Quick filters:
Web threat Stock Photos and Images
 Web threat Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/web-threat-image343623633.html
Web threat Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/web-threat-image343623633.htmlRM2AY1BCH–Web threat
RF2CE8ND5–Pixel Skull,Computer virus, blue background. Illustration of Abstract Skull sign with destroyed binary codes. Web Hacking. Online piracy concept.
 Meltdown and spectre threat concept on laptop screen. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-meltdown-and-spectre-threat-concept-on-laptop-screen-171250943.html
Meltdown and spectre threat concept on laptop screen. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-meltdown-and-spectre-threat-concept-on-laptop-screen-171250943.htmlRFKXH493–Meltdown and spectre threat concept on laptop screen.
 Update police incident television news banner. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/update-police-incident-television-news-banner-image550899201.html
Update police incident television news banner. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/update-police-incident-television-news-banner-image550899201.htmlRF2R07HFD–Update police incident television news banner.
 Computer Trojan Showing Web Site And Threat Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-computer-trojan-showing-web-site-and-threat-122175833.html
Computer Trojan Showing Web Site And Threat Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-computer-trojan-showing-web-site-and-threat-122175833.htmlRFH2NGEH–Computer Trojan Showing Web Site And Threat
 Cyber security threat, attack and online crime concept. Hacker writing with laptop computer wearing leather gloves. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-cyber-security-threat-attack-and-online-crime-concept-hacker-writing-174795322.html
Cyber security threat, attack and online crime concept. Hacker writing with laptop computer wearing leather gloves. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-cyber-security-threat-attack-and-online-crime-concept-hacker-writing-174795322.htmlRFM4AH62–Cyber security threat, attack and online crime concept. Hacker writing with laptop computer wearing leather gloves.
 Access internet web www key data protection lock computer security online threat Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-access-internet-web-www-key-data-protection-lock-computer-security-91295092.html
Access internet web www key data protection lock computer security online threat Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-access-internet-web-www-key-data-protection-lock-computer-security-91295092.htmlRFF8ERR0–Access internet web www key data protection lock computer security online threat
 mygalomorph spider (Macrothele calpeiana), in its web Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/mygalomorph-spider-macrothele-calpeiana-in-its-web-image344737610.html
mygalomorph spider (Macrothele calpeiana), in its web Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/mygalomorph-spider-macrothele-calpeiana-in-its-web-image344737610.htmlRM2B0T49E–mygalomorph spider (Macrothele calpeiana), in its web
 Bullying on the web Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-bullying-on-the-web-111380895.html
Bullying on the web Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-bullying-on-the-web-111380895.htmlRFGD5RD3–Bullying on the web
 Cityscape merging with digital overlays, displaying neon warnings Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cityscape-merging-with-digital-overlays-displaying-neon-warnings-image607598026.html
Cityscape merging with digital overlays, displaying neon warnings Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cityscape-merging-with-digital-overlays-displaying-neon-warnings-image607598026.htmlRF2X8EDDE–Cityscape merging with digital overlays, displaying neon warnings
 MI5 website www UK threat information web page Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-mi5-website-www-uk-threat-information-web-page-48097269.html
MI5 website www UK threat information web page Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-mi5-website-www-uk-threat-information-web-page-48097269.htmlRMCP70FH–MI5 website www UK threat information web page
RF2HND9RJ–Threat Simple vector icon. Illustration symbol design template for web mobile UI element.
 Driving through the data transmission tunnel Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/driving-through-the-data-transmission-tunnel-image483553808.html
Driving through the data transmission tunnel Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/driving-through-the-data-transmission-tunnel-image483553808.htmlRF2K2KNPT–Driving through the data transmission tunnel
 Driving through the dirty data tunnel Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/driving-through-the-dirty-data-tunnel-image483550571.html
Driving through the dirty data tunnel Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/driving-through-the-dirty-data-tunnel-image483550571.htmlRF2K2KHK7–Driving through the dirty data tunnel
 Hacked monitor. Ransomware. Binary digital numbers on red screen with ransom word on screen. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-image-hacked-monitor-ransomware-binary-digital-numbers-on-red-screen-with-164670735.html
Hacked monitor. Ransomware. Binary digital numbers on red screen with ransom word on screen. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-image-hacked-monitor-ransomware-binary-digital-numbers-on-red-screen-with-164670735.htmlRFKFWB5K–Hacked monitor. Ransomware. Binary digital numbers on red screen with ransom word on screen.
 Phishing scam, hacker attack and web security vector concept. Illustration of phishing and fraud, online scam and steal Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/phishing-scam-hacker-attack-and-web-security-vector-concept-illustration-of-phishing-and-fraud-online-scam-and-steal-image353046537.html
Phishing scam, hacker attack and web security vector concept. Illustration of phishing and fraud, online scam and steal Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/phishing-scam-hacker-attack-and-web-security-vector-concept-illustration-of-phishing-and-fraud-online-scam-and-steal-image353046537.htmlRF2BEAJCW–Phishing scam, hacker attack and web security vector concept. Illustration of phishing and fraud, online scam and steal
 Greylag Goose (Anser anser). High intensity threat. Gander challenging a perceived threat, head on. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-greylag-goose-anser-anser-high-intensity-threat-gander-challenging-114496911.html
Greylag Goose (Anser anser). High intensity threat. Gander challenging a perceived threat, head on. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-greylag-goose-anser-anser-high-intensity-threat-gander-challenging-114496911.htmlRMGJ7NYB–Greylag Goose (Anser anser). High intensity threat. Gander challenging a perceived threat, head on.
