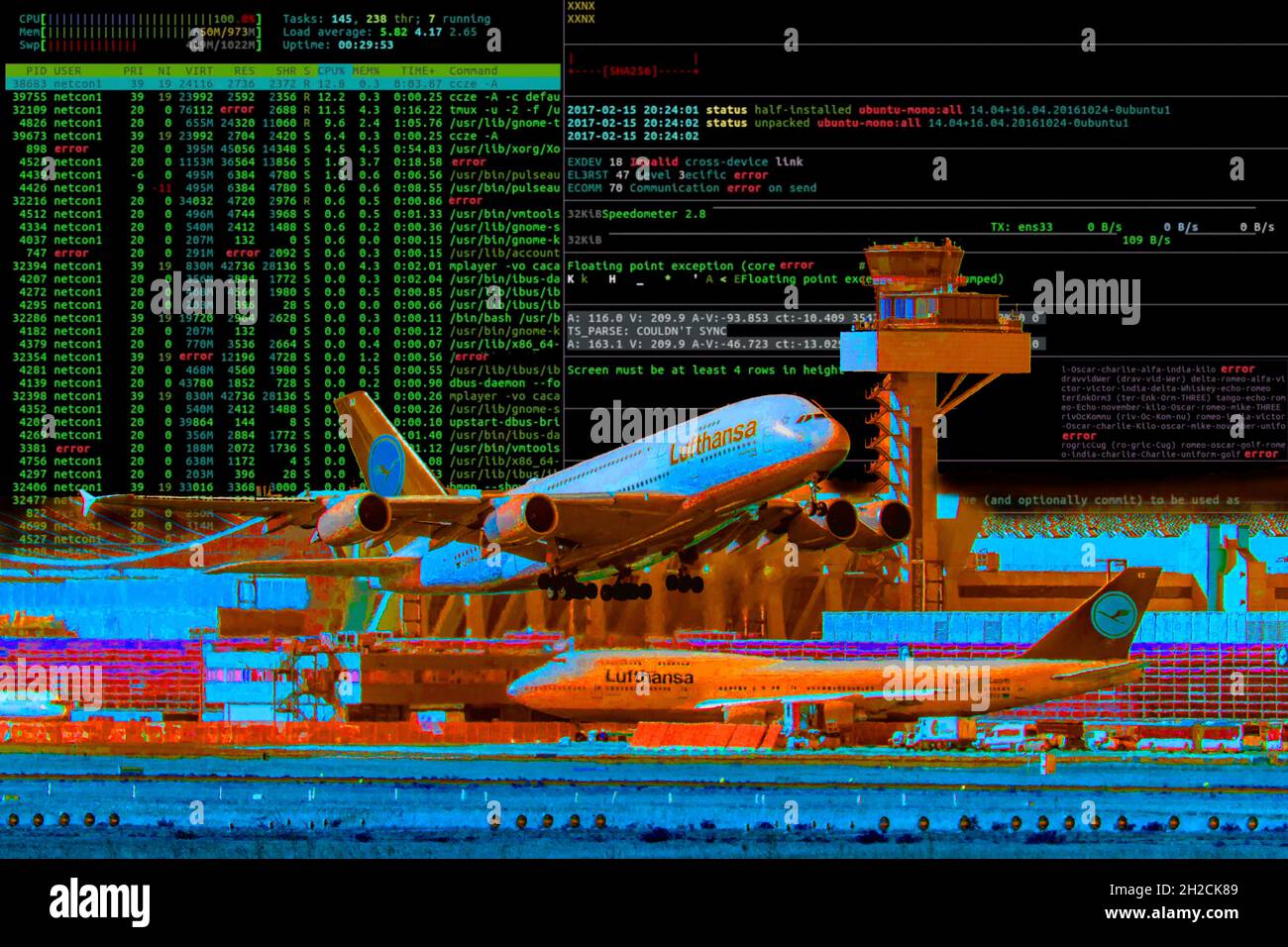 Symbolic image Cybe attack, computer crime, cybercrime, computer hackers attack a city's IT infrastructure, traffic, Frankfurt Airport, Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/symbolic-image-cybe-attack-computer-crime-cybercrime-computer-hackers-attack-a-citys-it-infrastructure-traffic-frankfurt-airport-image448977433.html
Symbolic image Cybe attack, computer crime, cybercrime, computer hackers attack a city's IT infrastructure, traffic, Frankfurt Airport, Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/symbolic-image-cybe-attack-computer-crime-cybercrime-computer-hackers-attack-a-citys-it-infrastructure-traffic-frankfurt-airport-image448977433.htmlRM2H2CK89–Symbolic image Cybe attack, computer crime, cybercrime, computer hackers attack a city's IT infrastructure, traffic, Frankfurt Airport,
RF2WTPH45–Computer problems fixing vector icon. Debugging, virus and errors control outline.