 Computer System Security Under Threat Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/computer-system-security-under-threat-image226028173.html
Computer System Security Under Threat Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/computer-system-security-under-threat-image226028173.htmlRFR3MD6N–Computer System Security Under Threat
 ORB WEAVER Spider Neoscona arabesca The orb-weaver spiders (family Araneidae) are the builders of spiral wheel-shaped webs Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-orb-weaver-spider-neoscona-arabesca-the-orb-weaver-spiders-family-16686344.html
ORB WEAVER Spider Neoscona arabesca The orb-weaver spiders (family Araneidae) are the builders of spiral wheel-shaped webs Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-orb-weaver-spider-neoscona-arabesca-the-orb-weaver-spiders-family-16686344.htmlRFAX08BN–ORB WEAVER Spider Neoscona arabesca The orb-weaver spiders (family Araneidae) are the builders of spiral wheel-shaped webs
 Close up of a brown spider on its web, against a black background Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/close-up-of-a-brown-spider-on-its-web-against-a-black-background-image337634180.html
Close up of a brown spider on its web, against a black background Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/close-up-of-a-brown-spider-on-its-web-against-a-black-background-image337634180.htmlRF2AH8FRG–Close up of a brown spider on its web, against a black background
 Skull symbol,Computer virus, background. Illustration of Abstract Skull sign with destroyed binary codes. Web Hacking. Online piracy concept. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/skull-symbolcomputer-virus-background-illustration-of-abstract-skull-sign-with-destroyed-binary-codes-web-hacking-online-piracy-concept-image371229726.html
Skull symbol,Computer virus, background. Illustration of Abstract Skull sign with destroyed binary codes. Web Hacking. Online piracy concept. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/skull-symbolcomputer-virus-background-illustration-of-abstract-skull-sign-with-destroyed-binary-codes-web-hacking-online-piracy-concept-image371229726.htmlRF2CFXY8E–Skull symbol,Computer virus, background. Illustration of Abstract Skull sign with destroyed binary codes. Web Hacking. Online piracy concept.
 Meltdown and spectre threat concept on laptop and smartphone screen. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-meltdown-and-spectre-threat-concept-on-laptop-and-smartphone-screen-171251136.html
Meltdown and spectre threat concept on laptop and smartphone screen. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-meltdown-and-spectre-threat-concept-on-laptop-and-smartphone-screen-171251136.htmlRFKXH4G0–Meltdown and spectre threat concept on laptop and smartphone screen.
 Working fire television news banner. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/working-fire-television-news-banner-image550899176.html
Working fire television news banner. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/working-fire-television-news-banner-image550899176.htmlRF2R07HEG–Working fire television news banner.
 Cyber Attack By North Korean Criminal Hack 3d Illustration. Shows Hacking By Korea And Virus Or Global Web Threat To Data Integrity Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-attack-by-north-korean-criminal-hack-3d-illustration-shows-hacking-by-korea-and-virus-or-global-web-threat-to-data-integrity-image208317120.html
Cyber Attack By North Korean Criminal Hack 3d Illustration. Shows Hacking By Korea And Virus Or Global Web Threat To Data Integrity Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-attack-by-north-korean-criminal-hack-3d-illustration-shows-hacking-by-korea-and-virus-or-global-web-threat-to-data-integrity-image208317120.htmlRFP2WJH4–Cyber Attack By North Korean Criminal Hack 3d Illustration. Shows Hacking By Korea And Virus Or Global Web Threat To Data Integrity
 Hacker code in laptop. Cyber security, privacy or hack threat. Coder or programmer writing virus software, malware, internet attack. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/hacker-code-in-laptop-cyber-security-privacy-or-hack-threat-coder-or-programmer-writing-virus-software-malware-internet-attack-image465435401.html
Hacker code in laptop. Cyber security, privacy or hack threat. Coder or programmer writing virus software, malware, internet attack. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/hacker-code-in-laptop-cyber-security-privacy-or-hack-threat-coder-or-programmer-writing-virus-software-malware-internet-attack-image465435401.htmlRF2J16BGW–Hacker code in laptop. Cyber security, privacy or hack threat. Coder or programmer writing virus software, malware, internet attack.
 New york, USA - April 20, 2023: Virus and threat protection for windows on laptop screen close up view Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/new-york-usa-april-20-2023-virus-and-threat-protection-for-windows-on-laptop-screen-close-up-view-image546977942.html
New york, USA - April 20, 2023: Virus and threat protection for windows on laptop screen close up view Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/new-york-usa-april-20-2023-virus-and-threat-protection-for-windows-on-laptop-screen-close-up-view-image546977942.htmlRF2PNTYXE–New york, USA - April 20, 2023: Virus and threat protection for windows on laptop screen close up view
RFFWTTTD–Gray-orange stylized infection symbol round web icon
RF2T6MNXD–Electrical hazard Caution signs. Symbols of danger and warning signs. warning attention. danger sign. attention vector icon.
 Cityscape overlaid with digital graphics showing cloud and MALWARE DETECTED text Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cityscape-overlaid-with-digital-graphics-showing-cloud-and-malware-detected-text-image607597985.html
Cityscape overlaid with digital graphics showing cloud and MALWARE DETECTED text Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cityscape-overlaid-with-digital-graphics-showing-cloud-and-malware-detected-text-image607597985.htmlRF2X8EDC1–Cityscape overlaid with digital graphics showing cloud and MALWARE DETECTED text
 Yellow shield with a virus symbol and the text Virus Danger - Vector Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/yellow-shield-with-a-virus-symbol-and-the-text-virus-danger-vector-image349194989.html
Yellow shield with a virus symbol and the text Virus Danger - Vector Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/yellow-shield-with-a-virus-symbol-and-the-text-virus-danger-vector-image349194989.htmlRF2B835NH–Yellow shield with a virus symbol and the text Virus Danger - Vector
 Web terrorism concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/web-terrorism-concept-image343623634.html
Web terrorism concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/web-terrorism-concept-image343623634.htmlRM2AY1BCJ–Web terrorism concept
 Driving through the data transmission tunnel Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/driving-through-the-data-transmission-tunnel-image483553887.html
Driving through the data transmission tunnel Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/driving-through-the-data-transmission-tunnel-image483553887.htmlRF2K2KNWK–Driving through the data transmission tunnel
 Driving through the data migration tunnel Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/driving-through-the-data-migration-tunnel-image483550263.html
Driving through the data migration tunnel Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/driving-through-the-data-migration-tunnel-image483550263.htmlRF2K2KH87–Driving through the data migration tunnel
 Hacked monitor. Ransomware. Binary digital numbers on red screen with ransom word on screen. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-image-hacked-monitor-ransomware-binary-digital-numbers-on-red-screen-with-164670663.html
Hacked monitor. Ransomware. Binary digital numbers on red screen with ransom word on screen. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-image-hacked-monitor-ransomware-binary-digital-numbers-on-red-screen-with-164670663.htmlRFKFWB33–Hacked monitor. Ransomware. Binary digital numbers on red screen with ransom word on screen.
 Email virus. Envelope with malware message with skull on laptop screen. E-mail spam, phishing scam and hacker attack vector concept. Spam threat on laptop, virus online malware illustration Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/email-virus-envelope-with-malware-message-with-skull-on-laptop-screen-e-mail-spam-phishing-scam-and-hacker-attack-vector-concept-spam-threat-on-laptop-virus-online-malware-illustration-image357376802.html
Email virus. Envelope with malware message with skull on laptop screen. E-mail spam, phishing scam and hacker attack vector concept. Spam threat on laptop, virus online malware illustration Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/email-virus-envelope-with-malware-message-with-skull-on-laptop-screen-e-mail-spam-phishing-scam-and-hacker-attack-vector-concept-spam-threat-on-laptop-virus-online-malware-illustration-image357376802.htmlRF2BNBWN6–Email virus. Envelope with malware message with skull on laptop screen. E-mail spam, phishing scam and hacker attack vector concept. Spam threat on laptop, virus online malware illustration
 Greylag Goose Anser anser High intensity threat. Gander challenging a perceived threat, or adversary, head on. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-greylag-goose-anser-anser-high-intensity-threat-gander-challenging-114496885.html
Greylag Goose Anser anser High intensity threat. Gander challenging a perceived threat, or adversary, head on. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-greylag-goose-anser-anser-high-intensity-threat-gander-challenging-114496885.htmlRMGJ7NXD–Greylag Goose Anser anser High intensity threat. Gander challenging a perceived threat, or adversary, head on.
 Argiope ansuja spider resting on its web Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/argiope-ansuja-spider-resting-on-its-web-image604465953.html
Argiope ansuja spider resting on its web Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/argiope-ansuja-spider-resting-on-its-web-image604465953.htmlRF2X3BPDN–Argiope ansuja spider resting on its web
 Warning Problem Spam Threat Online Website Concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-warning-problem-spam-threat-online-website-concept-126088470.html
Warning Problem Spam Threat Online Website Concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-warning-problem-spam-threat-online-website-concept-126088470.htmlRFH93R3J–Warning Problem Spam Threat Online Website Concept
 A large spider is sitting on a web stretched in the pantry. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/a-large-spider-is-sitting-on-a-web-stretched-in-the-pantry-image214768293.html
A large spider is sitting on a web stretched in the pantry. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/a-large-spider-is-sitting-on-a-web-stretched-in-the-pantry-image214768293.htmlRFPDBF45–A large spider is sitting on a web stretched in the pantry.
 Skull,Hacker,Computer virus concept. Illustration of Abstract Skull sign with destroyed letters and binary code. Web Hacking. Online piracy concept. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/skullhackercomputer-virus-concept-illustration-of-abstract-skull-sign-with-destroyed-letters-and-binary-code-web-hacking-online-piracy-concept-image361202988.html
Skull,Hacker,Computer virus concept. Illustration of Abstract Skull sign with destroyed letters and binary code. Web Hacking. Online piracy concept. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/skullhackercomputer-virus-concept-illustration-of-abstract-skull-sign-with-destroyed-letters-and-binary-code-web-hacking-online-piracy-concept-image361202988.htmlRF2BYJ62M–Skull,Hacker,Computer virus concept. Illustration of Abstract Skull sign with destroyed letters and binary code. Web Hacking. Online piracy concept.
 Chipocalypse concept with meltdown and spectre threat word cloud on laptop screen. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-chipocalypse-concept-with-meltdown-and-spectre-threat-word-cloud-on-171250870.html
Chipocalypse concept with meltdown and spectre threat word cloud on laptop screen. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-chipocalypse-concept-with-meltdown-and-spectre-threat-word-cloud-on-171250870.htmlRFKXH46E–Chipocalypse concept with meltdown and spectre threat word cloud on laptop screen.
 Breaking news television news banner Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/breaking-news-television-news-banner-image550899180.html
Breaking news television news banner Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/breaking-news-television-news-banner-image550899180.htmlRF2R07HEM–Breaking news television news banner
 Hand writing sign Insider Threat. Concept meaning security threat that originates from within the organization Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/hand-writing-sign-insider-threat-concept-meaning-security-threat-that-originates-from-within-the-organization-image547471272.html
Hand writing sign Insider Threat. Concept meaning security threat that originates from within the organization Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/hand-writing-sign-insider-threat-concept-meaning-security-threat-that-originates-from-within-the-organization-image547471272.htmlRM2PPKD5C–Hand writing sign Insider Threat. Concept meaning security threat that originates from within the organization
 Data and cyber security threat concept. Online financial crime, identity theft and internet scam. Laptop computer keyboard in spotlight. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-data-and-cyber-security-threat-concept-online-financial-crime-identity-174795142.html
Data and cyber security threat concept. Online financial crime, identity theft and internet scam. Laptop computer keyboard in spotlight. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-data-and-cyber-security-threat-concept-online-financial-crime-identity-174795142.htmlRFM4AGYJ–Data and cyber security threat concept. Online financial crime, identity theft and internet scam. Laptop computer keyboard in spotlight.