 Business, Technology, Internet and network concept. Young business man, working on the tablet of the future, select on the virtual display: Internal C Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-business-technology-internet-and-network-concept-young-business-man-138964621.html
Business, Technology, Internet and network concept. Young business man, working on the tablet of the future, select on the virtual display: Internal C Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-business-technology-internet-and-network-concept-young-business-man-138964621.htmlRFJ22AP5–Business, Technology, Internet and network concept. Young business man, working on the tablet of the future, select on the virtual display: Internal C
 Anonymous people using computer and programming to break code. Cyber security threat. Internet and network security. Access to private information. An Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/anonymous-people-using-computer-and-programming-to-break-code-cyber-security-threat-internet-and-network-security-access-to-private-information-an-image544466296.html
Anonymous people using computer and programming to break code. Cyber security threat. Internet and network security. Access to private information. An Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/anonymous-people-using-computer-and-programming-to-break-code-cyber-security-threat-internet-and-network-security-access-to-private-information-an-image544466296.htmlRF2PHPG8T–Anonymous people using computer and programming to break code. Cyber security threat. Internet and network security. Access to private information. An
 Computer Security concept. Chain and padlock on keyboard. Cyber security concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/computer-security-concept-chain-and-padlock-on-keyboard-cyber-security-concept-image612418780.html
Computer Security concept. Chain and padlock on keyboard. Cyber security concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/computer-security-concept-chain-and-padlock-on-keyboard-cyber-security-concept-image612418780.htmlRF2XGA2B8–Computer Security concept. Chain and padlock on keyboard. Cyber security concept
 Hooded hacker in dark room performing a cyber attack to a secure access to steal data on internet, laptop computer screen Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/hooded-hacker-in-dark-room-performing-a-cyber-attack-to-a-secure-access-image159002816.html
Hooded hacker in dark room performing a cyber attack to a secure access to steal data on internet, laptop computer screen Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/hooded-hacker-in-dark-room-performing-a-cyber-attack-to-a-secure-access-image159002816.htmlRFK6K5M0–Hooded hacker in dark room performing a cyber attack to a secure access to steal data on internet, laptop computer screen
RF2XH91KK–Access control concept. Businessman using mobile smartphone with virtual access control icon for access security personal data. Automatic access contr
 Security System and Access Control of Private Data Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/security-system-and-access-control-of-private-data-image389622662.html
Security System and Access Control of Private Data Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/security-system-and-access-control-of-private-data-image389622662.htmlRF2DHTRK2–Security System and Access Control of Private Data
 Hacker working on a code in dark room. Programming code on screen. Internet crime concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/hacker-working-on-a-code-in-dark-room-programming-code-on-screen-internet-image157802636.html
Hacker working on a code in dark room. Programming code on screen. Internet crime concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/hacker-working-on-a-code-in-dark-room-programming-code-on-screen-internet-image157802636.htmlRFK4METC–Hacker working on a code in dark room. Programming code on screen. Internet crime concept
 Business, technology, internet and network concept. Young businessman thinks over the steps for successful growth: Cyber crime Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/business-technology-internet-and-network-concept-young-businessman-thinks-over-the-steps-for-successful-growth-cyber-crime-image405115726.html
Business, technology, internet and network concept. Young businessman thinks over the steps for successful growth: Cyber crime Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/business-technology-internet-and-network-concept-young-businessman-thinks-over-the-steps-for-successful-growth-cyber-crime-image405115726.htmlRF2EF2H6P–Business, technology, internet and network concept. Young businessman thinks over the steps for successful growth: Cyber crime
 National Cyber Security Awareness Month. Vector stock illustration. Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/national-cyber-security-awareness-month-vector-stock-illustration-image451892702.html
National Cyber Security Awareness Month. Vector stock illustration. Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/national-cyber-security-awareness-month-vector-stock-illustration-image451892702.htmlRF2H75DN2–National Cyber Security Awareness Month. Vector stock illustration.
 Cyber bullying concept - shadowy figures menace boy at computer Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-cyber-bullying-concept-shadowy-figures-menace-boy-at-computer-21727696.html
Cyber bullying concept - shadowy figures menace boy at computer Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-cyber-bullying-concept-shadowy-figures-menace-boy-at-computer-21727696.htmlRMB79NW4–Cyber bullying concept - shadowy figures menace boy at computer
 Online Security And Cyber Crime Law And Legal Action Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/online-security-and-cyber-crime-law-and-legal-action-image350684735.html
Online Security And Cyber Crime Law And Legal Action Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/online-security-and-cyber-crime-law-and-legal-action-image350684735.htmlRF2BAF1XR–Online Security And Cyber Crime Law And Legal Action
 High tech IT cyber crime arrest concept, image of police handcuffs over computer keyboard, selective focus Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/high-tech-it-cyber-crime-arrest-concept-image-of-police-handcuffs-over-computer-keyboard-selective-focus-image591959123.html
High tech IT cyber crime arrest concept, image of police handcuffs over computer keyboard, selective focus Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/high-tech-it-cyber-crime-arrest-concept-image-of-police-handcuffs-over-computer-keyboard-selective-focus-image591959123.htmlRF2WB21W7–High tech IT cyber crime arrest concept, image of police handcuffs over computer keyboard, selective focus
 Driving through the access data tunnel Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/driving-through-the-access-data-tunnel-image483515625.html
Driving through the access data tunnel Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/driving-through-the-access-data-tunnel-image483515625.htmlRF2K2J135–Driving through the access data tunnel
 Security Camera Surveillance - CCTV Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/security-camera-surveillance-cctv-image272133126.html
Security Camera Surveillance - CCTV Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/security-camera-surveillance-cctv-image272133126.htmlRFWPMMG6–Security Camera Surveillance - CCTV
 A hacker behind binary code, stream of data, able to break through cyber security and reaches his hand out to control your personal identity Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/a-hacker-behind-binary-code-stream-of-data-able-to-break-through-cyber-security-and-reaches-his-hand-out-to-control-your-personal-identity-image565818823.html
A hacker behind binary code, stream of data, able to break through cyber security and reaches his hand out to control your personal identity Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/a-hacker-behind-binary-code-stream-of-data-able-to-break-through-cyber-security-and-reaches-his-hand-out-to-control-your-personal-identity-image565818823.htmlRF2RTF7K3–A hacker behind binary code, stream of data, able to break through cyber security and reaches his hand out to control your personal identity
 Cyber crime concept. Metal handcuffs and judge gavel on computer keyboard, 3d illustration Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-crime-concept-metal-handcuffs-and-judge-gavel-on-computer-keyboard-3d-illustration-image209934364.html
Cyber crime concept. Metal handcuffs and judge gavel on computer keyboard, 3d illustration Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-crime-concept-metal-handcuffs-and-judge-gavel-on-computer-keyboard-3d-illustration-image209934364.htmlRFP5F9BT–Cyber crime concept. Metal handcuffs and judge gavel on computer keyboard, 3d illustration
 Cyber security abstract technology banner background. Data protection, information privacy Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-security-abstract-technology-banner-background-data-protection-information-privacy-image247191490.html
Cyber security abstract technology banner background. Data protection, information privacy Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-security-abstract-technology-banner-background-data-protection-information-privacy-image247191490.htmlRFTA4F7E–Cyber security abstract technology banner background. Data protection, information privacy
 Red word 'Password' hidden in the middle of a binary code sequence. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/red-word-password-hidden-in-the-middle-of-a-binary-code-sequence-image466561114.html
Red word 'Password' hidden in the middle of a binary code sequence. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/red-word-password-hidden-in-the-middle-of-a-binary-code-sequence-image466561114.htmlRF2J31KCX–Red word 'Password' hidden in the middle of a binary code sequence.