 A wasp spider in a large web on a background of green grass on a sunny day. Argiope bruennichi. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/a-wasp-spider-in-a-large-web-on-a-background-of-green-grass-on-a-sunny-day-argiope-bruennichi-image562027552.html
A wasp spider in a large web on a background of green grass on a sunny day. Argiope bruennichi. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/a-wasp-spider-in-a-large-web-on-a-background-of-green-grass-on-a-sunny-day-argiope-bruennichi-image562027552.htmlRF2RJAFTG–A wasp spider in a large web on a background of green grass on a sunny day. Argiope bruennichi.
 Danger cloudy sky. Dark red black background. Threat of military conflict Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/danger-cloudy-sky-dark-red-black-background-threat-of-military-conflict-image342118913.html
Danger cloudy sky. Dark red black background. Threat of military conflict Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/danger-cloudy-sky-dark-red-black-background-threat-of-military-conflict-image342118913.htmlRF2ATGT4H–Danger cloudy sky. Dark red black background. Threat of military conflict
 Vector set of vertical web banners with digital marketing, experience and safety communication, protection email marketing.Vector banner template for Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/vector-set-of-vertical-web-banners-with-digital-marketing-experience-and-safety-communication-protection-email-marketingvector-banner-template-for-image244861574.html
Vector set of vertical web banners with digital marketing, experience and safety communication, protection email marketing.Vector banner template for Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/vector-set-of-vertical-web-banners-with-digital-marketing-experience-and-safety-communication-protection-email-marketingvector-banner-template-for-image244861574.htmlRFT6ABC6–Vector set of vertical web banners with digital marketing, experience and safety communication, protection email marketing.Vector banner template for
 Neon letters spelling VIRUS DETECTED hover over cityscape at night Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/neon-letters-spelling-virus-detected-hover-over-cityscape-at-night-image607598006.html
Neon letters spelling VIRUS DETECTED hover over cityscape at night Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/neon-letters-spelling-virus-detected-hover-over-cityscape-at-night-image607598006.htmlRF2X8EDCP–Neon letters spelling VIRUS DETECTED hover over cityscape at night
RFR5M002–Computer virus black icon, vector sign on isolated background. Computer virus concept symbol, illustration
 Web banking Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/web-banking-image343624497.html
Web banking Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/web-banking-image343624497.htmlRM2AY1CFD–Web banking
 Threat text on ripped paper Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/threat-text-on-ripped-paper-image483626095.html
Threat text on ripped paper Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/threat-text-on-ripped-paper-image483626095.htmlRF2K2R20F–Threat text on ripped paper
 Dirty data concept on rotating sphere Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/dirty-data-concept-on-rotating-sphere-image483550426.html
Dirty data concept on rotating sphere Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/dirty-data-concept-on-rotating-sphere-image483550426.htmlRF2K2KHE2–Dirty data concept on rotating sphere
 Hacked monitor. Ransomware. Binary digital numbers on red screen with ransom word on screen. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-image-hacked-monitor-ransomware-binary-digital-numbers-on-red-screen-with-164670610.html
Hacked monitor. Ransomware. Binary digital numbers on red screen with ransom word on screen. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-image-hacked-monitor-ransomware-binary-digital-numbers-on-red-screen-with-164670610.htmlRFKFWB16–Hacked monitor. Ransomware. Binary digital numbers on red screen with ransom word on screen.