 Protecting all personal data on your computer. Cyber security concept banner with laptop and security elements, data encryption, verification Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/protecting-all-personal-data-on-your-computer-cyber-security-concept-banner-with-laptop-and-security-elements-data-encryption-verification-image426262324.html
Protecting all personal data on your computer. Cyber security concept banner with laptop and security elements, data encryption, verification Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/protecting-all-personal-data-on-your-computer-cyber-security-concept-banner-with-laptop-and-security-elements-data-encryption-verification-image426262324.htmlRF2FNDWXC–Protecting all personal data on your computer. Cyber security concept banner with laptop and security elements, data encryption, verification
 Business, Technology, Internet and network concept. Young business man, working on the tablet of the future, select on the virtual display: Lock Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-business-technology-internet-and-network-concept-young-business-man-138964572.html
Business, Technology, Internet and network concept. Young business man, working on the tablet of the future, select on the virtual display: Lock Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-business-technology-internet-and-network-concept-young-business-man-138964572.htmlRFJ22AMC–Business, Technology, Internet and network concept. Young business man, working on the tablet of the future, select on the virtual display: Lock
 Cyber Attack, Cyber hacker accessing somebody else's computer programme Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-image-cyber-attack-cyber-hacker-accessing-somebody-elses-computer-programme-165896854.html
Cyber Attack, Cyber hacker accessing somebody else's computer programme Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-image-cyber-attack-cyber-hacker-accessing-somebody-elses-computer-programme-165896854.htmlRFKHW73J–Cyber Attack, Cyber hacker accessing somebody else's computer programme
 Security on digital tablet. Chain and padlock on tablet. Cyber security on digital devices concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/security-on-digital-tablet-chain-and-padlock-on-tablet-cyber-security-on-digital-devices-concept-image612418777.html
Security on digital tablet. Chain and padlock on tablet. Cyber security on digital devices concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/security-on-digital-tablet-chain-and-padlock-on-tablet-cyber-security-on-digital-devices-concept-image612418777.htmlRF2XGA2B5–Security on digital tablet. Chain and padlock on tablet. Cyber security on digital devices concept
 A creative illustration to convey the idea of having 'no control' over something. The text no ctrl on a computer keyboard button Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/a-creative-illustration-to-convey-the-idea-of-having-no-control-over-something-the-text-no-ctrl-on-a-computer-keyboard-button-image488915478.html
A creative illustration to convey the idea of having 'no control' over something. The text no ctrl on a computer keyboard button Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/a-creative-illustration-to-convey-the-idea-of-having-no-control-over-something-the-text-no-ctrl-on-a-computer-keyboard-button-image488915478.htmlRF2KBC0K2–A creative illustration to convey the idea of having 'no control' over something. The text no ctrl on a computer keyboard button
 Security Violation - Infographical Concept Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-security-violation-infographical-concept-143419808.html
Security Violation - Infographical Concept Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-security-violation-infographical-concept-143419808.htmlRFJ999C0–Security Violation - Infographical Concept
 Security System and Access Control of Private Data Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/security-system-and-access-control-of-private-data-image357645643.html
Security System and Access Control of Private Data Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/security-system-and-access-control-of-private-data-image357645643.htmlRF2BNT4JK–Security System and Access Control of Private Data
 Faceless hooded anonymous computer hacker on Ukrainian flag background. Internet crime and electronic banking security. Hacker Attack, Virus Infected Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/faceless-hooded-anonymous-computer-hacker-on-ukrainian-flag-background-internet-crime-and-electronic-banking-security-hacker-attack-virus-infected-image466596494.html
Faceless hooded anonymous computer hacker on Ukrainian flag background. Internet crime and electronic banking security. Hacker Attack, Virus Infected Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/faceless-hooded-anonymous-computer-hacker-on-ukrainian-flag-background-internet-crime-and-electronic-banking-security-hacker-attack-virus-infected-image466596494.htmlRF2J338GE–Faceless hooded anonymous computer hacker on Ukrainian flag background. Internet crime and electronic banking security. Hacker Attack, Virus Infected
 Business, technology, internet and network concept. Young businessman thinks over the steps for successful growth: Cyber crime Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/business-technology-internet-and-network-concept-young-businessman-thinks-over-the-steps-for-successful-growth-cyber-crime-image415586472.html
Business, technology, internet and network concept. Young businessman thinks over the steps for successful growth: Cyber crime Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/business-technology-internet-and-network-concept-young-businessman-thinks-over-the-steps-for-successful-growth-cyber-crime-image415586472.htmlRF2F43GP0–Business, technology, internet and network concept. Young businessman thinks over the steps for successful growth: Cyber crime
 Computer at home with text: 'I'm watching, whatever you do' Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/computer-at-home-with-text-im-watching-whatever-you-do-image478256378.html
Computer at home with text: 'I'm watching, whatever you do' Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/computer-at-home-with-text-im-watching-whatever-you-do-image478256378.htmlRF2JP2CTX–Computer at home with text: 'I'm watching, whatever you do'
 Cyber bullying concept - Three shadows menace boy at computer Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-cyber-bullying-concept-three-shadows-menace-boy-at-computer-13283287.html
Cyber bullying concept - Three shadows menace boy at computer Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-cyber-bullying-concept-three-shadows-menace-boy-at-computer-13283287.htmlRMAD2G7M–Cyber bullying concept - Three shadows menace boy at computer
 2d Illustration Fingerprint Scanning Technology Concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/2d-illustration-fingerprint-scanning-technology-concept-image482339224.html
2d Illustration Fingerprint Scanning Technology Concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/2d-illustration-fingerprint-scanning-technology-concept-image482339224.htmlRF2K0MCGT–2d Illustration Fingerprint Scanning Technology Concept
 Computer Security. Vector stock illustration. Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/computer-security-vector-stock-illustration-image451892714.html
Computer Security. Vector stock illustration. Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/computer-security-vector-stock-illustration-image451892714.htmlRF2H75DNE–Computer Security. Vector stock illustration.
 Driving through the access data tunnel Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/driving-through-the-access-data-tunnel-image483515272.html
Driving through the access data tunnel Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/driving-through-the-access-data-tunnel-image483515272.htmlRF2K2J0JG–Driving through the access data tunnel
 Security Camera Surveillance - CCTV. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/security-camera-surveillance-cctv-image246642766.html
Security Camera Surveillance - CCTV. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/security-camera-surveillance-cctv-image246642766.htmlRFT97FA6–Security Camera Surveillance - CCTV.
 A hacker behind binary code, stream of data, able to break through cyber security and reaches his hand out to steal your personal information Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/a-hacker-behind-binary-code-stream-of-data-able-to-break-through-cyber-security-and-reaches-his-hand-out-to-steal-your-personal-information-image565818813.html
A hacker behind binary code, stream of data, able to break through cyber security and reaches his hand out to steal your personal information Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/a-hacker-behind-binary-code-stream-of-data-able-to-break-through-cyber-security-and-reaches-his-hand-out-to-steal-your-personal-information-image565818813.htmlRF2RTF7JN–A hacker behind binary code, stream of data, able to break through cyber security and reaches his hand out to steal your personal information
RF2T5RAFR–Cyber security banner web icon vector illustration concept with icon of application, information, network, operational, encryption, access control
 Cyber security abstract technology banner background. Data protection, information privacy Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-security-abstract-technology-banner-background-data-protection-information-privacy-image245694358.html
Cyber security abstract technology banner background. Data protection, information privacy Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-security-abstract-technology-banner-background-data-protection-information-privacy-image245694358.htmlRFT7M9JE–Cyber security abstract technology banner background. Data protection, information privacy
 Red word 'Cyberwarfare' hidden in the middle of a binary code sequence. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/red-word-cyberwarfare-hidden-in-the-middle-of-a-binary-code-sequence-image463148611.html
Red word 'Cyberwarfare' hidden in the middle of a binary code sequence. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/red-word-cyberwarfare-hidden-in-the-middle-of-a-binary-code-sequence-image463148611.htmlRF2HWE6NR–Red word 'Cyberwarfare' hidden in the middle of a binary code sequence.