 Computer hacker testing cyber security Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/computer-hacker-testing-cyber-security-image434864930.html
Computer hacker testing cyber security Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/computer-hacker-testing-cyber-security-image434864930.htmlRF2G7DPJA–Computer hacker testing cyber security
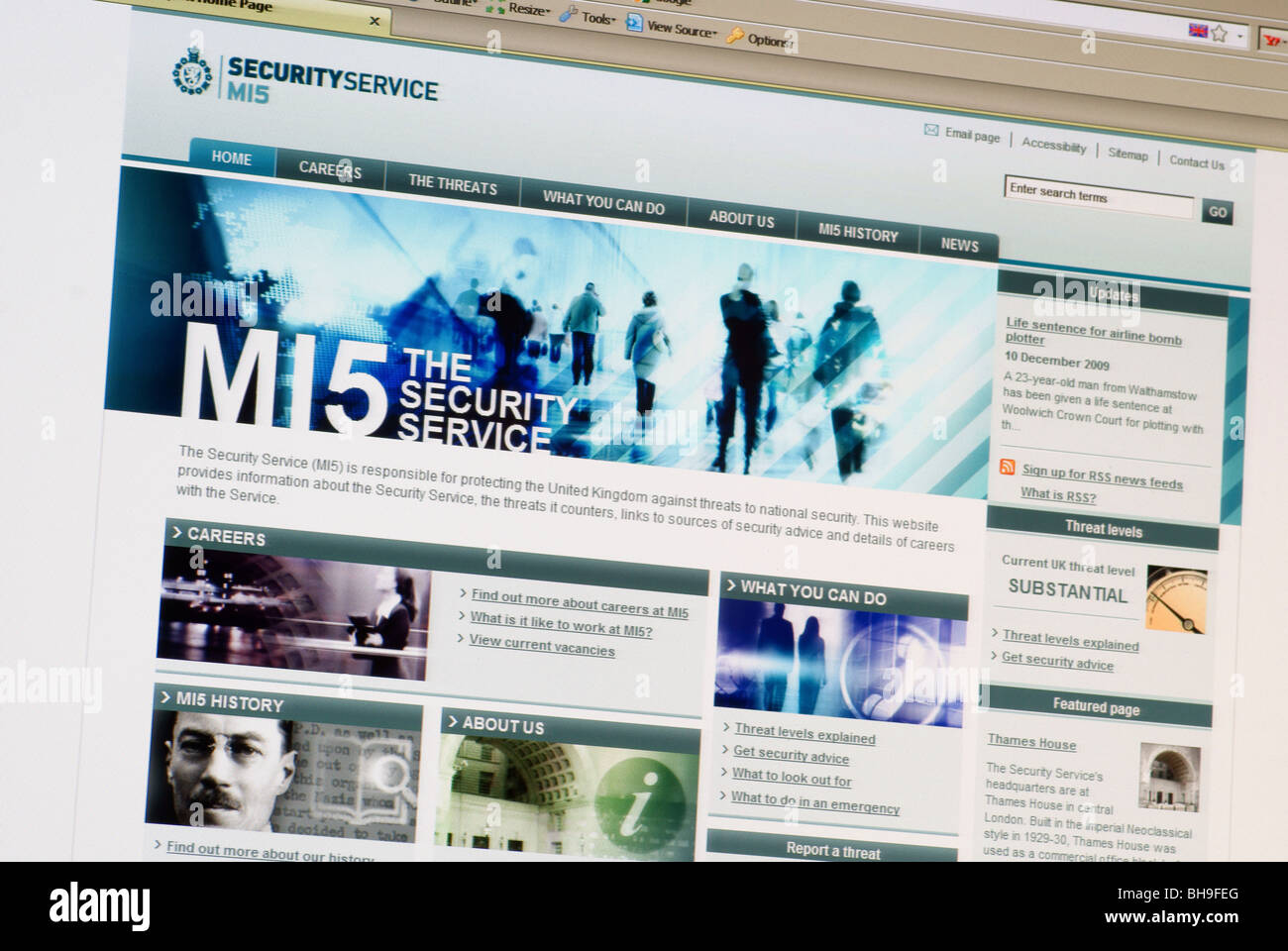 Macro screen shot of MI5 web site home page Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-macro-screen-shot-of-mi5-web-site-home-page-27869256.html
Macro screen shot of MI5 web site home page Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-macro-screen-shot-of-mi5-web-site-home-page-27869256.htmlRMBH9FEG–Macro screen shot of MI5 web site home page
 Argiope ansuja spider resting on its web Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/argiope-ansuja-spider-resting-on-its-web-image604465966.html
Argiope ansuja spider resting on its web Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/argiope-ansuja-spider-resting-on-its-web-image604465966.htmlRF2X3BPE6–Argiope ansuja spider resting on its web
 Warning Problem Spam Threat Online Website Concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-warning-problem-spam-threat-online-website-concept-126088471.html
Warning Problem Spam Threat Online Website Concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-warning-problem-spam-threat-online-website-concept-126088471.htmlRFH93R3K–Warning Problem Spam Threat Online Website Concept
 Large web stretched in the pantry, in the center of which sits a large spider. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/large-web-stretched-in-the-pantry-in-the-center-of-which-sits-a-large-spider-image214768008.html
Large web stretched in the pantry, in the center of which sits a large spider. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/large-web-stretched-in-the-pantry-in-the-center-of-which-sits-a-large-spider-image214768008.htmlRFPDBEP0–Large web stretched in the pantry, in the center of which sits a large spider.
 Spider climbing up to the fly he caught in the web Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/spider-climbing-up-to-the-fly-he-caught-in-the-web-image228883003.html
Spider climbing up to the fly he caught in the web Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/spider-climbing-up-to-the-fly-he-caught-in-the-web-image228883003.htmlRFR8AEGY–Spider climbing up to the fly he caught in the web
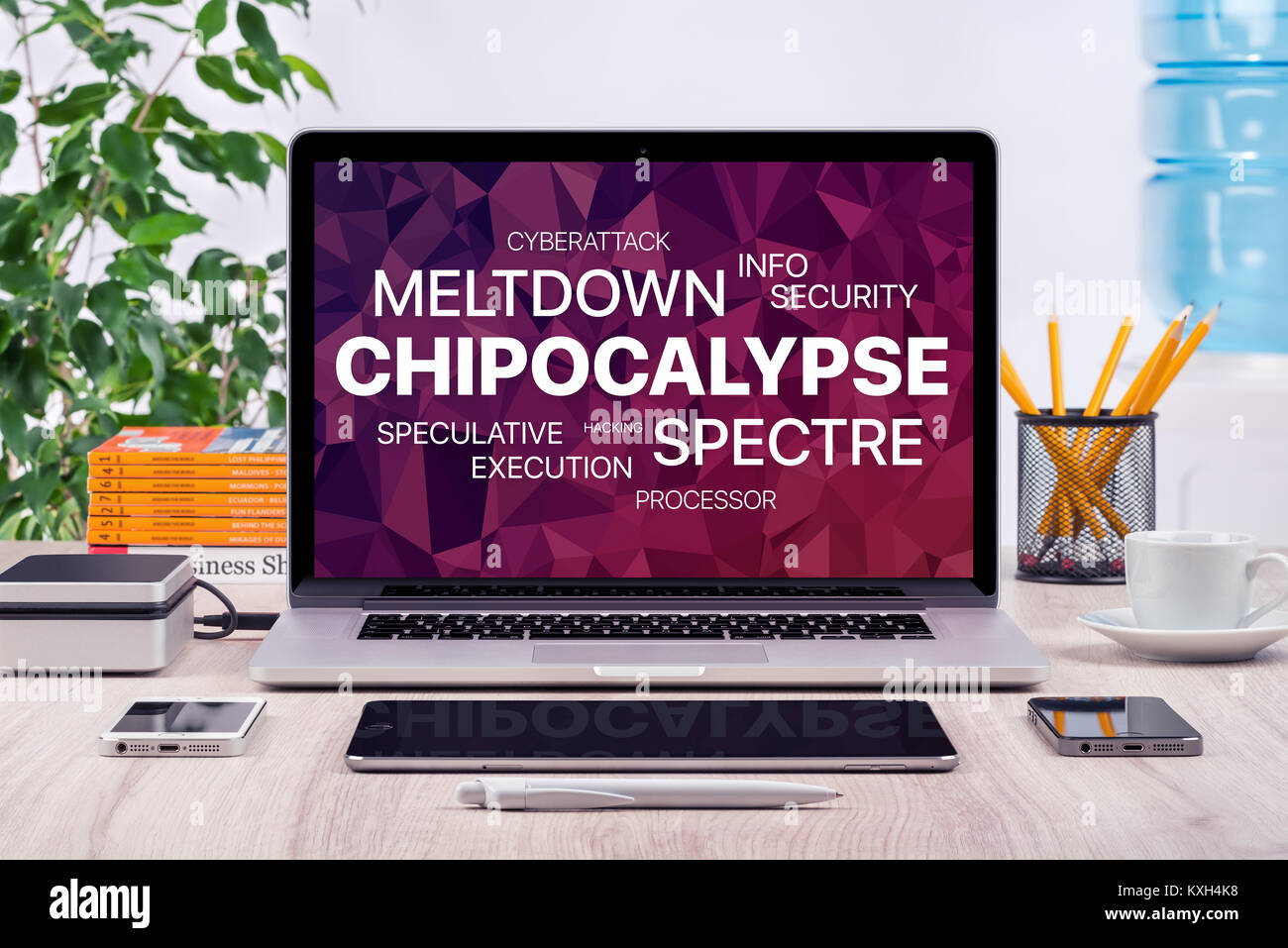 Chipocalypse concept with meltdown and spectre threat on laptop screen in office. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-chipocalypse-concept-with-meltdown-and-spectre-threat-on-laptop-screen-171251228.html
Chipocalypse concept with meltdown and spectre threat on laptop screen in office. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-chipocalypse-concept-with-meltdown-and-spectre-threat-on-laptop-screen-171251228.htmlRFKXH4K8–Chipocalypse concept with meltdown and spectre threat on laptop screen in office.
 Update vehicle accident television news banner. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/update-vehicle-accident-television-news-banner-image550899188.html
Update vehicle accident television news banner. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/update-vehicle-accident-television-news-banner-image550899188.htmlRF2R07HF0–Update vehicle accident television news banner.
 Inspiration showing sign Insider Threat. Business concept security threat that originates from within the organization Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/inspiration-showing-sign-insider-threat-business-concept-security-threat-that-originates-from-within-the-organization-image547486739.html