 Biometric cyber security system and access control concept. Businessman access security personal financial data on scan fingerprint identification. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/biometric-cyber-security-system-and-access-control-concept-businessman-access-security-personal-financial-data-on-scan-fingerprint-identification-image609335031.html
Biometric cyber security system and access control concept. Businessman access security personal financial data on scan fingerprint identification. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/biometric-cyber-security-system-and-access-control-concept-businessman-access-security-personal-financial-data-on-scan-fingerprint-identification-image609335031.htmlRF2XB9H1B–Biometric cyber security system and access control concept. Businessman access security personal financial data on scan fingerprint identification.
 Business, Technology, Internet and network concept. Young business man, working on the tablet of the future, select on the virtual display: Privacy Se Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-business-technology-internet-and-network-concept-young-business-man-138964547.html
Business, Technology, Internet and network concept. Young business man, working on the tablet of the future, select on the virtual display: Privacy Se Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-business-technology-internet-and-network-concept-young-business-man-138964547.htmlRFJ22AKF–Business, Technology, Internet and network concept. Young business man, working on the tablet of the future, select on the virtual display: Privacy Se
 Data Control - Text on Small Chalkboard. 3d. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-data-control-text-on-small-chalkboard-3d-135875492.html
Data Control - Text on Small Chalkboard. 3d. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-data-control-text-on-small-chalkboard-3d-135875492.htmlRFHW1JG4–Data Control - Text on Small Chalkboard. 3d.
 Security on smartphone, chain and padlock on smart phone. Cyber security on digital devices concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/security-on-smartphone-chain-and-padlock-on-smart-phone-cyber-security-on-digital-devices-concept-image612418788.html
Security on smartphone, chain and padlock on smart phone. Cyber security on digital devices concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/security-on-smartphone-chain-and-padlock-on-smart-phone-cyber-security-on-digital-devices-concept-image612418788.htmlRF2XGA2BG–Security on smartphone, chain and padlock on smart phone. Cyber security on digital devices concept
 The concept of something being 'out of control' using the ctrl button on a computer keyboard. Losing control or bad management concept. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/the-concept-of-something-being-out-of-control-using-the-ctrl-button-on-a-computer-keyboard-losing-control-or-bad-management-concept-image488915546.html
The concept of something being 'out of control' using the ctrl button on a computer keyboard. Losing control or bad management concept. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/the-concept-of-something-being-out-of-control-using-the-ctrl-button-on-a-computer-keyboard-losing-control-or-bad-management-concept-image488915546.htmlRF2KBC0NE–The concept of something being 'out of control' using the ctrl button on a computer keyboard. Losing control or bad management concept.
 Global hacker network Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/global-hacker-network-image185307338.html
Global hacker network Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/global-hacker-network-image185307338.htmlRFMNDDB6–Global hacker network
 Cyber eye symbol 3d illustration. Digital background with space for contents. Abstract futuristic concept of digital surveillance, spying, hacking and Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-eye-symbol-3d-illustration-digital-background-with-space-for-contents-abstract-futuristic-concept-of-digital-surveillance-spying-hacking-and-image272542387.html
Cyber eye symbol 3d illustration. Digital background with space for contents. Abstract futuristic concept of digital surveillance, spying, hacking and Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-eye-symbol-3d-illustration-digital-background-with-space-for-contents-abstract-futuristic-concept-of-digital-surveillance-spying-hacking-and-image272542387.htmlRFWRBAGK–Cyber eye symbol 3d illustration. Digital background with space for contents. Abstract futuristic concept of digital surveillance, spying, hacking and
 Hardware Firewall. Cyber Security Isometric Concept. Vector Illustration. Gateway Preventing Cyber Attacks. Protecting Data and Confidentiality. Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/hardware-firewall-cyber-security-isometric-concept-vector-illustration-gateway-preventing-cyber-attacks-protecting-data-and-confidentiality-image406656729.html
Hardware Firewall. Cyber Security Isometric Concept. Vector Illustration. Gateway Preventing Cyber Attacks. Protecting Data and Confidentiality. Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/hardware-firewall-cyber-security-isometric-concept-vector-illustration-gateway-preventing-cyber-attacks-protecting-data-and-confidentiality-image406656729.htmlRF2EHGPPH–Hardware Firewall. Cyber Security Isometric Concept. Vector Illustration. Gateway Preventing Cyber Attacks. Protecting Data and Confidentiality.