Inspiration showing sign Insider Threat. Business concept security threat that originates from within the organization Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/inspiration-showing-sign-insider-threat-business-concept-security-threat-that-originates-from-within-the-organization-image547486739.htmlRM2PPM4WR–Inspiration showing sign Insider Threat. Business concept security threat that originates from within the organization
 Laptop in web with gun and knife nternet data password security protection Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-image-laptop-in-web-with-gun-and-knife-nternet-data-password-security-protection-166175994.html
Laptop in web with gun and knife nternet data password security protection Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-image-laptop-in-web-with-gun-and-knife-nternet-data-password-security-protection-166175994.htmlRFKJ9Y4X–Laptop in web with gun and knife nternet data password security protection
RF2JPBTNX–threat line icon, outline symbol, vector illustration, concept sign
 Human skull on danger cloudy sky. Dark red black background. Threat of military conflict Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/human-skull-on-danger-cloudy-sky-dark-red-black-background-threat-of-military-conflict-image383847325.html
Human skull on danger cloudy sky. Dark red black background. Threat of military conflict Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/human-skull-on-danger-cloudy-sky-dark-red-black-background-threat-of-military-conflict-image383847325.htmlRF2D8DN51–Human skull on danger cloudy sky. Dark red black background. Threat of military conflict
 Email protection and secure communication on internet. Antivirus for protection, security and blocking of spam. Template in flat design for web banner Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/email-protection-and-secure-communication-on-internet-antivirus-for-protection-security-and-blocking-of-spam-template-in-flat-design-for-web-banner-image240274653.html
Email protection and secure communication on internet. Antivirus for protection, security and blocking of spam. Template in flat design for web banner Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/email-protection-and-secure-communication-on-internet-antivirus-for-protection-security-and-blocking-of-spam-template-in-flat-design-for-web-banner-image240274653.htmlRFRXWCNH–Email protection and secure communication on internet. Antivirus for protection, security and blocking of spam. Template in flat design for web banner
 Hand with mouse hovers over screen displaying cybersecurity threats Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/hand-with-mouse-hovers-over-screen-displaying-cybersecurity-threats-image607598013.html
Hand with mouse hovers over screen displaying cybersecurity threats Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/hand-with-mouse-hovers-over-screen-displaying-cybersecurity-threats-image607598013.htmlRF2X8EDD1–Hand with mouse hovers over screen displaying cybersecurity threats
 close up of spider and web against a blurred backdrop of a garden maze in Betanzos Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-close-up-of-spider-and-web-against-a-blurred-backdrop-of-a-garden-112995443.html
close up of spider and web against a blurred backdrop of a garden maze in Betanzos Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-close-up-of-spider-and-web-against-a-blurred-backdrop-of-a-garden-112995443.htmlRMGFRARF–close up of spider and web against a blurred backdrop of a garden maze in Betanzos
 Web banking Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/web-banking-image343624496.html
Web banking Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/web-banking-image343624496.htmlRM2AY1CFC–Web banking
 Scam on the web concept. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/scam-on-the-web-concept-image483583143.html
Scam on the web concept. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/scam-on-the-web-concept-image483583143.htmlRF2K2N36F–Scam on the web concept.