 Business, technology, internet and network concept. A young businessman collects information to become successful: Cyber crime Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/business-technology-internet-and-network-concept-a-young-businessman-collects-information-to-become-successful-cyber-crime-image398058641.html
Business, technology, internet and network concept. A young businessman collects information to become successful: Cyber crime Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/business-technology-internet-and-network-concept-a-young-businessman-collects-information-to-become-successful-cyber-crime-image398058641.htmlRF2E3H3T1–Business, technology, internet and network concept. A young businessman collects information to become successful: Cyber crime
 Computer at home with text:someone is watching you Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/computer-at-home-with-textsomeone-is-watching-you-image478256379.html
Computer at home with text:someone is watching you Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/computer-at-home-with-textsomeone-is-watching-you-image478256379.htmlRF2JP2CTY–Computer at home with text:someone is watching you
 Cyber bullying concept - Three shadows menace boy at computer Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-cyber-bullying-concept-three-shadows-menace-boy-at-computer-13283283.html
Cyber bullying concept - Three shadows menace boy at computer Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-cyber-bullying-concept-three-shadows-menace-boy-at-computer-13283283.htmlRMAD2G7G–Cyber bullying concept - Three shadows menace boy at computer
 2d Illustration Fingerprint Scanning Technology Concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/2d-illustration-fingerprint-scanning-technology-concept-image482339217.html
2d Illustration Fingerprint Scanning Technology Concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/2d-illustration-fingerprint-scanning-technology-concept-image482339217.htmlRF2K0MCGH–2d Illustration Fingerprint Scanning Technology Concept
 Computer Security Day. Vector stock illustration. Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/computer-security-day-vector-stock-illustration-image451892661.html
Computer Security Day. Vector stock illustration. Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/computer-security-day-vector-stock-illustration-image451892661.htmlRF2H75DKH–Computer Security Day. Vector stock illustration.
 Access data concept on rotating sphere Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/access-data-concept-on-rotating-sphere-image483515277.html
Access data concept on rotating sphere Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/access-data-concept-on-rotating-sphere-image483515277.htmlRF2K2J0JN–Access data concept on rotating sphere
 Security Camera Surveillance - CCTV. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/security-camera-surveillance-cctv-image246642741.html
Security Camera Surveillance - CCTV. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/security-camera-surveillance-cctv-image246642741.htmlRFT97F99–Security Camera Surveillance - CCTV.
 A hacker behind binary code, a stream of data, unlocks cyber security by hacking your username and password Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/a-hacker-behind-binary-code-a-stream-of-data-unlocks-cyber-security-by-hacking-your-username-and-password-image565818836.html
A hacker behind binary code, a stream of data, unlocks cyber security by hacking your username and password Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/a-hacker-behind-binary-code-a-stream-of-data-unlocks-cyber-security-by-hacking-your-username-and-password-image565818836.htmlRF2RTF7KG–A hacker behind binary code, a stream of data, unlocks cyber security by hacking your username and password
 Screen of laptop computer showing alert that the computer was attacked by ransomware. 3D rendering image with clipping path. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-screen-of-laptop-computer-showing-alert-that-the-computer-was-attacked-105312360.html
Screen of laptop computer showing alert that the computer was attacked by ransomware. 3D rendering image with clipping path. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-screen-of-laptop-computer-showing-alert-that-the-computer-was-attacked-105312360.htmlRFG39AYM–Screen of laptop computer showing alert that the computer was attacked by ransomware. 3D rendering image with clipping path.
 Hooded computer hacker with tablet computer, red and blue light low key image Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/hooded-computer-hacker-with-tablet-computer-red-and-blue-light-low-key-image-image182999389.html
Hooded computer hacker with tablet computer, red and blue light low key image Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/hooded-computer-hacker-with-tablet-computer-red-and-blue-light-low-key-image-image182999389.htmlRFMHM9GD–Hooded computer hacker with tablet computer, red and blue light low key image
 Red word 'Doxxing' hidden in the middle of a binary code sequence. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/red-word-doxxing-hidden-in-the-middle-of-a-binary-code-sequence-image465613470.html
Red word 'Doxxing' hidden in the middle of a binary code sequence. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/red-word-doxxing-hidden-in-the-middle-of-a-binary-code-sequence-image465613470.htmlRF2J1EEME–Red word 'Doxxing' hidden in the middle of a binary code sequence.