 Driving through the data migration tunnel Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/driving-through-the-data-migration-tunnel-image483550292.html
Driving through the data migration tunnel Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/driving-through-the-data-migration-tunnel-image483550292.htmlRF2K2KH98–Driving through the data migration tunnel
 Hacked monitor. Ransomware. Binary digital numbers on red screen with ransom word on screen. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-image-hacked-monitor-ransomware-binary-digital-numbers-on-red-screen-with-164670693.html
Hacked monitor. Ransomware. Binary digital numbers on red screen with ransom word on screen. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-image-hacked-monitor-ransomware-binary-digital-numbers-on-red-screen-with-164670693.htmlRFKFWB45–Hacked monitor. Ransomware. Binary digital numbers on red screen with ransom word on screen.
 Computer hacker testing cyber security Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/computer-hacker-testing-cyber-security-image434864931.html
Computer hacker testing cyber security Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/computer-hacker-testing-cyber-security-image434864931.htmlRF2G7DPJB–Computer hacker testing cyber security
 Macro screen shot of MI5 web site careers page Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-macro-screen-shot-of-mi5-web-site-careers-page-27867850.html
Macro screen shot of MI5 web site careers page Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-macro-screen-shot-of-mi5-web-site-careers-page-27867850.htmlRMBH9DMA–Macro screen shot of MI5 web site careers page
 Argiope ansuja spider resting on its web Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/argiope-ansuja-spider-resting-on-its-web-image604465914.html
Argiope ansuja spider resting on its web Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/argiope-ansuja-spider-resting-on-its-web-image604465914.htmlRF2X3BPCA–Argiope ansuja spider resting on its web
 Warning Problem Spam Threat Online Website Concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-warning-problem-spam-threat-online-website-concept-126088469.html
Warning Problem Spam Threat Online Website Concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-warning-problem-spam-threat-online-website-concept-126088469.htmlRFH93R3H–Warning Problem Spam Threat Online Website Concept
RF2HNGB0N–Backdoor Simple vector icon. Illustration symbol design template for web mobile UI element.
 A brown and black spider hanging on a web in front of a red wall Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/a-brown-and-black-spider-hanging-on-a-web-in-front-of-a-red-wall-image351388313.html
A brown and black spider hanging on a web in front of a red wall Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/a-brown-and-black-spider-hanging-on-a-web-in-front-of-a-red-wall-image351388313.htmlRF2BBK3AH–A brown and black spider hanging on a web in front of a red wall
 Meltdown and spectre threat concept on laptop screen in office workplace. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-meltdown-and-spectre-threat-concept-on-laptop-screen-in-office-workplace-171251137.html
Meltdown and spectre threat concept on laptop screen in office workplace. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-meltdown-and-spectre-threat-concept-on-laptop-screen-in-office-workplace-171251137.htmlRFKXH4G1–Meltdown and spectre threat concept on laptop screen in office workplace.
 Hooded and masked computer hacker thief with a cloud computer based background. Unknown technology threat to the cloud mainframe Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-hooded-and-masked-computer-hacker-thief-with-a-cloud-computer-based-105114280.html
Hooded and masked computer hacker thief with a cloud computer based background. Unknown technology threat to the cloud mainframe Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-hooded-and-masked-computer-hacker-thief-with-a-cloud-computer-based-105114280.htmlRFG30A9C–Hooded and masked computer hacker thief with a cloud computer based background. Unknown technology threat to the cloud mainframe
 Text showing inspiration Insider Threat. Word Written on security threat that originates from within the organization Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/text-showing-inspiration-insider-threat-word-written-on-security-threat-that-originates-from-within-the-organization-image547448139.html
Text showing inspiration Insider Threat. Word Written on security threat that originates from within the organization Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/text-showing-inspiration-insider-threat-word-written-on-security-threat-that-originates-from-within-the-organization-image547448139.htmlRM2PPJBK7–Text showing inspiration Insider Threat. Word Written on security threat that originates from within the organization
 Laptop in web with gun and knife nternet data password security protection Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-image-laptop-in-web-with-gun-and-knife-nternet-data-password-security-protection-166175992.html
Laptop in web with gun and knife nternet data password security protection Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-image-laptop-in-web-with-gun-and-knife-nternet-data-password-security-protection-166175992.htmlRFKJ9Y4T–Laptop in web with gun and knife nternet data password security protection
RF2JP6T1R–email virus threat line icon, outline symbol, vector illustration, concept sign
 Human skull on danger cloudy sky. Dark red black background. Threat of military conflict Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/human-skull-on-danger-cloudy-sky-dark-red-black-background-threat-of-military-conflict-image342142931.html
Human skull on danger cloudy sky. Dark red black background. Threat of military conflict Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/human-skull-on-danger-cloudy-sky-dark-red-black-background-threat-of-military-conflict-image342142931.htmlRF2ATHXPB–Human skull on danger cloudy sky. Dark red black background. Threat of military conflict
 Antivirus for protection, security and blocking spam. Protect of privacy, virus and phishing. Template in flat design for web banner or infographic i Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/antivirus-for-protection-security-and-blocking-spam-protect-of-privacy-virus-and-phishing-template-in-flat-design-for-web-banner-or-infographic-i-image240274654.html
Antivirus for protection, security and blocking spam. Protect of privacy, virus and phishing. Template in flat design for web banner or infographic i Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/antivirus-for-protection-security-and-blocking-spam-protect-of-privacy-virus-and-phishing-template-in-flat-design-for-web-banner-or-infographic-i-image240274654.htmlRFRXWCNJ–Antivirus for protection, security and blocking spam. Protect of privacy, virus and phishing. Template in flat design for web banner or infographic i
 Image of padlock, connections and data processing over dark background Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/image-of-padlock-connections-and-data-processing-over-dark-background-image607603218.html
Image of padlock, connections and data processing over dark background Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/image-of-padlock-connections-and-data-processing-over-dark-background-image607603218.htmlRF2X8EM2X–Image of padlock, connections and data processing over dark background
 Computer Virus Illustration Concept. Modern design concept of web page design for website and mobile website.Vector illustration EPS 10 Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/computer-virus-illustration-concept-modern-design-concept-of-web-page-design-for-website-and-mobile-websitevector-illustration-eps-10-image259496782.html
Computer Virus Illustration Concept. Modern design concept of web page design for website and mobile website.Vector illustration EPS 10 Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/computer-virus-illustration-concept-modern-design-concept-of-web-page-design-for-website-and-mobile-websitevector-illustration-eps-10-image259496782.htmlRFW252P6–Computer Virus Illustration Concept. Modern design concept of web page design for website and mobile website.Vector illustration EPS 10
 global connection web Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/global-connection-web-image369813009.html
global connection web Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/global-connection-web-image369813009.htmlRM2CDJC7D–global connection web
 Scam on the web concept. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/scam-on-the-web-concept-image483583145.html
Scam on the web concept. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/scam-on-the-web-concept-image483583145.htmlRF2K2N36H–Scam on the web concept.
 Driving through the data transmission tunnel Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/driving-through-the-data-transmission-tunnel-image483515844.html
Driving through the data transmission tunnel Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/driving-through-the-data-transmission-tunnel-image483515844.htmlRF2K2J1B0–Driving through the data transmission tunnel
 Hacked monitor. Ransomware. Binary digital numbers on red screen with ransom word on screen. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-image-hacked-monitor-ransomware-binary-digital-numbers-on-red-screen-with-164670634.html
Hacked monitor. Ransomware. Binary digital numbers on red screen with ransom word on screen. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-image-hacked-monitor-ransomware-binary-digital-numbers-on-red-screen-with-164670634.htmlRFKFWB22–Hacked monitor. Ransomware. Binary digital numbers on red screen with ransom word on screen.
 Internet Security Hackers Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/internet-security-hackers-image447889783.html
Internet Security Hackers Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/internet-security-hackers-image447889783.htmlRF2H0K3YK–Internet Security Hackers
 A young man at a computer and an online fraudster. Phishing, Scam, hacker attack and web security concept. Online Scam and theft Vector illustration Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/a-young-man-at-a-computer-and-an-online-fraudster-phishing-scam-hacker-attack-and-web-security-concept-online-scam-and-theft-vector-illustration-image381607710.html
A young man at a computer and an online fraudster. Phishing, Scam, hacker attack and web security concept. Online Scam and theft Vector illustration Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/a-young-man-at-a-computer-and-an-online-fraudster-phishing-scam-hacker-attack-and-web-security-concept-online-scam-and-theft-vector-illustration-image381607710.htmlRF2D4RMEP–A young man at a computer and an online fraudster. Phishing, Scam, hacker attack and web security concept. Online Scam and theft Vector illustration
 A wasp spider in a large web on a background of green grass on a sunny day. Argiope bruennichi. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/a-wasp-spider-in-a-large-web-on-a-background-of-green-grass-on-a-sunny-day-argiope-bruennichi-image544681336.html
A wasp spider in a large web on a background of green grass on a sunny day. Argiope bruennichi. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/a-wasp-spider-in-a-large-web-on-a-background-of-green-grass-on-a-sunny-day-argiope-bruennichi-image544681336.htmlRF2PJ4AGT–A wasp spider in a large web on a background of green grass on a sunny day. Argiope bruennichi.
 Warning Problem Spam Threat Online Website Concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-warning-problem-spam-threat-online-website-concept-126088472.html
Warning Problem Spam Threat Online Website Concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-warning-problem-spam-threat-online-website-concept-126088472.htmlRFH93R3M–Warning Problem Spam Threat Online Website Concept
RF2HN99TK–Backdoor Simple vector icon. Illustration symbol design template for web mobile UI element.
 Smart healthcare vector landing page template. Innovation ody diagnostics website design layout. Modern treatment methods web page concept. Medical clinic, research institute webpage interface Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/smart-healthcare-vector-landing-page-template-innovation-ody-diagnostics-website-design-layout-modern-treatment-methods-web-page-concept-medical-clinic-research-institute-webpage-interface-image366243773.html
Smart healthcare vector landing page template. Innovation ody diagnostics website design layout. Modern treatment methods web page concept. Medical clinic, research institute webpage interface Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/smart-healthcare-vector-landing-page-template-innovation-ody-diagnostics-website-design-layout-modern-treatment-methods-web-page-concept-medical-clinic-research-institute-webpage-interface-image366243773.htmlRF2C7RRJN–Smart healthcare vector landing page template. Innovation ody diagnostics website design layout. Modern treatment methods web page concept. Medical clinic, research institute webpage interface
 Meltdown and spectre threat concept on laptop screen on ultraviolet polygonal background. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-meltdown-and-spectre-threat-concept-on-laptop-screen-on-ultraviolet-171958934.html
Meltdown and spectre threat concept on laptop screen on ultraviolet polygonal background. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-meltdown-and-spectre-threat-concept-on-laptop-screen-on-ultraviolet-171958934.htmlRFKYNBAE–Meltdown and spectre threat concept on laptop screen on ultraviolet polygonal background.
 Hooded and masked computer hacker thief with a cloud computer based background and binary code. Unknown technology threat to the Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-hooded-and-masked-computer-hacker-thief-with-a-cloud-computer-based-105114402.html
Hooded and masked computer hacker thief with a cloud computer based background and binary code. Unknown technology threat to the Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-hooded-and-masked-computer-hacker-thief-with-a-cloud-computer-based-105114402.htmlRFG30ADP–Hooded and masked computer hacker thief with a cloud computer based background and binary code. Unknown technology threat to the
RF2A9CJRN–Global cyber attack around the world with planet Earth viewed from space and internet network communication under cyberattack with red icons, worldwid