 Closeup of handcuffs on laptop at table Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/closeup-of-handcuffs-on-laptop-at-table-image159954902.html
Closeup of handcuffs on laptop at table Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/closeup-of-handcuffs-on-laptop-at-table-image159954902.htmlRFK86G32–Closeup of handcuffs on laptop at table
 Business, Technology, Internet and network concept. Young business man, working on the tablet of the future, select on the virtual display Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-business-technology-internet-and-network-concept-young-business-man-138964557.html
Business, Technology, Internet and network concept. Young business man, working on the tablet of the future, select on the virtual display Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-business-technology-internet-and-network-concept-young-business-man-138964557.htmlRFJ22AKW–Business, Technology, Internet and network concept. Young business man, working on the tablet of the future, select on the virtual display
 Data Control Concept on Clipboard. 3D. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-data-control-concept-on-clipboard-3d-125830262.html
Data Control Concept on Clipboard. 3D. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-data-control-concept-on-clipboard-3d-125830262.htmlRFH8M1NX–Data Control Concept on Clipboard. 3D.
 Russia bans internet, hacker cyber attack concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/russia-bans-internet-hacker-cyber-attack-concept-image477561200.html
Russia bans internet, hacker cyber attack concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/russia-bans-internet-hacker-cyber-attack-concept-image477561200.htmlRF2JMXP54–Russia bans internet, hacker cyber attack concept
 hacker attacked computer chip while business worker can work under firewall protection. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/hacker-attacked-computer-chip-while-business-worker-can-work-under-firewall-protection-image599083727.html
hacker attacked computer chip while business worker can work under firewall protection. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/hacker-attacked-computer-chip-while-business-worker-can-work-under-firewall-protection-image599083727.htmlRF2WPJHBB–hacker attacked computer chip while business worker can work under firewall protection.
 Global hacker network Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/global-hacker-network-image184905385.html
Global hacker network Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/global-hacker-network-image184905385.htmlRFMMR4KN–Global hacker network
 Digital protection by fingerprint authorization on cyber background. Personal identification technology and digital security with hand finger verifica Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/digital-protection-by-fingerprint-authorization-on-cyber-background-personal-identification-technology-and-digital-security-with-hand-finger-verifica-image244388294.html
Digital protection by fingerprint authorization on cyber background. Personal identification technology and digital security with hand finger verifica Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/digital-protection-by-fingerprint-authorization-on-cyber-background-personal-identification-technology-and-digital-security-with-hand-finger-verifica-image244388294.htmlRFT5GRNA–Digital protection by fingerprint authorization on cyber background. Personal identification technology and digital security with hand finger verifica
 Concept of hacking and malware. Hacker using an abstract laptop with a binary code digital interface. Young hacker in cybersecurity concept. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/concept-of-hacking-and-malware-hacker-using-an-abstract-laptop-with-a-binary-code-digital-interface-young-hacker-in-cybersecurity-concept-image469237582.html
Concept of hacking and malware. Hacker using an abstract laptop with a binary code digital interface. Young hacker in cybersecurity concept. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/concept-of-hacking-and-malware-hacker-using-an-abstract-laptop-with-a-binary-code-digital-interface-young-hacker-in-cybersecurity-concept-image469237582.htmlRM2J7BH92–Concept of hacking and malware. Hacker using an abstract laptop with a binary code digital interface. Young hacker in cybersecurity concept.
 Business, technology, internet and network concept. Young businessman thinks over the steps for successful growth: Cyber crime Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/business-technology-internet-and-network-concept-young-businessman-thinks-over-the-steps-for-successful-growth-cyber-crime-image418279969.html
Business, technology, internet and network concept. Young businessman thinks over the steps for successful growth: Cyber crime Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/business-technology-internet-and-network-concept-young-businessman-thinks-over-the-steps-for-successful-growth-cyber-crime-image418279969.htmlRF2F8E8A9–Business, technology, internet and network concept. Young businessman thinks over the steps for successful growth: Cyber crime